Drosera HandBook: The ABC of Traps
The Drosera is a cunning carnivorous plant that lures its prey with a beautiful disguise glistening, nectar-like droplets that promise sweetness but deliver death. So when a company aiming to be at the forefront of smart contract security named itself Drosera, it sparked curiosity. pulling developers like myself, eager to find solutions to the long-standing Web3 security crisis. The bedrock of blockchain rests on Decentralization, Security, and Scalability. However, recent prioritizing of scalability over security has led to critical vulnerabilities and repeated hacks, creating a dilemma - over the future of blockchain Is there a fix? Vitalik Butterin, In his article "The Limits to Blockchain Scalability," discusses two primary approaches to scalability. Fundamental Technical Improvements: Implementing advanced solutions like zero-knowledge proofs, rollups, or sharding to enhance scalability without compromising security or decentralization. Increasing the Parameters: Simply raising the capacity limits (e.g., block size or gas limits) to allow more transactions per second. While all of these are viable solutions and mostly implemented we are still far from a possible long-term solution. Patches, rollups, and networks have been implemented, raising questions about why a solution remains elusive as there has been an unprecedented surge in hacks, surpassing previous years. In the first three months of 2025, over $1.6 billion has been stolen, with the ByBit hack alone accounting for $1.46 billion—making it the largest crypto heist in history. This far exceeds the $900 million lost in 2024 and the $1.7 billion stolen throughout all of 2023, rapidly approaching the $3.8 billion lost in 2022. Various solutions have been proposed, but no single fix has proven effective. As a result, the ecosystem has turned to a multipronged approach, incorporating layered security solutions, cryptographic methods, formal verification, and incentive-driven audits—throwing everything at the beast. Yet, like a patient pack of wolves, attackers continue to overwhelm defenses with crafty maneuvers. Drosera's emergence creates a eureka bulb moment in the ecosystem, not as just another web3 product but as a calculated predator in the fight against blockchain vulnerabilities. Rather than relying on static security measures that often fail against rapidly evolving threats, Drosera operates on a proactive security model. It integrates real-time exploit detection, automated smart contract analysis, and adversarial simulation—methods designed not just to react to attacks but to anticipate them. What is Drosera? Drosera is a security automation protocol designed for decentralized applications (dApps). It helps developers create smart contract monitoring systems that detect suspicious activity and trigger automated responses. Think of it as a security guard that never sleeps, constantly monitoring blockchain activity for potential threats. Unlike traditional security solutions that react after an attack occurs, Drosera works preemptively, identifying risks before they become exploits. It does this by deploying Traps—small smart contracts that monitor the blockchain, detect suspicious behavior, and take action when needed. How Does Drosera Work? At its core, Drosera operates on a simple yet powerful mechanism: Traps Collect Data – Scan blockchain transactions for anomalies. Analyze Data – The collected information is assessed to determine if an attack is happening. Trigger a Response – If the Trap detects malicious activity, it can execute a predefined response, such as pausing a contract or alerting security teams. Key Components of Drosera: Trap – A smart contract that defines monitoring rules. Trap Config – A configuration file that specifies how the Trap operates. Operators – Entities that validate and execute security measures. Together, these components allow Drosera to function as a decentralized security network, ensuring that smart contracts remain safe from attacks. Getting Started with Drosera CLI The Drosera Command Line Interface (CLI) is the primary tool for creating, managing, and monitoring Traps. It simplifies the process of integrating security automation into your blockchain applications. To get started, spin up a boilerplate npx @drosera/create-drosera-app or set up one using forge init -t drosera-network/trap-foundry-template on your terminal. Make sure you also have foundry installed, if you do not have it installed, set up foundry by running curl -L https://foundry.paradigm.xyz | bash. Next, install bun # install Bun curl -fsSL https://bun.sh/install | bash # install node modules bun install Set up a Vulnerable contract Create a vunerable.sol in the src folder, for this guide we will create a smart contract that allows anyone to take ownership. pragma solidity ^0.8.12; contract VulnerableContract { address public Owner; //
The Drosera is a cunning carnivorous plant that lures its prey with a beautiful disguise glistening, nectar-like droplets that promise sweetness but deliver death.
