This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies.
The Joint Corp. (JYNT) Q1 2025 Earnings Call ...
May 10, 2025 0
Trend Micro Incorporated (TMICY) Q1 2025 Earn...
May 10, 2025 0
The Joint Corp. (JYNT) Q1 2025 Earnings Call ...
May 10, 2025 0
Trend Micro Incorporated (TMICY) Q1 2025 Earn...
May 10, 2025 0










































































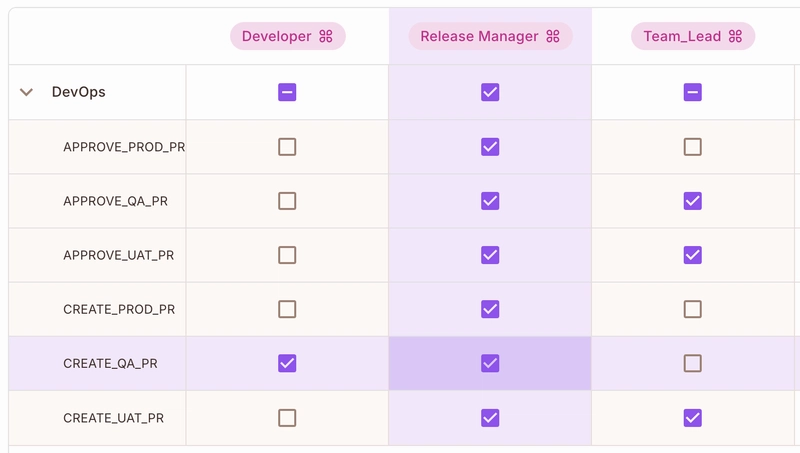

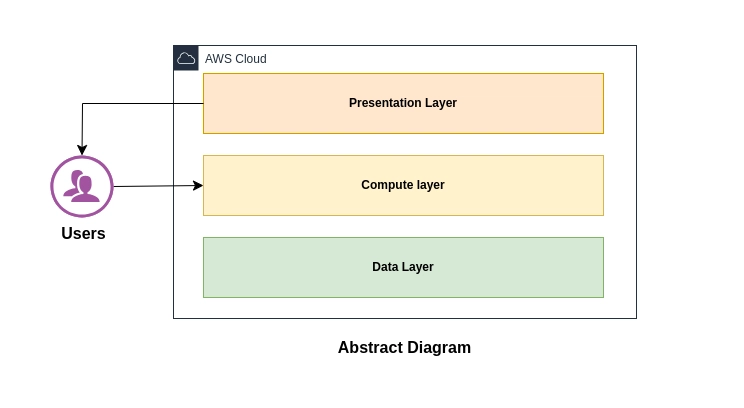


![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)




