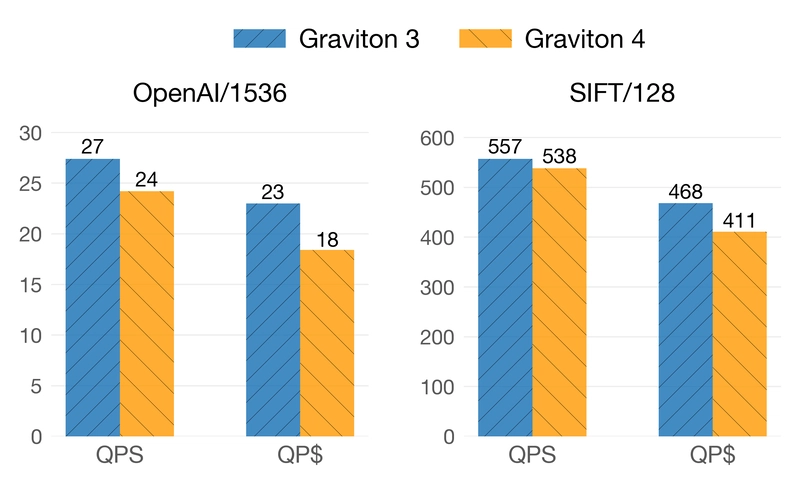
Putting Azure APIM in front of your Service Bus queue
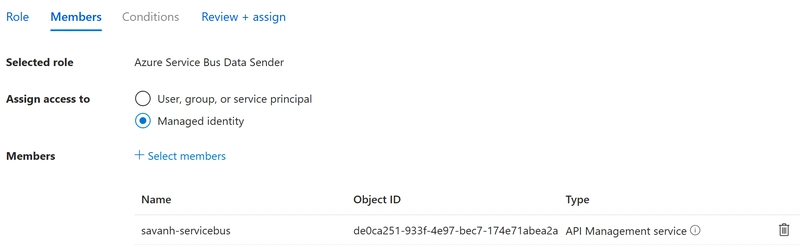
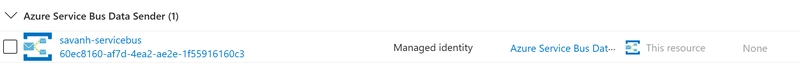
For a specific scenario, we wanted to expose a queuing endpoint towards a customer, in a secure way, but at the same time abstracting our internal usage of Azure Service Bus. As we already had Azure API Management in place to expose our API, we decided to leverage this and see if we could avoid the typical scenario where we'd have to develop a strong typed custom API that then just takes the incoming request and maps it to a Service Bus message that should be be processed to the right endpoint. And this post describes exactly how you can achieve this. Azure API Management policy The following abstract is the full policy that we configured. So, you could see this as the "tldr;" of this blog post. In the rest of the article, we'll dive deeper in the details and discuss what's behind everything. TODO Set up the API operation contract As we want to have a strong typed operation, enforcing the contract, we have to define both the actual operation (http resource) as well as the incoming payload schema first. In the following screenshot, you can see we define the resource (POST /order). We also indicate that the operation expects an instance of the definition CreateOrderRequest in the request. The schema itself is defined in the Definitions tab (at the bottom), where you can define the schema itself, or have the schema generated from a sample instance. Enable security and access rights on Service Bus In order to allow the API Management service to send messages to the Azure Service Bus endpoint, it is important to assign the correct permissions. We will do this by providing the Azure Service Bus Data Sender role to the System Identity of Azure API Management. Please verify the System Assigned Identity is enabled on API Management, by navigating to the 'Managed Identities' tab. Take note of the Object (principal) ID. Navigate to your Service Bus namespace in the Azure portal Assign the right permissions in Role Assignments, as shown in the next screenshot The result should be looking like the following The client id of the role should be stored as it will be used in the APIM policy , to authenticate against the API of Servicebus (here: 60ec8160***)
For a specific scenario, we wanted to expose a queuing endpoint towards a customer, in a secure way, but at the same time abstracting our internal usage of Azure Service Bus.
As we already had Azure API Management in place to expose our API, we decided to leverage this and see if we could avoid the typical scenario where we'd have to develop a strong typed custom API that then just takes the incoming request and maps it to a Service Bus message that should be be processed to the right endpoint.
