Cloud Made Easy: AWS Control Tower
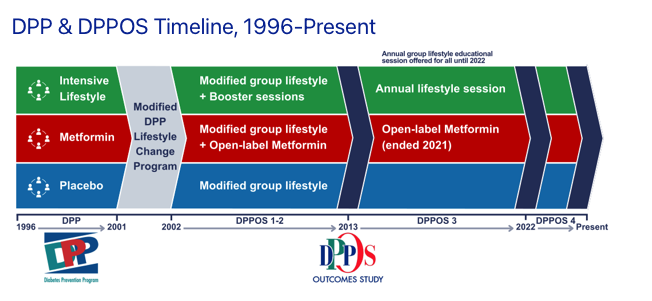
Hello Cloud Learners, I hope you are doing well. Let's explore today something interesting and very important AWS service: Control tower. Imagine trying to manage dozens of AWS accounts manually-each with its own users, permissions, security policies, and compliance requirements. Now imagine doing it all with just a few clicks. That's the magic of AWS Control Tower, and it's transforming how enterprises scale their cloud operations. Organizations struggle most not with individual services, but with establishing a coherent, secure foundation for their cloud journey. AWS Control Tower solves this fundamental challenge by providing a streamlined way to set up and govern a multi-account AWS environment following best practices. ** Understanding AWS Control Tower: The Foundation of Multi-Account Management ** AWS Control Tower offers a straightforward approach to establishing and governing a secure, compliant multi-account AWS environment. It orchestrates several AWS services, including AWS Organizations, AWS Service Catalog, and AWS IAM Identity Center, to build what's called a "landing zone" in less than an hour. This orchestration extends the capabilities of AWS Organizations while setting up resources and managing them on your behalf. Why Control Tower Matters In my early days of AWS consulting, I'd spend weeks helping clients establish proper account structures, security baselines, and governance models. Today, Control Tower automates most of this work. If you're managing more than a handful of accounts, having this orchestration layer becomes invaluable for both account deployment and governance. The real power of Control Tower lies in its ability to balance two competing needs: Enabling end users to quickly provision new AWS accounts through configurable templates Allowing central cloud administrators to ensure all accounts align with company-wide compliance policies This balance between agility and control is what makes Control Tower the easiest way to set up a secure, compliant multi-account AWS environment based on best practices established through thousands of enterprise implementations. Key Components of AWS Control Tower Landing Zone A landing zone is the well-architected, multi-account environment that serves as the foundation for your AWS organization. Think of it as the enterprise-wide container that holds all your organizational units (OUs), accounts, users, and other resources subject to compliance regulation. What makes landing zones powerful is their scalability-they can accommodate enterprises of any size, from startups to global corporations. Controls (Guardrails) Controls, often called guardrails, are high-level rules that provide ongoing governance for your AWS environment. They're expressed in plain language to make them accessible to both technical and non-technical stakeholders. Controls come in three types: Preventive controls: Block actions before they occur Detective controls: Identify non-compliance after it happens Proactive controls: Guide users toward best practices They also fall into three guidance categories: Mandatory: Must be implemented Strongly recommended: Should be implemented in most cases Elective: Optional based on specific needs These guardrails help prevent "drift"-the gradual divergence from best practices that often happens as environments grow organically. Account Factory Account Factory is a configurable account template that standardizes the provisioning of new accounts with pre-approved configurations. It essentially automates the account provisioning workflow in your organization. Think of Account Factory as a vending machine for AWS accounts-it delivers standardized, compliant accounts on demand. This component is sometimes referred to as an Account Vending Machine (AVM). Dashboard The Control Tower dashboard provides continuous oversight of your landing zone. It gives central cloud administrators visibility into: Provisioned accounts across the enterprise Controls enabled for policy enforcement Controls enabled for continuous detection of policy non-conformance Non-compliant resources organized by accounts and OUs The Architecture of AWS Control Tower When you implement Control Tower, it creates a structured organization with several Organizational Units (OUs): Security OU This contains two critical accounts: Log Archive Account: Serves as a central repository for all CloudTrail and AWS Config logs across the landing zone, with data securely stored in S3 buckets Audit Account: Provides a dedicated environment for security auditing functions Sandbox OU This OU hosts testing accounts that are safely isolated from production workloads, allowing teams to experiment without risk. Production OU As the name suggests, this OU houses all production accounts containing live workloads. Non-Production OU This serves as a pre-production environment for further testing and development before deploying to pr

Hello Cloud Learners,
I hope you are doing well.