So when a company aiming to be at the forefront of smart contract security named itself Drosera, it sparked curiosity. pulling developers like myself, eager to find solutions to the long-standing Web3 security crisis.
The bedrock of blockchain rests on Decentralization, Security, and Scalability. However, recent prioritizing of scalability over security has led to critical vulnerabilities and repeated hacks, creating a dilemma - over the future of blockchain
Is there a fix?
Vitalik Butterin, In his article "The Limits to Blockchain Scalability," discusses two primary approaches to scalability.
Fundamental Technical Improvements: Implementing advanced solutions like zero-knowledge proofs, rollups, or sharding to enhance scalability without compromising security or decentralization.
Increasing the Parameters: Simply raising the capacity limits (e.g., block size or gas limits) to allow more transactions per second.
While all of these are viable solutions and mostly implemented we are still far from a possible long-term solution. Patches, rollups, and networks have been implemented, raising questions about why a solution remains elusive as there has been an unprecedented surge in hacks, surpassing previous years.
In the first three months of 2025, over $1.6 billion has been stolen, with the ByBit hack alone accounting for $1.46 billion—making it the largest crypto heist in history. This far exceeds the $900 million lost in 2024 and the $1.7 billion stolen throughout all of 2023, rapidly approaching the $3.8 billion lost in 2022.
Various solutions have been proposed, but no single fix has proven effective. As a result, the ecosystem has turned to a multipronged approach, incorporating layered security solutions, cryptographic methods, formal verification, and incentive-driven audits—throwing everything at the beast. Yet, like a patient pack of wolves, attackers continue to overwhelm defenses with crafty maneuvers.
Drosera's emergence creates a eureka bulb moment in the ecosystem, not as just another web3 product but as a calculated predator in the fight against blockchain vulnerabilities.
Rather than relying on static security measures that often fail against rapidly evolving threats, Drosera operates on a proactive security model. It integrates real-time exploit detection, automated smart contract analysis, and adversarial simulation—methods designed not just to react to attacks but to anticipate them.
What is Drosera?
Drosera is a security automation protocol designed for decentralized applications (dApps). It helps developers create smart contract monitoring systems that detect suspicious activity and trigger automated responses. Think of it as a security guard that never sleeps, constantly monitoring blockchain activity for potential threats.
Unlike traditional security solutions that react after an attack occurs, Drosera works preemptively, identifying risks before they become exploits. It does this by deploying Traps—small smart contracts that monitor the blockchain, detect suspicious behavior, and take action when needed.
How Does Drosera Work?
At its core, Drosera operates on a simple yet powerful mechanism:
- Traps Collect Data – Scan blockchain transactions for anomalies.
- Analyze Data – The collected information is assessed to determine if an attack is happening.
- Trigger a Response – If the Trap detects malicious activity, it can execute a predefined response, such as pausing a contract or alerting security teams.
Key Components of Drosera:
- Trap – A smart contract that defines monitoring rules.
- Trap Config – A configuration file that specifies how the Trap operates.
- Operators – Entities that validate and execute security measures.
Together, these components allow Drosera to function as a decentralized security network, ensuring that smart contracts remain safe from attacks.
Getting Started with Drosera CLI
The Drosera Command Line Interface (CLI) is the primary tool for creating, managing, and monitoring Traps. It simplifies the process of integrating security automation into your blockchain applications.
To get started, spin up a boilerplate npx @drosera/create-drosera-app or set up one using forge init -t drosera-network/trap-foundry-template on your terminal.
Make sure you also have foundry installed, if you do not have it installed, set up foundry by running curl -L https://foundry.paradigm.xyz | bash.
