CVE-2025-29927 Authorization Bypass in Next.js Middleware
CVE-2025-29927 Authorization Bypass in Next.js Middleware On Friday morning, March 21, 2025, at 9:00 a.m. UTC, a security advisory identified as CVE-2025-29927 was published. It cited a critical 9.1 severity vulnerability for mainstream Next.js applications. Next.js versions considered vulnerable: Next.js 15.x versions before15.2.3 Next.js 14.x versions before 14.2.25 Next.js 13.x versions before 13.5.9 All Next.js versions until the fixed Next.js 13.5.9 are considered vulnerable, but Vercel’s vulnerability announcement noted a possible upcoming workaround or fix backport to be released. We urge all developers to upgrade and deploy the latest version of Next.js that carries a fix to avoid suffering critical authorization bypass and other middleware logic circumvention. Impact scope of CVE-2025-29927 Vercel announced that this vulnerability does not impact applications hosted on the Vercel hosting platform. Netlify, another popular web hosting platform, announced that this vulnerability does not impact applications deployed to Netlify. Cloudflare, often used as a CDN but also capable of hosting Next.js applications, allows developers to turn on a managed WAF rule as an opt-in workaround. About Next.js Middleware Next.js middleware concept is borrowed from the Express web application framework. The idea of middleware is an HTTP predicate that can decorate, reroute, and decide how an incoming HTTP request to a Node.js server will behave. The Next.js middleware definition follows a similar function signature to that of Express, receiving an HTTP request object (NextRequest) and returning a NextResponse to force a specific behavior such as returning a 401 Unauthorized HTTP response, an HTTP redirect or allowing the request handling logic to proceed via a NextResponse.next() directive. export function middleware(req: NextRequest) { const token = req.cookies.get("auth-token")?.value; // Define protected routes const protectedRoutes = ["/admin"]; if (protectedRoutes.some((route) => req.nextUrl.pathname.startsWith(route))) { if (!token) { // Redirect to login page if not authorized const loginUrl = new URL("/login", req.nextUrl.origin); return NextResponse.redirect(loginUrl); } } // Allow request to proceed return NextResponse.next(); } As mentioned in the official Next.js documentation, developers often use middleware to perform authentication and authorization decisions, such as validating a cookie or a JWT in the request before allowing access to gated and protected routes. Authorization Bypass in Next.js Security researchers Allam Rachid and Allam Yasser, who studied and reported this vulnerability (and past Next.js vulnerabilities), have shown how external clients can bypass the middleware logic when issuing requests to protected routes managed by Next.js via the middleware. Bypassing the middleware requires clients to specify the following HTTP header to requests: x-middleware-subrequest: middleware The Next.js logic manages the x-middleware-subrequest HTTP header to decide how and when to allow requests to pass through without going through the middleware logic, avoiding infinite loops. However, said logic is faulty in the aforementioned vulnerable versions of Next.js and allows any incoming request to a Next.js server to bypass if the x-middleware-subrequest HTTP header is present with a specific value. Note for reproduction that the exact HTTP header value varies and depends on your version of Next.js. Am I affected by CVE-2025-29927 Next.js Authorization Bypass? Developers who use Snyk Open Source to detect dependency vulnerabilities in their IDE, Git SCM, CI, or Snyk’s monitoring workflow will be alerted to CVE-2025-29927 as shown in this GitHub repository imported to Snyk projects: The vulnerability details for Next.js at Snyk provide an upgrade path (e.g: next@14.2.25, like in my case) and Snyk users can also quickly fix the vulnerability with a click of a button (or choose to automate it altogether): You are likely affected and vulnerable to an authorization bypass in Next.js if: You’re running Next.js versions 11.1.4 to 13.5.6 You’re self-hosting vulnerable Next.js versions (14.x < 14.2.25 or 15.x < 15.2.3) Remediating the CVE-2025-29927 and Workarounds Fixes or remediation are available, depending on which versions of Next.js you are using and where you are deploying them: Upgrade to a fixed Next.js version using the latest 14.x or 15.x version branches. Apply a firewall rule that prevents external HTTP requests with the header x-middleware-subrequest from reaching the internal Next.js application infrastructure. Deployments to Vercel and Netlify are unaffected, as these cloud hosting platforms stated
CVE-2025-29927 Authorization Bypass in Next.js Middleware
On Friday morning, March 21, 2025, at 9:00 a.m. UTC, a security advisory identified as CVE-2025-29927 was published. It cited a critical 9.1 severity vulnerability for mainstream Next.js applications.
