Symmetric, Asymmetric & Hybrid Encryption Explained Simply. How TLS (HTTPS) Works
1. Introduction 2. Core Encryption Types 2.1. Symmetric Encryption 2.2. Asymmetric Encryption 3. Hybrid Encryption Scheme 4. TLS / SSL 5. Classification of encryption algorithms 6. Conclusion 1. Introduction Encryption is the process of converting readable data (plaintext) into an unreadable format (ciphertext) so that only authorized recipients can decipher it There are two primary types of encryption: Symmetric: The same key is used for both encryption and decryption Asymmetric: Two different keys are used—one to encrypt, another to decrypt Hybrid encryption isn’t a standalone type but rather a data exchange scheme combining both methods 2. Core Encryption Types 2.1. Symmetric Encryption How Symmetric Encryption Works The sender and recipient share the same secret key If a hacker obtains this key, they can decrypt all messages Simple example: Caesar Cipher Concept: Each letter in a message is shifted by a fixed number of positions in the alphabet. The key is the shift value def caesar_encrypt(text, shift): result = "" for char in text: if char.isalpha(): # Check if the character is a letter # Determine offset for uppercase (A-Z) or lowercase (a-z) letters offset = 65 if char.isupper() else 97 # Apply Caesar cipher with circular alphabet wrap (%26) result += chr((ord(char) - offset + shift) % 26 + offset) else: result += char # Non-alphabetic characters remain unchanged return result # Example: Shift by 3 positions print(caesar_encrypt("Hello, World!", 3)) # Output: "Khoor, Zruog!" Note: The Caesar cipher is a historical example and is not secure for modern use Modern algorithms: AES 3DES IDEA These are far more secure than the Caesar cipher but still rely on a single key 2.2. Asymmetric Encryption How Asymmetric Encryption Works The recipient generates a key pair: Public key: Shared freely Private key: Kept secret The sender encrypts data with the recipient’s public key Only the recipient’s private key can decrypt it Example scenario Bob generates a key pair (public + private) He distributes his public key (e.g., to Alice) Alice writes a message, encrypts it with Bob’s public key, and sends it Only Bob can decrypt it using his private key How is this possible? We ourselves encrypt a message with a public key and we ourselves can't decrypt it with the same key - that's right. It's the math that makes this system work. The keys are generated in a bundle: Public key - only encrypts Private key - only decrypts. Once Alice has encrypted her message, even she can't read it unless she has the private key. To further understand how this works, I recommend studying the RSA encryption algorithm - it's the one that shows how such a process is implemented in practice Modern algorithms: RSA ECC (Elliptic Curve Cryptography) Important: Asymmetric algorithms are inconvenient to encrypt large amounts of data because they are slow. Therefore, in practice they are used in combination with symmetric encryption, which is hybrid encryption 3. Hybrid Encryption Scheme Why use it? Asymmetric: Secure but slow. Symmetric: Fast but requires secure key exchange. Solution: Combine both. How Hybrid Encryption Works Symmetric Keys Exchange Scenario The recipient (Bob) generates a key pair - public and private - using the RSA algorithm The sender (Alice) generates a symmetric key for encryption (e.g., using the AES algorithm) Alice encrypts the symmetric key using Bob's public key The encrypted symmetric key is given to Bob. No one but him can decrypt it without the private key Bob receives the encrypted key and decrypts it using his private key Now both Alice and Bob have a common symmetric key known only to them They can then use this key to encrypt and decrypt messages. Asymmetric encryption is no longer required Instant Data Exchange Scenario The recipient (Bob) generates a key pair - public and private - using the RSA algorithm the sender (Alice) generates a symmetric key for encryption (e.g., using the AES algorithm) Alice encrypts the symmetric key using Bob's public key She then encrypts her message using the symmetric key created Alice sends Bob two items: the encrypted symmetric key and the encrypted message Bob receives the encrypted key and decrypts it using his private key After obtaining the symmetric key, Bob decrypts the message. Thus, he simultaneously obtains both the key and the contents of the message. They can then use this key to encrypt and decrypt the messages. Asymmetric encryption is no longer required 4. TLS / SSL TLS (Transport Layer Security) - A protocol to protect data transmitted over the Internet. SSL (Secure Sockets Layer) is an older version. Before these protocols, the http protocol was used, now it is https, whic

- 1. Introduction
-
2. Core Encryption Types
- 2.1. Symmetric Encryption
- 2.2. Asymmetric Encryption
- 3. Hybrid Encryption Scheme
- 4. TLS / SSL
- 5. Classification of encryption algorithms
- 6. Conclusion
1. Introduction
Encryption is the process of converting readable data (plaintext) into an unreadable format (ciphertext) so that only authorized recipients can decipher it
There are two primary types of encryption:
- Symmetric: The same key is used for both encryption and decryption
- Asymmetric: Two different keys are used—one to encrypt, another to decrypt
Hybrid encryption isn’t a standalone type but rather a data exchange scheme combining both methods
2. Core Encryption Types
2.1. Symmetric Encryption
How Symmetric Encryption Works
- The sender and recipient share the same secret key
- If a hacker obtains this key, they can decrypt all messages
Simple example: Caesar Cipher
Concept: Each letter in a message is shifted by a fixed number of positions in the alphabet. The key is the shift value
def caesar_encrypt(text, shift):
result = ""
for char in text:
if char.isalpha(): # Check if the character is a letter
# Determine offset for uppercase (A-Z) or lowercase (a-z) letters
offset = 65 if char.isupper() else 97
# Apply Caesar cipher with circular alphabet wrap (%26)
result += chr((ord(char) - offset + shift) % 26 + offset)
else:
result += char # Non-alphabetic characters remain unchanged
return result
# Example: Shift by 3 positions
print(caesar_encrypt("Hello, World!", 3)) # Output: "Khoor, Zruog!"