Next, install bun
# install Bun
curl -fsSL https://bun.sh/install | bash
# install node modules
bun install
Set up a Vulnerable contract
Create a vunerable.sol in the src folder, for this guide we will create a smart contract that allows anyone to take ownership.
pragma solidity ^0.8.12;
contract VulnerableContract {
address public Owner;
// Constructor to set the initial owner
constructor(address _owner) {
Owner = _owner;
}
// Function to change the owner (no access control)
function changeOwner(address _newOwner) public {
Owner = _newOwner;
}
}
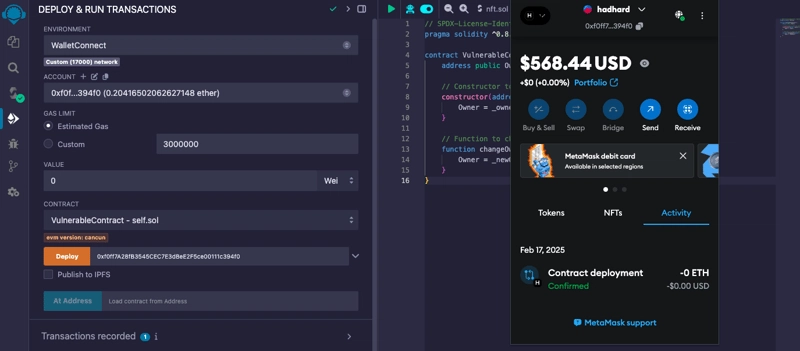
Copy the smart contract on vulnerable.sol and paste on remix, connect your wallet in this case i am using Metamask and if your do not have testnet faucet, fund it here.
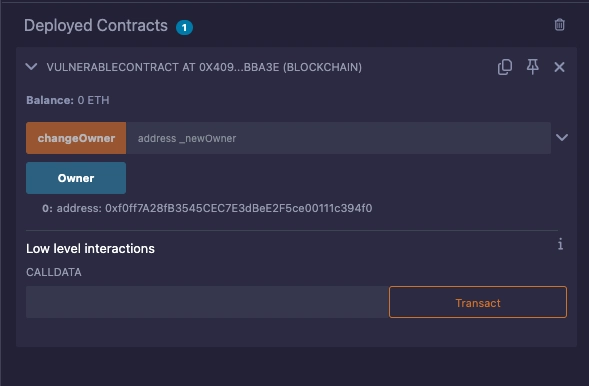
Deploy the contract and grab the deployed contract address, we will hardcode it into our trap.
Drosera Trap
Setting up a Drosera trap involves understanding the target contract’s logic. In this case, we’re monitoring for a change in ownership. Once that state change occurs, the trap detects it and automatically triggers an alert or on-chain response.
To get started, paste this on the HelloWorldTrap.sol file.
// SPDX-License-Identifier: UNLICENSED
pragma solidity ^0.8.12;
import {ITrap} from "drosera-contracts/interfaces/ITrap.sol";
import {VulnerableContract} from "./Vulnerable.sol";
contract HelloWorldTrap is ITrap {
// Hardcode the address of the deployed VulnerableContract
VulnerableContract public vulnerableContract = VulnerableContract(0x4096cdC78dD7b8f74E7228dbD9214bD919dbbA3E);
function collect() external view returns (bytes memory) {
// This function only reads state and does not modify it.
address currentOwner = vulnerableContract.Owner();
return abi.encode(currentOwner);
}
function shouldRespond(bytes[] calldata data) external pure returns (bool, bytes memory) {
if (data.length == 0) {
return (false, bytes(""));
}
address currentOwner = abi.decode(data[0], (address));
// Hardcoded expected owner: 0xf0ff7A28fB3545CEC7E3dBeE2F5ce00111c394f0
if (currentOwner != 0xf0ff7A28fB3545CEC7E3dBeE2F5ce00111c394f0) {
return (true, abi.encode("Owner has changed"));
}
return (false, bytes(""));
}
}
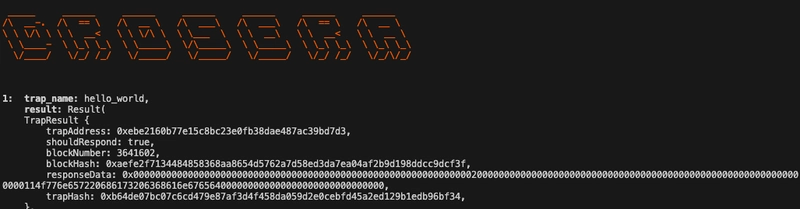
Our trap has two main functions collect() and shouldRespond(), both function have different usage which we will look into, in this trap we are checking the ownership at intervals to see if ownership changes in VulnerableContract.
