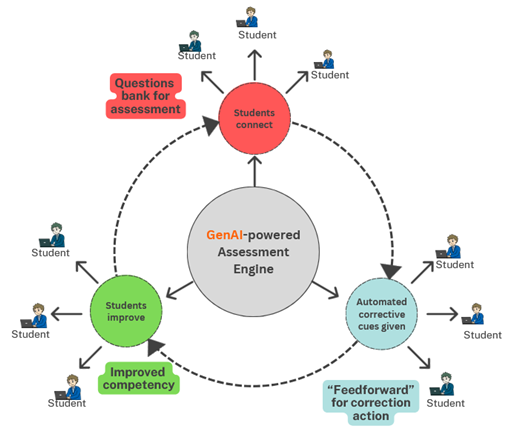
What is Threat Detection and Incident Response (TDIR)?
In today’s fast-evolving digital landscape, organizations must do more than just set up firewalls—they need proactive solutions to identify and respond to threats in real time. That’s where Threat Detection and Incident Response (TDIR) comes in. TDIR isn’t a single tool or software—it’s a strategic framework designed to help security teams spot suspicious activity early and act quickly to contain and eliminate potential threats. Breaking Down TDIR: Detection Meets Action TDIR consists of two core components: Threat Detection: Using automated tools and real-time monitoring, organizations can scan their networks, applications, and endpoints for signs of malicious behavior. It’s like a virtual security camera that never blinks, looking for anything out of the ordinary—from strange login attempts to unusual data transfers. Incident Response: Once a threat is flagged, the incident response team takes over. Their job is to assess the impact, investigate the root cause, contain the damage, and restore affected systems. It’s a race against time to prevent data loss, reputational harm, or operational downtime. Why TDIR is Essential in Cybersecurity Modern cyberattacks are smarter, faster, and harder to detect. Traditional security solutions often can’t keep up. TDIR gives organizations the visibility and agility needed to counter both known and unknown threats—whether it’s a phishing attempt, a malware infection, or insider misuse. Here’s why TDIR matters: Helps identify vulnerabilities early Reduces response times during security events Protects sensitive data and operations Ensures compliance with industry standards and regulations Builds trust with customers through strong cybersecurity practices The TDIR Lifecycle: From Awareness to Action Data Collection: Gather logs, activity reports, and asset inventories to understand your IT environment. Threat Identification: Use advanced analytics and threat intelligence to pinpoint potential risks. Incident Analysis: Investigate suspicious behavior, determine the impact, and prioritize response based on risk. Remediation & Recovery: Deploy playbooks, patch vulnerabilities, and restore systems while documenting every step. Best Practices for Effective TDIR Invest in modern SIEM and SOAR tools Automate repetitive tasks for efficiency Train your team to recognize early warning signs Create a clear incident response plan Continuously update your processes as threats evolve Final Thoughts TDIR is more than a safety net—it’s a necessary pillar of modern cybersecurity. With the right tools and strategy, organizations can detect threats before they escalate and respond with speed and precision. In the face of rising cyber risks, a well-executed TDIR program is the key to resilience.


In today’s fast-evolving digital landscape, organizations must do more than just set up firewalls—they need proactive solutions to identify and respond to threats in real time. That’s where Threat Detection and Incident Response (TDIR) comes in. TDIR isn’t a single tool or software—it’s a strategic framework designed to help security teams spot suspicious activity early and act quickly to contain and eliminate potential threats.
Breaking Down TDIR: Detection Meets Action
TDIR consists of two core components:
- Threat Detection: Using automated tools and real-time monitoring, organizations can scan their networks, applications, and endpoints for signs of malicious behavior. It’s like a virtual security camera that never blinks, looking for anything out of the ordinary—from strange login attempts to unusual data transfers.
- Incident Response: Once a threat is flagged, the incident response team takes over. Their job is to assess the impact, investigate the root cause, contain the damage, and restore affected systems. It’s a race against time to prevent data loss, reputational harm, or operational downtime.
Why TDIR is Essential in Cybersecurity
Modern cyberattacks are smarter, faster, and harder to detect. Traditional security solutions often can’t keep up. TDIR gives organizations the visibility and agility needed to counter both known and unknown threats—whether it’s a phishing attempt, a malware infection, or insider misuse.
Here’s why TDIR matters:
- Helps identify vulnerabilities early
- Reduces response times during security events
- Protects sensitive data and operations
- Ensures compliance with industry standards and regulations
- Builds trust with customers through strong cybersecurity practices
The TDIR Lifecycle: From Awareness to Action
- Data Collection: Gather logs, activity reports, and asset inventories to understand your IT environment.
- Threat Identification: Use advanced analytics and threat intelligence to pinpoint potential risks.
- Incident Analysis: Investigate suspicious behavior, determine the impact, and prioritize response based on risk.
- Remediation & Recovery: Deploy playbooks, patch vulnerabilities, and restore systems while documenting every step.
Best Practices for Effective TDIR
- Invest in modern SIEM and SOAR tools
- Automate repetitive tasks for efficiency
- Train your team to recognize early warning signs
- Create a clear incident response plan
- Continuously update your processes as threats evolve
Final Thoughts
TDIR is more than a safety net—it’s a necessary pillar of modern cybersecurity. With the right tools and strategy, organizations can detect threats before they escalate and respond with speed and precision. In the face of rising cyber risks, a well-executed TDIR program is the key to resilience.

















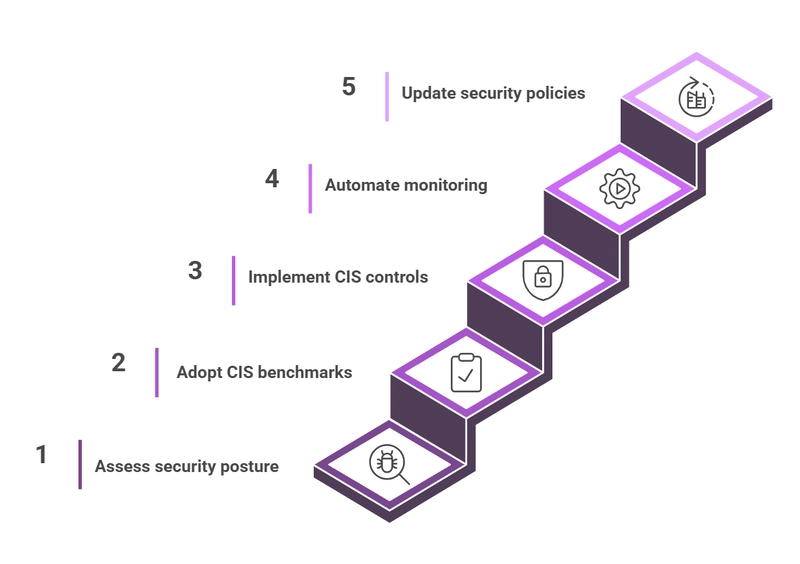


-(1).png?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)