Next.js versions considered vulnerable:
- Next.js 15.x versions before15.2.3
- Next.js 14.x versions before 14.2.25
- Next.js 13.x versions before 13.5.9
- All Next.js versions until the fixed Next.js 13.5.9 are considered vulnerable, but Vercel’s vulnerability announcement noted a possible upcoming workaround or fix backport to be released.
We urge all developers to upgrade and deploy the latest version of Next.js that carries a fix to avoid suffering critical authorization bypass and other middleware logic circumvention.
Impact scope of CVE-2025-29927
Vercel announced that this vulnerability does not impact applications hosted on the Vercel hosting platform.
Netlify, another popular web hosting platform, announced that this vulnerability does not impact applications deployed to Netlify.
Cloudflare, often used as a CDN but also capable of hosting Next.js applications, allows developers to turn on a managed WAF rule as an opt-in workaround.
About Next.js Middleware
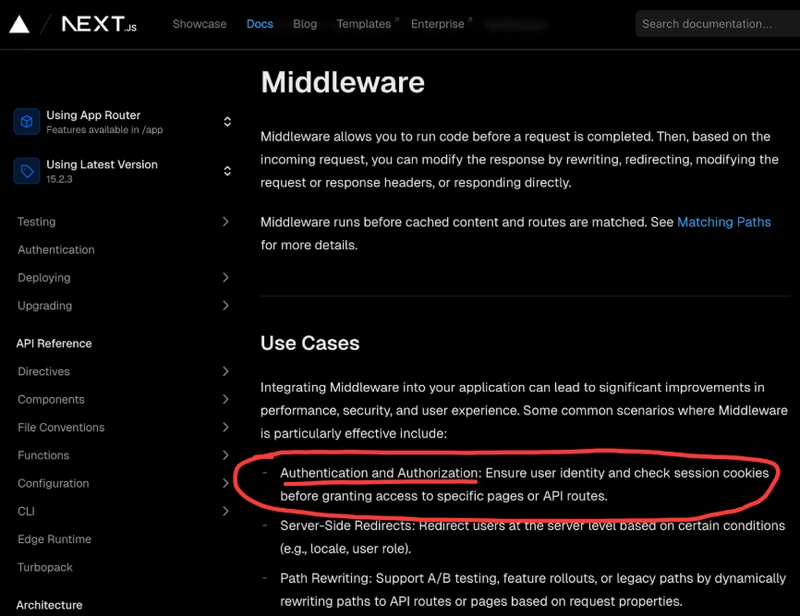
Next.js middleware concept is borrowed from the Express web application framework. The idea of middleware is an HTTP predicate that can decorate, reroute, and decide how an incoming HTTP request to a Node.js server will behave.
The Next.js middleware definition follows a similar function signature to that of Express, receiving an HTTP request object (NextRequest) and returning a NextResponse to force a specific behavior such as returning a 401 Unauthorized HTTP response, an HTTP redirect or allowing the request handling logic to proceed via a NextResponse.next() directive.
export function middleware(req: NextRequest) {
const token = req.cookies.get("auth-token")?.value;
// Define protected routes
const protectedRoutes = ["/admin"];
if (protectedRoutes.some((route) => req.nextUrl.pathname.startsWith(route))) {
if (!token) {
// Redirect to login page if not authorized
const loginUrl = new URL("/login", req.nextUrl.origin);
return NextResponse.redirect(loginUrl);
}
}
// Allow request to proceed
return NextResponse.next();
}
As mentioned in the official Next.js documentation, developers often use middleware to perform authentication and authorization decisions, such as validating a cookie or a JWT in the request before allowing access to gated and protected routes.