Let's explore today something interesting and very important AWS service: Control tower.
Imagine trying to manage dozens of AWS accounts manually-each with its own users, permissions, security policies, and compliance requirements. Now imagine doing it all with just a few clicks. That's the magic of AWS Control Tower, and it's transforming how enterprises scale their cloud operations.
Organizations struggle most not with individual services, but with establishing a coherent, secure foundation for their cloud journey. AWS Control Tower solves this fundamental challenge by providing a streamlined way to set up and govern a multi-account AWS environment following best practices.
**
Understanding AWS Control Tower: The Foundation of Multi-Account Management
**
AWS Control Tower offers a straightforward approach to establishing and governing a secure, compliant multi-account AWS environment. It orchestrates several AWS services, including AWS Organizations, AWS Service Catalog, and AWS IAM Identity Center, to build what's called a "landing zone" in less than an hour. This orchestration extends the capabilities of AWS Organizations while setting up resources and managing them on your behalf.
Why Control Tower Matters
In my early days of AWS consulting, I'd spend weeks helping clients establish proper account structures, security baselines, and governance models. Today, Control Tower automates most of this work. If you're managing more than a handful of accounts, having this orchestration layer becomes invaluable for both account deployment and governance.
The real power of Control Tower lies in its ability to balance two competing needs:
Enabling end users to quickly provision new AWS accounts through configurable templates
Allowing central cloud administrators to ensure all accounts align with company-wide compliance policies
This balance between agility and control is what makes Control Tower the easiest way to set up a secure, compliant multi-account AWS environment based on best practices established through thousands of enterprise implementations.
Key Components of AWS Control Tower
Landing Zone
A landing zone is the well-architected, multi-account environment that serves as the foundation for your AWS organization. Think of it as the enterprise-wide container that holds all your organizational units (OUs), accounts, users, and other resources subject to compliance regulation.
What makes landing zones powerful is their scalability-they can accommodate enterprises of any size, from startups to global corporations.
Controls (Guardrails)
Controls, often called guardrails, are high-level rules that provide ongoing governance for your AWS environment. They're expressed in plain language to make them accessible to both technical and non-technical stakeholders.
Controls come in three types:
- Preventive controls: Block actions before they occur
- Detective controls: Identify non-compliance after it happens
- Proactive controls: Guide users toward best practices
They also fall into three guidance categories:
- Mandatory: Must be implemented
- Strongly recommended: Should be implemented in most cases
- Elective: Optional based on specific needs
These guardrails help prevent "drift"-the gradual divergence from best practices that often happens as environments grow organically.
Account Factory
Account Factory is a configurable account template that standardizes the provisioning of new accounts with pre-approved configurations. It essentially automates the account provisioning workflow in your organization.
Think of Account Factory as a vending machine for AWS accounts-it delivers standardized, compliant accounts on demand. This component is sometimes referred to as an Account Vending Machine (AVM).
Dashboard
The Control Tower dashboard provides continuous oversight of your landing zone. It gives central cloud administrators visibility into:
- Provisioned accounts across the enterprise
- Controls enabled for policy enforcement
- Controls enabled for continuous detection of policy non-conformance
- Non-compliant resources organized by accounts and OUs
The Architecture of AWS Control Tower
When you implement Control Tower, it creates a structured organization with several Organizational Units (OUs):
Security OU
This contains two critical accounts:
Log Archive Account: Serves as a central repository for all CloudTrail and AWS Config logs across the landing zone, with data securely stored in S3 buckets
Audit Account: Provides a dedicated environment for security auditing functions
Sandbox OU
This OU hosts testing accounts that are safely isolated from production workloads, allowing teams to experiment without risk.