And this post describes exactly how you can achieve this.
Azure API Management policy
The following abstract is the full policy that we configured. So, you could see this as the "tldr;" of this blog post. In the rest of the article, we'll dive deeper in the details and discuss what's behind everything.
TODO
Set up the API operation contract
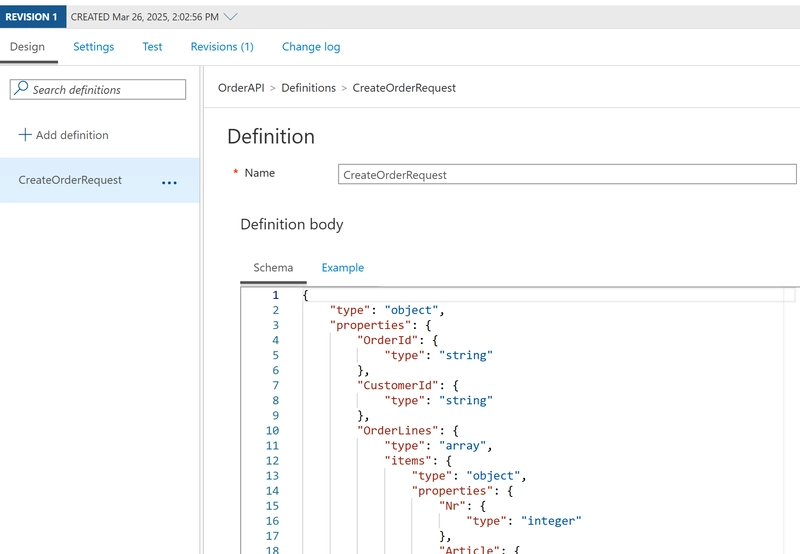
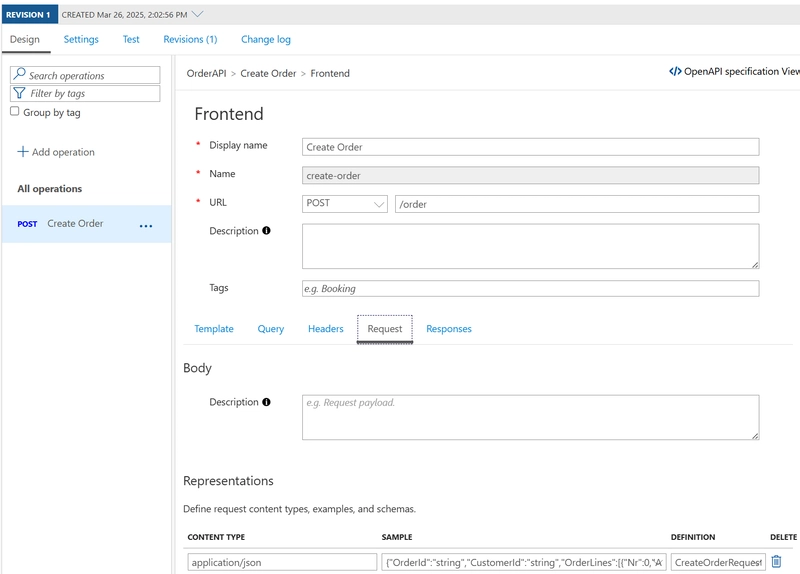
As we want to have a strong typed operation, enforcing the contract, we have to define both the actual operation (http resource) as well as the incoming payload schema first.
In the following screenshot, you can see we define the resource (POST /order). We also indicate that the operation expects an instance of the definition CreateOrderRequest in the request.
The schema itself is defined in the Definitions tab (at the bottom), where you can define the schema itself, or have the schema generated from a sample instance.
Enable security and access rights on Service Bus
In order to allow the API Management service to send messages to the Azure Service Bus endpoint, it is important to assign the correct permissions. We will do this by providing the Azure Service Bus Data Sender role to the System Identity of Azure API Management.
- Please verify the System Assigned Identity is enabled on API Management, by navigating to the 'Managed Identities' tab.
- Take note of the Object (principal) ID.
- Navigate to your Service Bus namespace in the Azure portal
- Assign the right permissions in Role Assignments, as shown in the next screenshot
The result should be looking like the following
The client id of the role should be stored as it will be used in the APIM policy , to authenticate against the API of Servicebus (here: 60ec8160***)