Authorization Bypass in Next.js
Security researchers Allam Rachid and Allam Yasser, who studied and reported this vulnerability (and past Next.js vulnerabilities), have shown how external clients can bypass the middleware logic when issuing requests to protected routes managed by Next.js via the middleware.
Bypassing the middleware requires clients to specify the following HTTP header to requests:
x-middleware-subrequest: middleware
The Next.js logic manages the x-middleware-subrequest HTTP header to decide how and when to allow requests to pass through without going through the middleware logic, avoiding infinite loops. However, said logic is faulty in the aforementioned vulnerable versions of Next.js and allows any incoming request to a Next.js server to bypass if the x-middleware-subrequest HTTP header is present with a specific value.
Note for reproduction that the exact HTTP header value varies and depends on your version of Next.js.
Am I affected by CVE-2025-29927 Next.js Authorization Bypass?
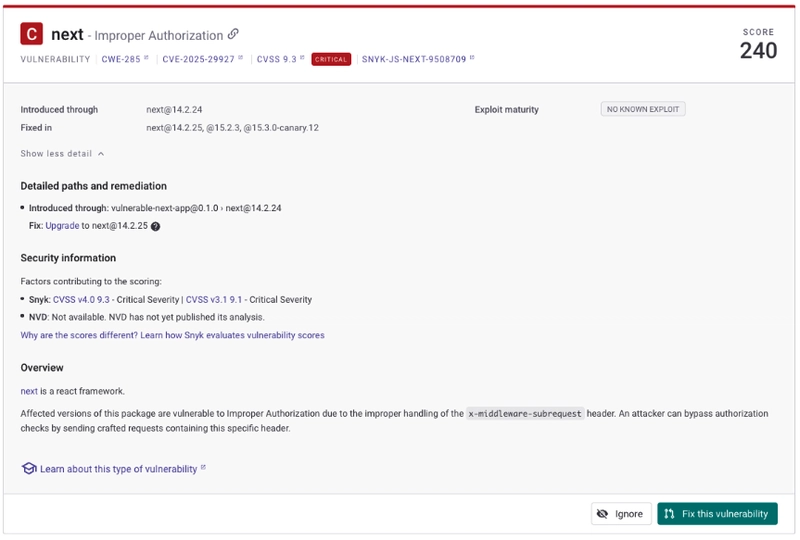
Developers who use Snyk Open Source to detect dependency vulnerabilities in their IDE, Git SCM, CI, or Snyk’s monitoring workflow will be alerted to CVE-2025-29927 as shown in this GitHub repository imported to Snyk projects:
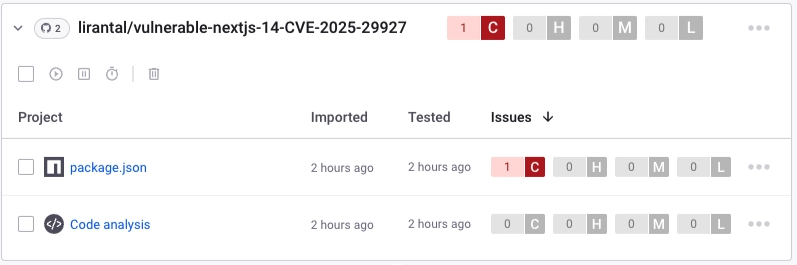
The vulnerability details for Next.js at Snyk provide an upgrade path (e.g: next@14.2.25, like in my case) and Snyk users can also quickly fix the vulnerability with a click of a button (or choose to automate it altogether):
You are likely affected and vulnerable to an authorization bypass in Next.js if:
- You’re running Next.js versions 11.1.4 to 13.5.6
- You’re self-hosting vulnerable Next.js versions (14.x < 14.2.25 or 15.x < 15.2.3)
Remediating the CVE-2025-29927 and Workarounds
Fixes or remediation are available, depending on which versions of Next.js you are using and where you are deploying them:
- Upgrade to a fixed Next.js version using the latest 14.x or 15.x version branches.
- Apply a firewall rule that prevents external HTTP requests with the header x-middleware-subrequest from reaching the internal Next.js application infrastructure.
- Deployments to Vercel and Netlify are unaffected, as these cloud hosting platforms stated