PASTA Threat Modeling Think Like a Hacker to Boost Security
In the world of cybersecurity, knowing how hackers think is one of the best ways to protect your systems. With cyber threats growing more complex every day,
In cybersecurity, understanding how hackers operate is the best way to secure your system. In the world of cyber-attacks that are becoming more sophisticated each day, keeping just one step in front of hackers is essential. PASTA, which stands for Threat Modeling, a Process that enables attack Simulation as well as Threat Analysis is an effective approach to accomplish this. This strategy encourages security personnel to mimic attackers in order that they are able to spot vulnerabilities before attackers do.
In this article we'll explain the details of what PASTA is, how it is effective, and how it can help you think like a hacker in order to safeguard your systems.
What Is PASTA Threat Modeling?
PASTA is a step-bystep method that involves pasta threat modeling threat modelling. It's about analyzing your system from an attack perspective. Instead of merely identifying weaknesses, PASTA allows you to be aware of how hackers could utilize them and the reasons they might use the vulnerabilities. Through hacking your brain, you are capable of better preparing your defenses and safeguard your system from being hacked.
Why Think Like a Hacker?
Hackers aren't randomly attacking you, there isn't a pattern. They look for weaknesses that they can exploit and then typically gain access your data or systems.
If you think about what would be inside their shoes You can predict the location they'll go to attack them.
Here's the reason it does the trick:
Expect attacks: Generally hackers will use a specific method of attacking the system, e.g., finding weaknesses, exploiting vulnerabilities and spreading across the network. After you have figured out this practice it is possible to determine where hackers are most likely to attack first.
Discover Hidden Security Issues Some weaknesses aren't obvious. A hacker could attack an insignificant component of your system, such as an incompatible plugin or a faulty authentication process. Being a hacker in your head can help you identify the hidden dangers.
Prioritize risks The reason is that not all weaknesses are all created in the same way. Hackers seek out the least resistance first. By putting yourself in their position, you can determine the weaknesses that need addressed first in order to avoid attack vectors that could be most vulnerable.
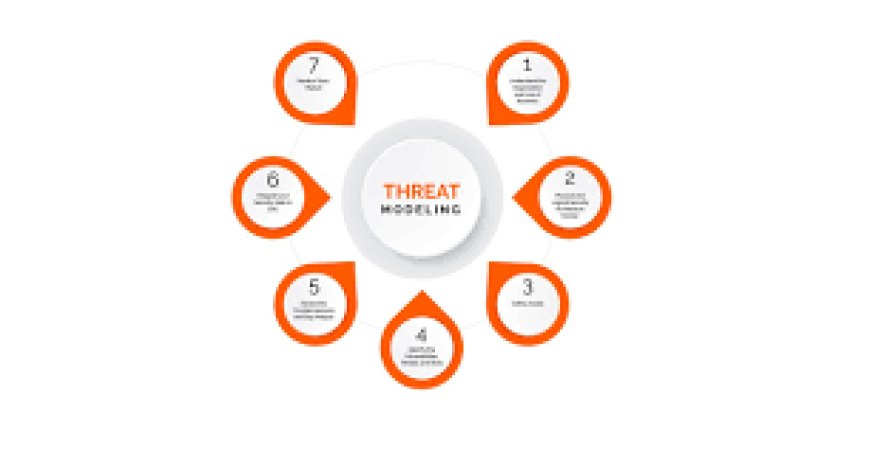
The PASTA Method Step-by-Step
PASTA is a systematic seven-step procedure that guides security personnel in identifying and resolving possible threats. This is how it is implemented:
Define Objectives
Prioritize what is important for your company. This involves identifying your most important assets, including confidential customer information intellectual property, as well as critical services. When you've identified what's the most valuable, you can concentrate on protecting the most crucial aspects in your network.
Define the Technical Scope
Next, consider the design of your system. What is the point of entry (like APIs, web-based applications or networks) that an attacker could be able to exploit? Knowing this is crucial in identifying what vulnerabilities may be present.
Decompose the Application
Break your system down into smaller parts so that you understand how each piece functions. This can help you find areas of weakness within the system, such as unsecure communication channels, or components of software that aren't configured.
Threat Analysis
Let's say we're hackers. Who would you allow to gain access to your system and what would they do? What techniques and tools could they employ? You must investigate the normal threats as well as possible adversaries, i.e., cybercriminals hackers, competitors, or hacktivists. This can reveal the motivations of the attacker.
Vulnerability and Exploit Analysis
You are looking for vulnerabilities in your system that attackers could take advantage of. It is possible to use automated tools, penetration testing and manual scanners in order to discover security holes. This is where being hackers is helpful. You must simulate attacks and determine how easy it could be for someone to gain access to your system.
Risk and Impact Assessment
After you've identified weaknesses, it is important to examine the risks they represent. What weaknesses pose the greatest threats? Which one would be the most dangerous to attack? This way you can classify your vulnerabilities according to the priority that they require attention.
Mitigation and Security Controls
Then, implement solutions to fix the weaknesses you've discovered. This could include updating software, enhancing security measures or adding more levels of protection. The aim is to ensure that your system is as difficult to break as you can.
How PASTA Helps You Think Like a Hacker
PASTA is the word used to describe the state of mind. This is how it can help you think like hackers:
Changes Your Mental State Instead of defending the system you are using, PASTA allows you to think as an attacker. You attempt to discover how to hack your system just as an attacker.
Replicates Actual Attacks: In lieu of making up theories about what could happen, PASTA allows you to play with real-world attacks. It's a hands-on method which helps you see how your system is susceptible to being compromised.
Be aware of the attacker's motives: Hackers don't just hack just because they're able, they hack in order to accomplish something, be it taking data, causing harm, or even making statements. Knowing these motivations will allow you to predict how they'll act and the areas they'll go after.
It helps you prioritize risks As hackers target the most easy victims first, PASTA can help you identify the most vulnerable risks and tackle the most vulnerable risks first. This will help you focus your efforts on what's most important to you.
In the world of cyber security, waiting around for a cyber attack to occur and then reacting is not enough anymore. With the increasing sophistication of threats businesses should be proactive about security. PASTA Threat Modeling lets you to accomplish this. By thinking like hackers it is possible to identify threats before they become real threats, and then strengthen your defenses accordingly.
The PASTA procedure allows you to play with potential attacks, learn about hacker techniques, and set your security needs prior to all other security concerns. This method ensures you are one step ahead of the game and safeguards your systems more efficiently.