Production OU
As the name suggests, this OU houses all production accounts containing live workloads.
Non-Production OU
This serves as a pre-production environment for further testing and development before deploying to production.
Suspended OU
This is a highly restricted OU where deleted, reused, or breached accounts can be moved. Permissions here are extremely limited to ensure security.
Shared Services OU
This contains accounts for services shared across multiple other accounts, typically including:
- Shared Services Account: Where resources are directly shared
- Security Services Account: Hosting services like Amazon Inspector, Amazon Macie, and AWS Secrets Manager
- Networking Account: Contains VPC Endpoints, DNS Endpoints, and other networking components
This architecture provides a clear separation of concerns while enabling centralized management and governance.
Hands-On: Setting Up Your AWS Control Tower Landing Zone
Let's walk through the process of setting up a landing zone using AWS Control Tower. I'll guide you through each step with detailed instructions.
Prerequisites
- An AWS account with administrative privileges
- Unique email addresses for the Log Archive and Audit accounts
- Basic understanding of AWS Organizations
Step 1: Access AWS Control Tower and Begin Setup
- Log into your AWS Management Console
- Navigate to the AWS Control Tower service
- On the Control Tower home page, click "Set up landing zone"
AWS will inform you what to expect: Control Tower will have the ability to govern resources across accounts and organizational units, but it won't take control of everything by default. You can extend governance later as needed.
Step 2: Define Your Home Region and Region Settings
- Select your home region (e.g., us-east-1 North Virginia)
- Configure the Region Deny setting if you want to prohibit access to services in specific regions
- If enabled, you can define which regions you want to control
- If not enabled, all regions will be accessible
- Select additional regions for governance if desired
- Click "Next"
Step 3: Define Organizational Unit Structure
- Review the foundational OU (typically named "Security")
- This will contain the Log Archive and Security Audit accounts
- Create additional OUs if desired (e.g., "Sandbox" for dev/test workloads)
- Click "Next"
Step 4: Configure Shared Accounts and Encryption Settings
- Review the Management Account settings (this will be your current account)
- Configure the Log Archive Account
- Provide a unique email address
Optionally change the account name
Configure the Audit Account
Provide another unique email address
Optionally change the account name
Enable encryption settings if desired
Click "Next"
Step 5: Review and Confirm
- Review all the information you've provided
- Check the box to confirm that Control Tower will be granted permissions to access your resources and enforce rules
- Click "Set up landing zone"
The setup process typically takes 30-60 minutes to complete. During this time, AWS Control Tower is:
- Creating the organizational structure
- Setting up the Log Archive and Audit accounts
- Configuring baseline security services
- Implementing mandatory controls
Step 6: Secure Your Environment
After the landing zone is created, it's important to secure your environment:
- Set complex passwords for all accounts
- Enable multi-factor authentication (MFA)
- Create account aliases to make identification easier
- Set up cross-account access roles to simplify management
For cross-account access:
- In each new account, create a role named "admin" (or something descriptive)
- Grant this role the "AdministratorAccess" policy
- Set the trust relationship to your root account
- Use the "Switch Roles" feature to move between accounts without logging in and out
Step 7: Create Additional Accounts Using Account Factory
Once your landing zone is established, you can create additional accounts:
- Navigate to AWS Control Tower
- Go to "Account Factory"
- Click "Create account"
- Provide account details:
- Account email
- Account name
- IAM Identity Center user email (if using IAM Identity Center)
- Organizational unit
- Network configuration
- Click "Create account"
The account provisioning process typically takes 10-15 minutes.