How does the collect() and shouldRespond() operates?
collect() Function – Gathering Blockchain Data
The collect() function is responsible for retrieving the current owner of the VulnerableContract. It is marked as view, meaning it can read blockchain data but cannot modify it.
How It Works
- The function calls
Owner()on theVulnerableContractto get the current owner's address. - It encodes this address into a byte format, which allows it to be stored or processed later.
Why It Matters
- This function acts as a data collector, continuously fetching the contract’s owner information.
- The collected data is essential for tracking changes over time.
shouldRespond() Function – Detecting Ownership Changes
The shouldRespond() function is responsible for deciding whether a change has occurred in the contract’s ownership. Unlike collect(), this function is marked as pure, meaning it does not read blockchain data or modify any state—it only processes input data.
How It Works
- It first checks if there is any data available. If there isn’t, it returns
false, meaning no response is needed. - It extracts the most recent owner’s address from the encoded data.
- It compares this address with a hardcoded expected owner: 0xf0ff7A28fB3545CEC7E3dBeE2F5ce00111c394f0
If the current owner does not match the expected owner, the function returns
(true, abi.encode("Owner has changed"))
Thus signalling that an action should be triggered.
Why It Matters
- This function validates the collected data without accessing the blockchain, making it highly efficient.
- It prevents unnecessary responses, ensuring that actions are only triggered when a real change occurs.
- It plays a crucial role in security monitoring, helping detect potential ownership takeovers.
Finally, the HelloWorldTrap contract works as a watchdog for the VulnerableContract. Here’s how both functions work together.
-
collect()fetches and encodes the contract owner's address. -
shouldRespond()checks if the owner has changed and, if so, signals that an action is required.
Next, after populating the contract with our code, hardcode the contract address here.
VulnerableContract public vulnerableContract = VulnerableContract(0x4096cdC78dD7b8f74E7228dbD9214bD919dbbA3E);
By hardcoding the contract address, we ensure that HelloWorldTrap interacts with the specific deployed instance of VulnerableContract. If VulnerableContract is redeployed, this address must be updated manually.
Compile
Confirm your contract by compiling, run forge build
Drosera have updated their private key storage, you can either call the private key from the CLI or encode it in the .env file, you can no longer set it in the .toml file
private_key = "0d53..."
Make sure you have enough faucet in your address before continuing.
Deployment
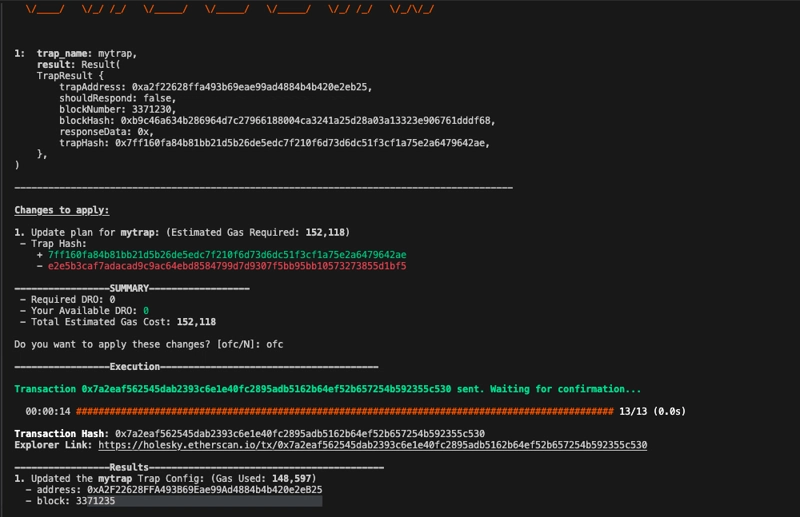
To deploy the trap, run the following commands:
#Compile the Trap
forge build
drosera apply --private-key 0d53...
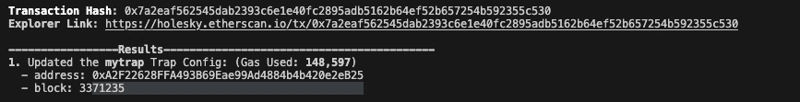
After successfully deploying the trap, the CLI will add an address field to the drosera.toml file.
