Context-Based Access Control and Zero Trust: Key Insights from the CSA White Paper
Introduction Cloud Security Alliance (CSA)released a white paper on Context-Based Access Control (CBAC) and its role in advancing Zero Trust security models. The paper underscores the necessity of shifting from static, trust-based access control to real-time, adaptive authentication that evaluates risk dynamically, and Pomerium was highlighted as a key player in the CBAC space. We’ll break down the white paper’s key findings and explore how Pomerium aligns with this modern security framework. Why Traditional Access Controls Fall Short Historically, access control has been based on predefined roles and entitlements. The Role-Based Access Control (RBAC) model assigns permissions to roles rather than individual users, simplifying management but failing to adapt to real-time threats. Attribute-Based Access Control (ABAC) improves on RBAC by considering user attributes, but it still lacks dynamic risk assessment and real-time adaptability. The CSA paper highlights how modern identity-based attacks, such as credential theft and lateral movement, exploit these traditional models. Attackers can obtain valid credentials and operate within an organization undetected, as access decisions are based on static rules rather than continuous evaluation. What is Context-Based Access Control (CBAC)? CBAC represents a paradigm shift in access control. Instead of granting access solely based on identity or static attributes, CBAC evaluates real-time contextual signals to determine whether a request should be approved. These signals can include: User behavior: Is the user accessing resources in a typical pattern? Device health: Is the device compliant with security policies? Location & network conditions: Is the request coming from a familiar or risky location? Time & frequency: Is access being requested at an unusual time or with an abnormal frequency? By continuously analyzing these factors, CBAC minimizes implicit trust and ensures that every access request is assessed based on current risk factors rather than static policies. Read more about CBAC vs. RBAC vs. ABAC, the CBAC Maturity Model, and Pomerium's role as a zero trust, context-aware access solution on our blog.
Introduction
Cloud Security Alliance (CSA)released a white paper on Context-Based Access Control (CBAC) and its role in advancing Zero Trust security models. The paper underscores the necessity of shifting from static, trust-based access control to real-time, adaptive authentication that evaluates risk dynamically, and Pomerium was highlighted as a key player in the CBAC space.
We’ll break down the white paper’s key findings and explore how Pomerium aligns with this modern security framework.
Why Traditional Access Controls Fall Short
Historically, access control has been based on predefined roles and entitlements. The Role-Based Access Control (RBAC) model assigns permissions to roles rather than individual users, simplifying management but failing to adapt to real-time threats. Attribute-Based Access Control (ABAC) improves on RBAC by considering user attributes, but it still lacks dynamic risk assessment and real-time adaptability.
The CSA paper highlights how modern identity-based attacks, such as credential theft and lateral movement, exploit these traditional models. Attackers can obtain valid credentials and operate within an organization undetected, as access decisions are based on static rules rather than continuous evaluation.
What is Context-Based Access Control (CBAC)?
CBAC represents a paradigm shift in access control. Instead of granting access solely based on identity or static attributes, CBAC evaluates real-time contextual signals to determine whether a request should be approved. These signals can include:
- User behavior: Is the user accessing resources in a typical pattern?
- Device health: Is the device compliant with security policies?
- Location & network conditions: Is the request coming from a familiar or risky location?
- Time & frequency: Is access being requested at an unusual time or with an abnormal frequency? By continuously analyzing these factors, CBAC minimizes implicit trust and ensures that every access request is assessed based on current risk factors rather than static policies.
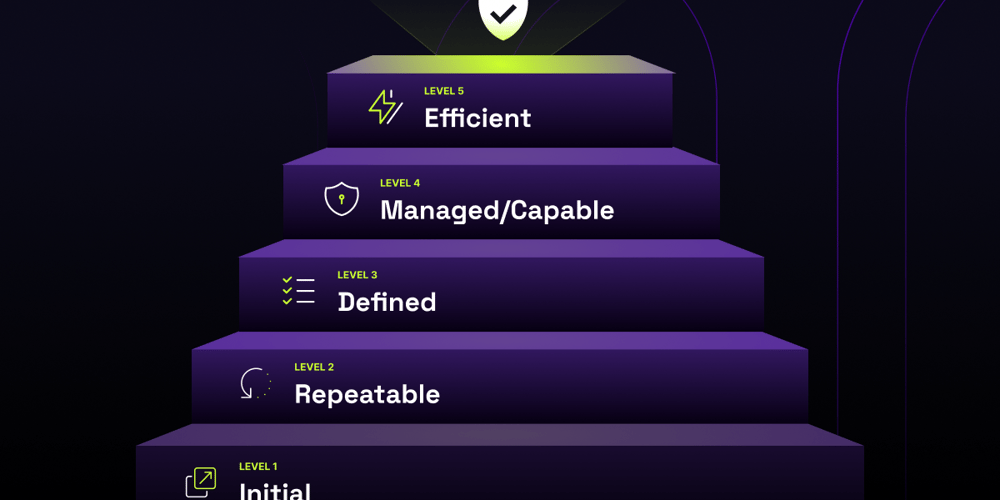
Read more about CBAC vs. RBAC vs. ABAC, the CBAC Maturity Model, and Pomerium's role as a zero trust, context-aware access solution on our blog.
















_Yuri_Arcurs_Alamy.jpg?#)



















![Watch a SpaceX rocket launch Crew-10 relief mission March 14 for NASA astronauts on ISS after delay [updated]](https://cdn.mos.cms.futurecdn.net/TBuLj3rJngaWrbyogNud9H.jpg?#)