Extending Control Tower with Account Factory for Terraform (AFT)
For organizations that use Infrastructure as Code (IaC), AWS offers Account Factory for Terraform (AFT). This powerful extension sets up a Terraform pipeline to provision and customize accounts in AWS Control Tower, combining the advantages of Terraform-based account provisioning with Control Tower governance.
How AFT Works
AFT creates a separate account called the "AFT management account" to deploy AFT capabilities. The workflow is straightforward:
- Create an account request Terraform file
- This file triggers the AFT workflow for account provisioning
- After provisioning completes, AFT automatically runs a series of steps
- The account customizations stage begins
AFT supports multiple Terraform distributions:
- Terraform Cloud
- Terraform Enterprise
- Terraform Community Edition
The beauty of AFT is that you can initiate account creation using a simple input file and a "git push" command. This allows you to customize new or existing accounts while maintaining all the governance benefits of AWS Control Tower.
Key Features of AFT
- GitOps model: Submit account provisioning and update requests through Git
- Metadata storage: Store account metadata and audit history
- Account-level tagging: Apply consistent tags across accounts
- Customization flexibility: Apply customizations to all accounts, sets of accounts, or individual accounts
- Feature options: Enable additional capabilities as needed
AFT also supports account customization request tracing. Each time you submit an account customization request, AFT generates a unique tracing token that passes through an AWS Step Functions state machine, which logs the token as part of its execution. This allows you to trace your account customization requests throughout the entire AFT workflow.
Real-World Example: Implementing Control Tower for a Growing Enterprise
Let me share a real-world scenario I encountered with a client who was experiencing rapid growth.
The Challenge
A mid-sized financial services company had started with a single AWS account three years ago. As they grew, they had organically expanded to 15 accounts with inconsistent security configurations, IAM policies, and logging practices. Their compliance team was raising concerns about their ability to meet regulatory requirements, and their developers were frustrated by the inconsistent environments.
The Solution
We implemented AWS Control Tower to establish a proper foundation:
Assessment: We mapped their existing accounts and identified which ones could be migrated and which needed to be rebuilt.
Landing Zone Setup: We established a Control Tower landing zone with the following OUs:
- Security (for Log Archive and Audit)
- Production (for customer-facing services)
- Non-Production (for development and testing)
- Shared Services (for common resources like Active Directory and monitoring)
Account Migration: We migrated existing accounts into the appropriate OUs and created new accounts using Account Factory.
Guardrails Implementation: We enabled mandatory and strongly recommended guardrails, plus additional elective guardrails specific to financial services.
IAM Identity Center Integration: We integrated with their existing identity provider for single sign-on.
Automation: We implemented Account Factory for Terraform to automate the provisioning of new accounts with consistent configurations.
The Results
Within three months, the company had:
- Reduced security findings by 78%
- Decreased the time to provision new accounts from days to minutes
- Improved developer satisfaction by providing consistent environments
- Passed their compliance audit with minimal findings
- Established a scalable foundation that could grow with their business
This transformation wasn't just about technology-it was about establishing processes and governance that aligned with their business objectives while maintaining security and compliance.
Best Practices for AWS Control Tower
Based on my experience implementing Control Tower for dozens of organizations, here are some best practices to consider:
1. Plan Your OU Structure Carefully
Your organizational unit structure should reflect your business needs. Consider factors like:
- Business units or departments
- Environment types (dev, test, prod)
- Compliance requirements
- Cost allocation
Once established, changing the OU structure can be challenging, so invest time in planning.
2. Start with Mandatory and Strongly Recommended Guardrails
Begin with the guardrails AWS recommends before adding custom ones. This establishes a solid baseline of security and compliance.
3. Implement Consistent Tagging
Develop a comprehensive tagging strategy for resources across all accounts. This facilitates cost allocation, ownership tracking, and automation.
4. Use Service Control Policies (SCPs) Judiciously
SCPs are powerful tools for enforcing policies across your organization, but they can be disruptive if implemented incorrectly. Test SCPs thoroughly before applying them broadly.