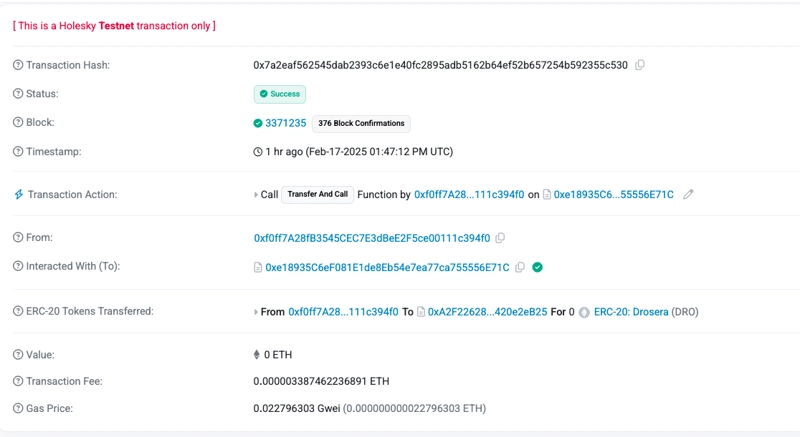
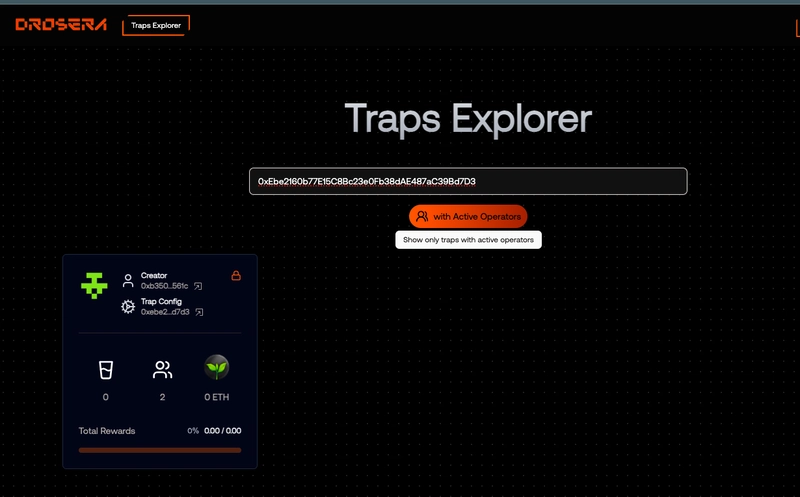
We can check out our deployed project using the Explorar link attached.
Click on the Explorar link to see the deployed contract.
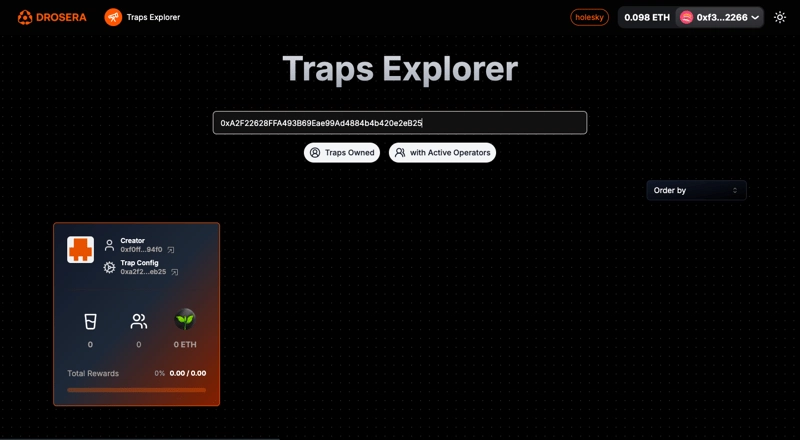
Next, copy your address and paste it on trap explorar and with this step your trap is live.
Getting Started With Operators
What is a Drosera Operator?
A Drosera Operator is an individual or entity that runs an Operator Node within the Drosera network. These nodes are responsible for executing Traps which are smart contracts that define conditions for detecting anomalies and triggering on-chain responses.
Operators play a crucial role in maintaining the security and efficiency of dApps by ensuring that Traps are executed promptly and accurately.
Why Become a Drosera Operator?