Note: The Caesar cipher is a historical example and is not secure for modern use
Modern algorithms:
These are far more secure than the Caesar cipher but still rely on a single key
2.2. Asymmetric Encryption
How Asymmetric Encryption Works
- The recipient generates a key pair:
- Public key: Shared freely
- Private key: Kept secret
- The sender encrypts data with the recipient’s public key
- Only the recipient’s private key can decrypt it
Example scenario
- Bob generates a key pair (public + private)
- He distributes his public key (e.g., to Alice)
- Alice writes a message, encrypts it with Bob’s public key, and sends it
- Only Bob can decrypt it using his private key
How is this possible?
We ourselves encrypt a message with a public key and we ourselves can't decrypt it with the same key - that's right. It's the math that makes this system work.
The keys are generated in a bundle:
- Public key - only encrypts
- Private key - only decrypts.
Once Alice has encrypted her message, even she can't read it unless she has the private key. To further understand how this works, I recommend studying the RSA encryption algorithm - it's the one that shows how such a process is implemented in practice
Modern algorithms:
Important: Asymmetric algorithms are inconvenient to encrypt large amounts of data because they are slow. Therefore, in practice they are used in combination with symmetric encryption, which is hybrid encryption
3. Hybrid Encryption Scheme
Why use it?
- Asymmetric: Secure but slow.
- Symmetric: Fast but requires secure key exchange.
- Solution: Combine both.
How Hybrid Encryption Works
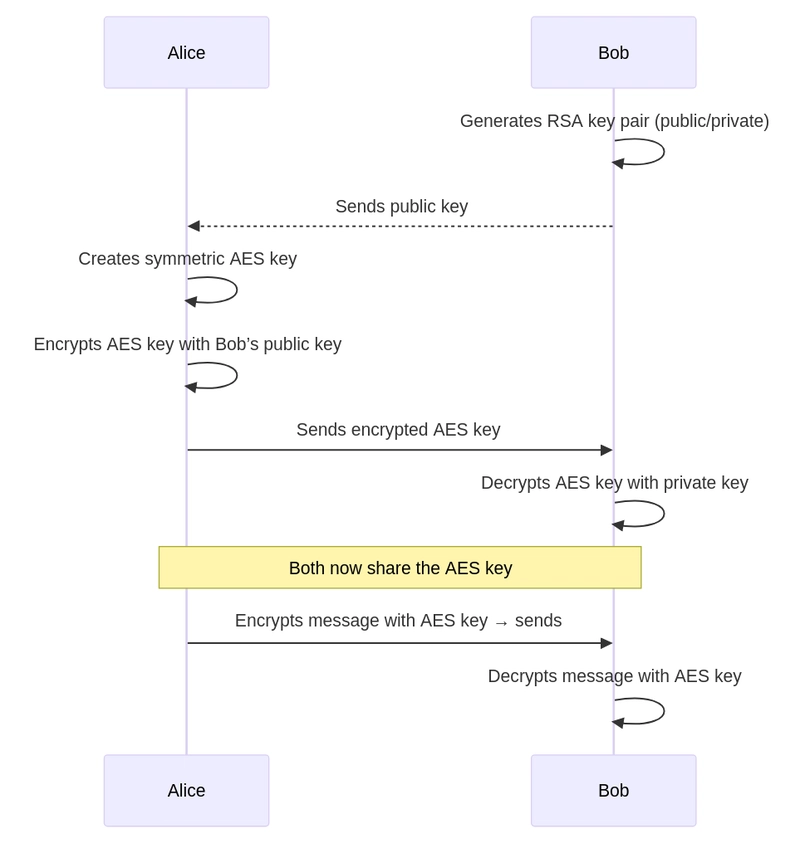
Symmetric Keys Exchange Scenario
- The recipient (Bob) generates a key pair - public and private - using the RSA algorithm
- The sender (Alice) generates a symmetric key for encryption (e.g., using the AES algorithm)
- Alice encrypts the symmetric key using Bob's public key
- The encrypted symmetric key is given to Bob. No one but him can decrypt it without the private key
- Bob receives the encrypted key and decrypts it using his private key
- Now both Alice and Bob have a common symmetric key known only to them
- They can then use this key to encrypt and decrypt messages. Asymmetric encryption is no longer required
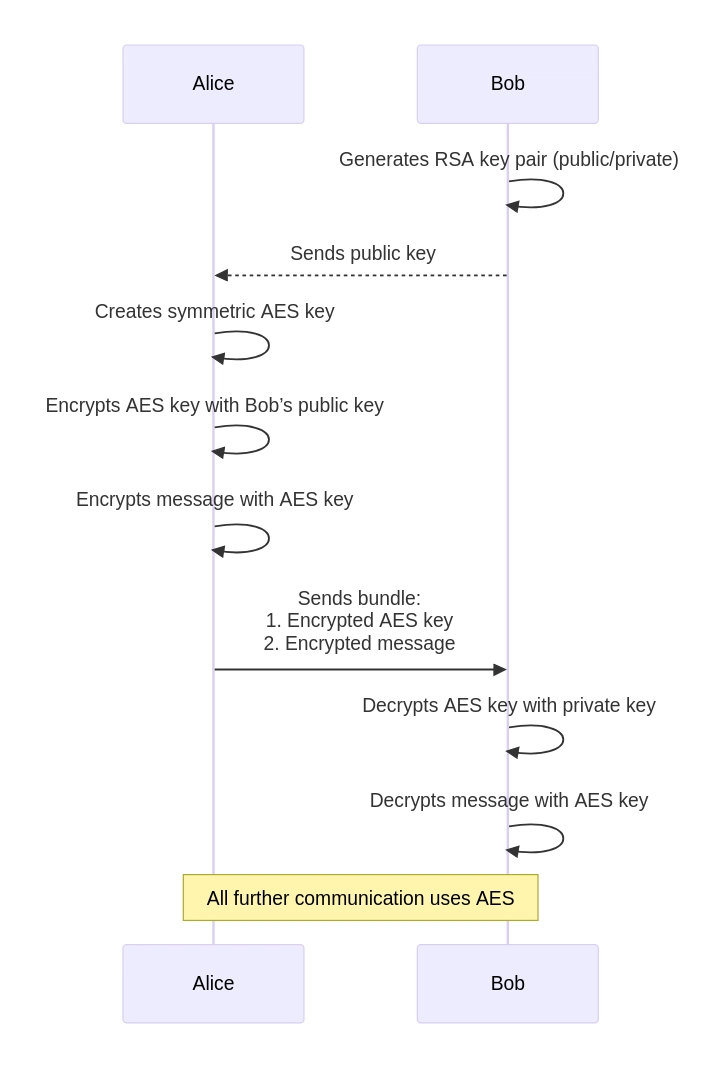
Instant Data Exchange Scenario
- The recipient (Bob) generates a key pair - public and private - using the RSA algorithm
- the sender (Alice) generates a symmetric key for encryption (e.g., using the AES algorithm)
