Kata Containers: Lightweight VMs for Containers
Introduction In today’s cloud-native world, containers have become the standard unit of software delivery. They allow developers to package applications along with their dependencies into lightweight, portable units that can run reliably across different environments. This has revolutionized the way we build, ship, and run applications—from developer laptops to large-scale Kubernetes clusters. But while containers are efficient and fast, they come with a trade-off: security. Traditional containers share the host operating system’s kernel. That means if a container is compromised, there’s a potential risk to the entire system. For many teams running multi-tenant clusters or handling untrusted workloads, that risk isn’t acceptable. This is where Kata Containers come in—a project designed to bridge the gap between the speed of containers and the strong isolation of virtual machines. Kata Containers look and feel like containers, but under the hood, they run inside lightweight VMs using a separate kernel. This offers a level of isolation closer to traditional virtualization, without the overhead that comes with full-blown hypervisors. Whether you're managing sensitive data, running sandboxed workloads, or building a secure Kubernetes platform, Kata Containers can offer a powerful middle ground. To better understand what makes Kata Containers different, let’s take a look at a side-by-side comparison with traditional containers. source : https://yqintl.alicdn.com/fb67232d2a5e2e8afbc7968c9227f7dd4121bbaf.png On the right side of the diagram, we see how traditional containers work. Each containerized process (A, B, C) shares the same Linux kernel. Isolation is achieved using namespaces, cgroups, and additional filters like seccomp, MAC (Mandatory Access Control), and capabilities. While this method is lightweight and fast, it still means that all containers rely on the host’s kernel. If one container exploits a kernel vulnerability, it could potentially affect others or even the host. On the left side, Kata Containers take a different approach. Each containerized process runs inside its own lightweight virtual machine, with a dedicated kernel (e.g., Linux Kernel A, B, C). These VMs are powered by hardware virtualization, which provides strong, hardware-enforced isolation between workloads. From the perspective of the process inside, it’s still running in a container—but behind the scenes, it’s isolated as if it were a small, independent VM. In practice, this means Kata Containers offer much stronger security boundaries. If a container running inside a Kata VM is compromised, the attack surface is significantly reduced—it would have to break through an entire virtualized layer rather than just a namespace. The tradeoff? Slightly more overhead compared to traditional containers. But in environments where security and workload isolation are top priorities—like multi-tenant platforms, confidential workloads, or untrusted code—Kata Containers strike a compelling balance between performance and protection. Kata Containers may not be the default choice for every workload, but when security and strong isolation matter just as much as performance, they offer a powerful and elegant solution that bridges the best of both containers and virtual machines. Resources https://github.com/kata-containers/kata-containers/tree/main/docs/install
Introduction
In today’s cloud-native world, containers have become the standard unit of software delivery. They allow developers to package applications along with their dependencies into lightweight, portable units that can run reliably across different environments. This has revolutionized the way we build, ship, and run applications—from developer laptops to large-scale Kubernetes clusters.
But while containers are efficient and fast, they come with a trade-off: security. Traditional containers share the host operating system’s kernel. That means if a container is compromised, there’s a potential risk to the entire system. For many teams running multi-tenant clusters or handling untrusted workloads, that risk isn’t acceptable.
This is where Kata Containers come in—a project designed to bridge the gap between the speed of containers and the strong isolation of virtual machines. Kata Containers look and feel like containers, but under the hood, they run inside lightweight VMs using a separate kernel. This offers a level of isolation closer to traditional virtualization, without the overhead that comes with full-blown hypervisors. Whether you're managing sensitive data, running sandboxed workloads, or building a secure Kubernetes platform, Kata Containers can offer a powerful middle ground.