Becoming a Drosera Operator offers several benefits:
Contribution to Security: Operators enhance the security of the Ethereum ecosystem by actively monitoring and responding to potential exploits.
Incentives: Operators may receive rewards for their participation and the resources they contribute to the network.
-
Community Engagement: Public operators becomes part of a community focused on improving decentralised security infrastructure.
Prerequisites for Running an Operator Node
Before setting up an Operator Node, ensure you meet the following requirements:
- Operating System: A Linux-based system, preferably Ubuntu 22.04 or later.
-
Hardware Requirements:
- CPU: At least 2 cores.
- RAM: Minimum of 4 GB.
- Storage: At least 20 GB of available disk space.
Ethereum Node Access: Access to an Ethereum node is essential. While self-hosting a node is recommended for optimal performance, third-party services like Alchemy, Infura can be used.
-
Ethereum Account: An Ethereum account with a private key and sufficient ETH to cover transaction fees (Metamask) you can get ETH faucet from here.
Installing the Drosera Operator
There are two primary methods to install the Drosera Operator: using pre-built binaries or Docker images.
Method 1: Using Pre-built Binaries
- Download the Latest Release:
Visit the Drosera Operator GitHub to find the latest version, as at today, the latest version is v1.16.2.
- Select the Appropriate Binary:
Choose the binary compatible with your system. For most users, this will be the x86_64-unknown-linux-gnu version.
- Download and Extract the Binary:
Open a terminal and execute the following commands, replacing VERSION with the latest version number
cd ~
curl -LO https://github.com/drosera-network/releases/releases/download/vVERSION/drosera-operator-vVERSION-x86_64-unknown-linux-gnu.tar.gz
tar -xvf drosera-operator-vVERSION-x86_64-unknown-linux-gnu.tar.gz
- Verify the Installation:
Run the following command to check the installed version:
./drosera-operator --version
Ensure the output matches the version you downloaded.
- (Optional) Move the Binary to a Directory in Your PATH:
To make the drosera-operator command accessible from any terminal session:
sudo cp drosera-operator /usr/bin
Method 2: Using Docker
- Pull the Drosera Operator Docker Image:
Execute the following command to download the latest Docker image:
docker pull ghcr.io/drosera-network/drosera-operator:latest
- Verify the Docker Image:
Run the following command to ensure the image is functioning correctly:
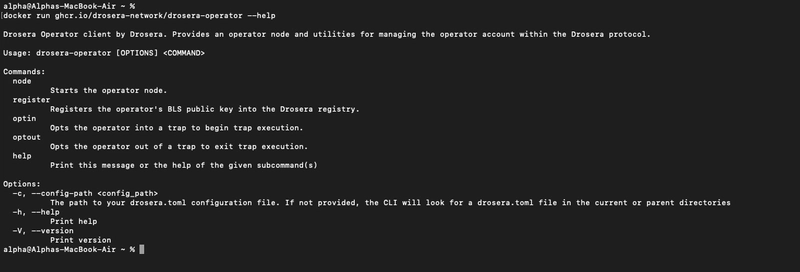
docker run ghcr.io/drosera-network/drosera-operator --help
Registering as an Operator
Before running the Operator Node, you must register your Ethereum account with the Drosera network.
drosera-operator register --eth-rpc-url --eth-private-key
This command registers your account by submitting your BLS public key to the Drosera contracts.
- Execute the Registration Command:
Replace
Running the Operator Node
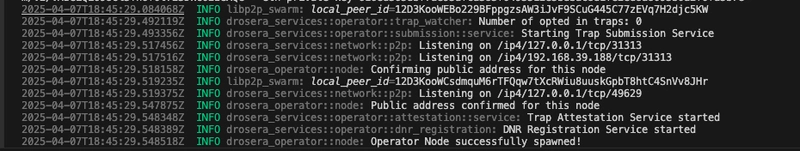
After registration, start the Operator Node with the following command:
drosera-operator node --eth-rpc-url --eth-private-key
If configured correctly, you should see a confirmation message indicating the node has started successfully.