- Alice encrypts the symmetric key using Bob's public key
- She then encrypts her message using the symmetric key created
- Alice sends Bob two items: the encrypted symmetric key and the encrypted message
- Bob receives the encrypted key and decrypts it using his private key
- After obtaining the symmetric key, Bob decrypts the message. Thus, he simultaneously obtains both the key and the contents of the message. They can then use this key to encrypt and decrypt the messages. Asymmetric encryption is no longer required
4. TLS / SSL
TLS (Transport Layer Security) - A protocol to protect data transmitted over the Internet. SSL (Secure Sockets Layer) is an older version. Before these protocols, the http protocol was used, now it is https, which ensures that your data is encrypted when requests are made to the server
TLS Handshake
- A Client (e.g., browser) connects to the server (
https://example.com) and requests a secure connection - The Server sends its public key and a SSL certificate signed by a certificate authority
- The client verifies the authenticity of the certificate
- The client creates a symmetric key, encrypts it with the server's public key, and sends it to the server
- The server decrypts the symmetric key with its private key
- Now both parties have a common symmetric key, and all further data is encrypted with that key
This is hybrid encryption in action: first asymmetric encryption is used to transmit the symmetric key, and then symmetric encryption is used for speed.
SSL Certificates
- Issued by special organizations - Certification Authorities (CAs)
- Signed by the CA's digital signature
- Contains domain, organization, expiration date and public key
5. Classification of encryption algorithms
-
By the number of keys:
- Symmetric - one key is used for encryption and decryption. Examples:
AES,3DES,IDEA. - Asymmetric - two keys are used: public and private. Examples:
RSA,ECC.
- Symmetric - one key is used for encryption and decryption. Examples:
-
Algorithm structure: 1.
- Block Ciphers - process data in fixed-size blocks. Examples:
AES,DES. - Stream Ciphers - encrypt data by bytes or bits. Examples:
RC4,ChaCha20.
- Block Ciphers - process data in fixed-size blocks. Examples:
6. Conclusion
That's it






































/https://tf-cmsv2-smithsonianmag-media.s3.amazonaws.com/filer_public/63/22/6322340c-6ff4-4e62-9324-e8b9a2a6b0f6/main_danielle-spreading-fungal-inoculum-adam-photo-cred_web.jpg?#)