5. Integrate with Your Identity Provider
Use AWS IAM Identity Center (formerly AWS Single Sign-On) to integrate with your corporate identity provider. This provides a seamless experience for users and simplifies access management.
6. Automate Account Provisioning
Leverage Account Factory or Account Factory for Terraform to automate the provisioning of new accounts. This ensures consistency and reduces manual effort.
7. Monitor for Drift
Regularly review the Control Tower dashboard for signs of drift-resources or configurations that no longer comply with your guardrails. Address drift promptly to maintain your security posture.
8. Document Your Environment
Maintain comprehensive documentation of your Control Tower environment, including:
- OU structure
- Enabled guardrails
- Custom policies
- Account provisioning processes
This documentation is invaluable for onboarding new team members and during audits.
Limitations and Considerations
While AWS Control Tower offers significant benefits, it's important to be aware of its limitations:
1. Initial Setup Requirements
Control Tower requires new email addresses for the Log Archive and Audit accounts. If you're integrating existing accounts, you'll need to plan for this requirement.
2. Region Limitations
Control Tower is not available in all AWS regions. Ensure it's available in the regions where you plan to operate.
3. Service Integration Constraints
Some AWS services may have specific requirements or limitations when used with Control Tower. Review the documentation for any services critical to your workloads.
4. Customization Complexity
While Control Tower provides a solid foundation, complex customizations may require additional effort. Account Factory for Terraform can help address this challenge.
5. Cost Considerations
Control Tower itself doesn't incur additional charges, but the AWS services it configures (such as AWS Config and CloudTrail) do. Factor these costs into your budget planning.
The Future of AWS Control Tower
AWS continues to enhance Control Tower with new features and capabilities. Some recent and anticipated developments include:
1. Expanded Guardrail Coverage
AWS is continuously adding new guardrails to address emerging security and compliance requirements.
2. Enhanced Customization Options
Expect more flexibility in customizing landing zones to meet specific organizational needs.
3. Improved Integration with AWS Services
Tighter integration with services like AWS Security Hub, AWS Config, and AWS Organizations will provide more comprehensive governance.
4. Advanced Automation Capabilities
Enhanced automation for account provisioning, policy enforcement, and remediation will further streamline management.
5. Multi-Region Support Enhancements
Improved support for managing resources across multiple regions will benefit global organizations.
Conclusion and Call to Action
AWS Control Tower represents a paradigm shift in how organizations approach multi-account AWS environments. By providing a structured, automated approach to account provisioning and governance, it addresses the fundamental challenges of scaling in the cloud while maintaining security and compliance.
Whether you're a startup planning for growth or an enterprise rationalizing an existing AWS footprint, Control Tower offers a path to a well-architected, governed cloud environment.
Take the Next Steps
Assess your current environment: Evaluate your existing AWS accounts and identify opportunities for consolidation and standardization.
Plan your landing zone: Define your organizational structure, account requirements, and governance needs.
Start small: Begin with a pilot implementation of Control Tower in a controlled environment to gain experience.
Develop a migration strategy: Plan how you'll transition existing workloads into your new landing zone.
Invest in training: Ensure your team understands Control Tower concepts and operations.
Engage with the community: Join AWS forums and user groups to learn from others' experiences.
The cloud journey is a marathon, not a sprint. AWS Control Tower provides the foundation that will support your organization's growth and innovation for years to come. By investing in a well-designed landing zone today, you're setting your organization up for success in an increasingly cloud-centric world.
Are you ready to transform how you manage your AWS environment? The time to act is now. Your future self-and your security, operations, and development teams-will thank you.
Hope this blog given some insights or trigger point to understand AWS Control tower concepts and feel free to reach out to me if in case of any assistance required, I'm glad to assist.
Let's grow each other and build strong cloud hands-on skills!
Follow me on LinkedIn for more AWS Cloud computing knowledge.
Happy Learning!
Cheers,
Logeswaran GV