Configuring the Operator Node
The Operator Node can be configured using command-line arguments, a drosera.toml configuration file, or environment variables. The order of precedence is:
- Command-line arguments
- drosera.toml` configuration file
- Environment variables
Example Configuration Using **drosera.toml**
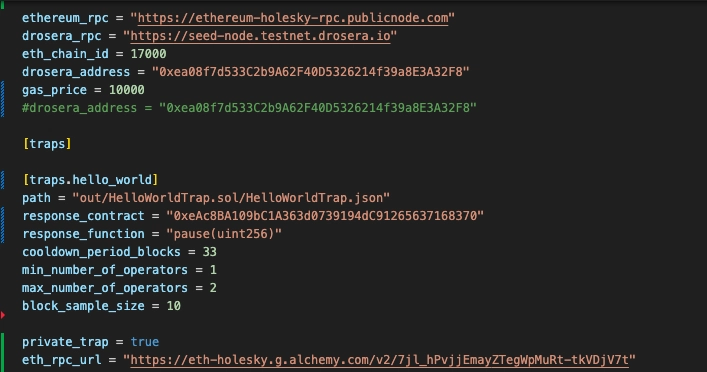
Open your drosera.toml file and add the eth_rpc_url command to it.
eth_rpc_url = ""
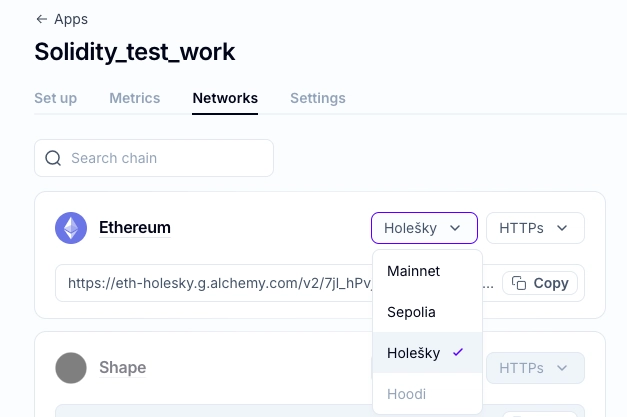
To set up an RPC url, you can create an account with Alchemy, set up your app and copy the RPC from the holesky testnet.
For security reasons you can no longer add the eth_private_key to the drosera.toml file, you can add it in the command line or in an .ENV file, but while this is still not advisable, encoding and hashing it with a key is more secure but for the sake of simplicity, we would use the CLI.
Start the node.
drosera-operator node --eth_private_key
The node will use the settings specified in the drosera.toml file.
Waitlisting your address
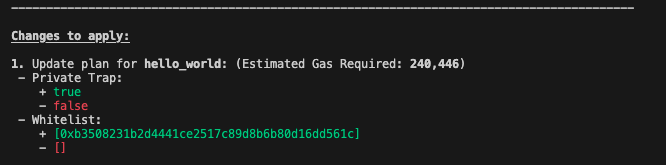
Drosera have two kinds of operators, Private operators which can be anyone whitelisted by the contract owner.
private_trap = true
whitelist = ["0xB3508231b2d4441cE2517C89D8B6b80d16Dd561C"]
And public groups. To get whitelisted into the Public groups where you can opt into any public trap, you must be a professional node operator as this groups are whitelisted by the Drosera team.
Next let go see our deployed trap, go to app.drosera.io and paste the trap address.
Hydrating, Dryrunning, and Monitoring Traps in Drosera
While Operators form the muscle behind Drosera’s automated security infrastructure, they are only as effective as the Traps they respond to. In this section, we’ll break down three essential concepts for Trappers and Operator maintainers: hydrating traps, dryrunning traps, and monitoring operator metrics.
If you’re building or maintaining secure dApps with Drosera, these tools are the difference between passive alerting and active, on-chain intervention.
Hydrating a Trap
Once a trap has been created and deployed on-chain, it doesn’t just sit there waiting to be useful. It needs to be hydrated — a process that streams rewards to Operators who monitor and act on that trap.
In other words, hydration turns a static contract into a living, incentivized security monitor.
How Hydration Works
When you hydrate a trap, you fund it with $DRO tokens. These tokens are distributed to Operators over time, across three reward streams:
Passive Rewards: Given to all Operators who’ve opted into the trap, proportionally and consistently.