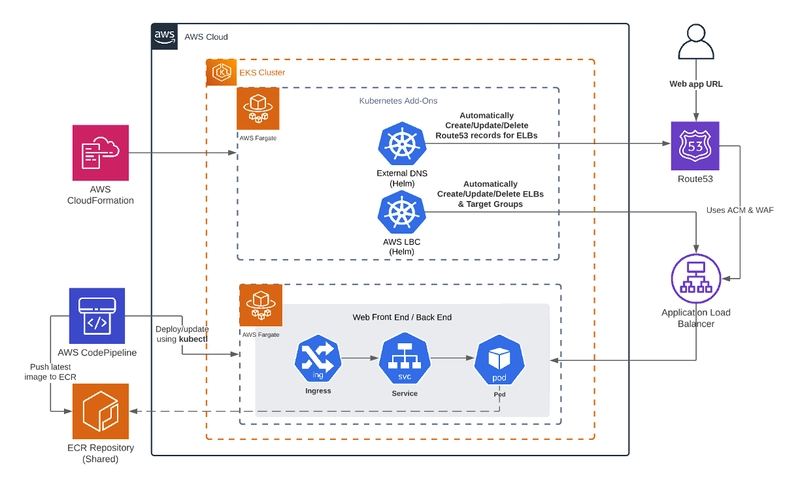
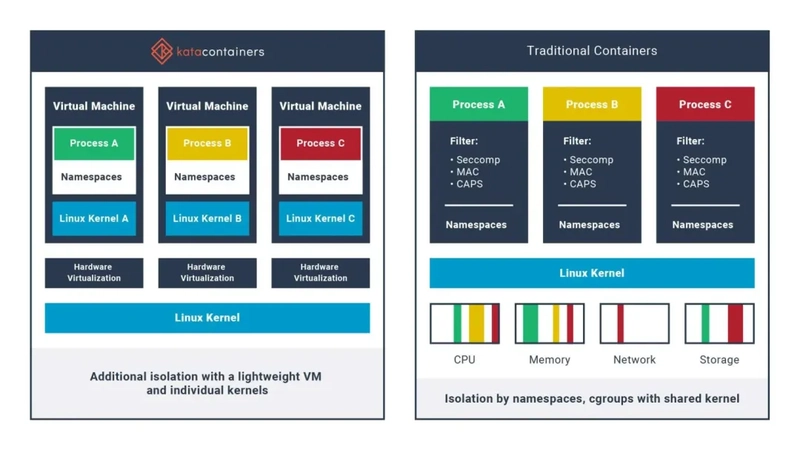
To better understand what makes Kata Containers different, let’s take a look at a side-by-side comparison with traditional containers.

source : https://yqintl.alicdn.com/fb67232d2a5e2e8afbc7968c9227f7dd4121bbaf.png
On the right side of the diagram, we see how traditional containers work. Each containerized process (A, B, C) shares the same Linux kernel. Isolation is achieved using namespaces, cgroups, and additional filters like seccomp, MAC (Mandatory Access Control), and capabilities. While this method is lightweight and fast, it still means that all containers rely on the host’s kernel. If one container exploits a kernel vulnerability, it could potentially affect others or even the host.
On the left side, Kata Containers take a different approach. Each containerized process runs inside its own lightweight virtual machine, with a dedicated kernel (e.g., Linux Kernel A, B, C). These VMs are powered by hardware virtualization, which provides strong, hardware-enforced isolation between workloads. From the perspective of the process inside, it’s still running in a container—but behind the scenes, it’s isolated as if it were a small, independent VM.
In practice, this means Kata Containers offer much stronger security boundaries. If a container running inside a Kata VM is compromised, the attack surface is significantly reduced—it would have to break through an entire virtualized layer rather than just a namespace.
The tradeoff? Slightly more overhead compared to traditional containers. But in environments where security and workload isolation are top priorities—like multi-tenant platforms, confidential workloads, or untrusted code—Kata Containers strike a compelling balance between performance and protection.
Kata Containers may not be the default choice for every workload, but when security and strong isolation matter just as much as performance, they offer a powerful and elegant solution that bridges the best of both containers and virtual machines.
Resources
https://github.com/kata-containers/kata-containers/tree/main/docs/install