Active Rewards: A bonus pool distributed based on participation in actual trap responses. The first Operator to react gets the lion’s share, but others who co-sign or contribute still receive a portion.
Staking Rewards: Sent to the protocol’s staking contract, rewarding DRO stakers and reinforcing network-wide health.
The duration of a hydration stream is fixed (30 days) and can be started by anyone, not just the trap creator. This encourages community engagement in maintaining high-priority traps.
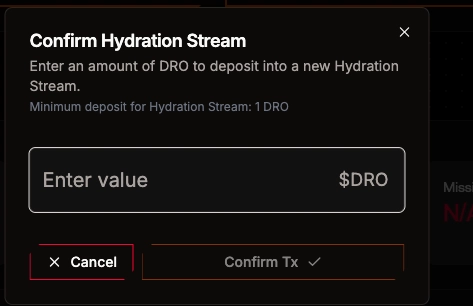
Example: Hydrating via CLI
Assuming you’ve deployed a trap and Operators have opted in, you can hydrate it like this:
drosera hydrate \
--trap-address 0xYourTrapAddress \
--dro-amount 1000
Or on the GUI.
Behind the scenes, this spins up a stream contract that will drip $DRO tokens to the trap for 30 days. Operators listening to this trap now have financial incentive to keep it live and responsive.
This mechanism helps shift away from altruistic monitoring toward market-driven security.
Dryrunning a Trap
Before hydrating or promoting a trap to mainnet, you’ll want to test its behavior without risking real-world consequences. That’s where dryrunning comes in.
Dryrunning lets you simulate what would happen if a trap were triggered — without executing any actual on-chain transactions or altering contract state.
Why Dryrun?
- Validate your trap logic
- Test with mock parameters or fake data
- Ensure your response contract behaves as expected
- Avoid wasting gas during development
This step is crucial, especially when writing complex detection logic or experimenting with multi-signature claim contracts.
Example: Dryrun a Live Trap
Here’s a basic command to simulate your trap
drosera dryrun \
--trap-address 0xYourTrapAddress
This command will return a full trace of what the trap would do, including:
- Whether it would be triggered
- What calldata would be constructed
- Which contract functions would be called
- Any revert reasons or execution failures
Advanced Use
In local development, you can also run dryruns against a forked mainnet environment or a local Hardhat node, giving you precise control over state and conditions.
Dryruns are fully reproducible and deterministic, making them ideal for CI testing of new trap versions.
Operator Metrics: Observability for Reliability
Running an Operator node isn't a fire-and-forget job. Like any production-grade infrastructure, it needs monitoring, observability, and logging.
Drosera exposes a metrics endpoint that gives you real-time insight into your node’s performance and behavior.
Accessing the Metrics
Once your Operator node is running, navigate to:
http://localhost:9090/metrics
This endpoint is Prometheus-compatible, meaning it’s ready to be scraped, graphed, and alerted on using your favorite DevOps stack.
What You Can Track
Here are just a few of the key metrics you’ll want to monitor:
-
drosera_operator_executed_traps_total: Total number of traps executed by the node. -
drosera_operator_opted_in_traps: How many traps the Operator has opted into. -
drosera_operator_error_count: Number of execution errors — spikes here might indicate RPC issues or contract bugs. -
drosera_operator_claim_submission_latency_seconds: Time taken to submit a claim after a trap fires — lower is better.
Example: Setting up with Prometheus
Create a prometheus.yml config like so:
scrape_configs:
- job_name: 'drosera_operator'
static_configs:
- targets: ['localhost:9090']
Then you can visualize your Operator node's behavior in real-time using Grafana or similar.
This monitoring stack transforms your node from a black box into a fully observable system, making it easier to
- Debug failed trap executions
- Measure response times
- Prove SLA-level reliability
Conclusion
Drosera is an on-chain, programmable defense system that brings real-time security automation to decentralized applications. It enables developers to create custom “traps” that detect and respond to suspicious behavior, while incentivizing Operators to monitor and execute these traps through token rewards.
By combining logic, automation, and economics, Drosera turns smart contracts into self-defending systems—reducing human overhead and increasing resilience in Web3 infrastructure.
It’s not just about alerts—it’s about on-chain reaction at the speed of threat.