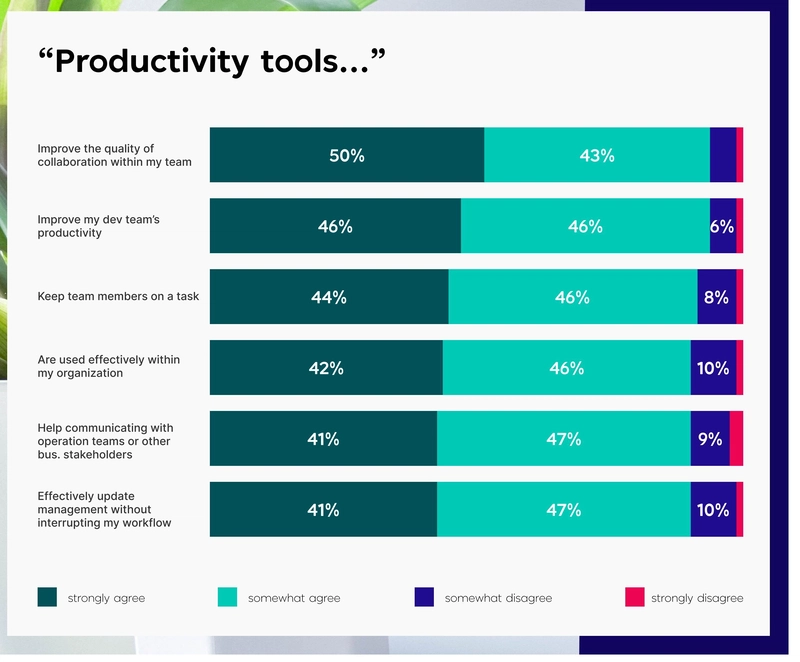
Access Control and Permission Management of ohpm-repo in HarmonyOS Next
During the development of HarmonyOS Next, the ohpm-repo private repository stores a large amount of important code and dependency packages, and its security is of vital importance. Reasonable access control and permission management strategies can effectively prevent malicious attacks and ensure the security of the private repository's data. Below, I will introduce in detail the access control strategies of ohpm-repo, combining practical usage experience. How to Manage User Permissions? System Administrators System administrators have the highest level of permissions and are responsible for the management and maintenance of the entire ohpm-repo system. They can perform system-level configurations, such as modifying database connection information and setting the storage method. In terms of user management, system administrators can create and delete user accounts and adjust the permissions of any user. For example, in an internal development environment of a company, system administrators can create accounts for newly joined developers according to project requirements and assign appropriate permissions. At the same time, system administrators can also adjust the global settings of the repository, such as setting the size limit for packages that can be uploaded and enabling or disabling certain functional modules. Ordinary Users Ordinary users are usually members of the development team, and their permissions are relatively restricted. The main operations of ordinary users are to download and use the packages in the repository. They can use the ohpm command in their own development environment to download the required dependency packages from the repository according to project needs. However, ordinary users do not have the permissions to upload and delete packages, nor can they perform system configuration and user management operations. This is to ensure the stability and security of the repository data and prevent accidental operations or malicious uploads. Organization Administrators Organization administrators are responsible for managing the packages and users under a specific organization. They can upload, delete, and manage packages within their own organization. For example, the organization administrator of a certain business department can upload the internal library developed by the department for use by the developers within the department. At the same time, organization administrators can manage the users within the organization, including adding and deleting users and adjusting the permissions of users within the organization. However, organization administrators cannot operate on the resources of other organizations and do not have system-level configuration permissions. AccessToken Authentication Mechanism How to Generate When a user logs in to the ohpm-repo private repository management address, the system will generate a unique AccessToken for the user. This Token is an encrypted string that contains key data such as the user's identity information and permission level. For example, after a user logs in with a username and password, the server will verify the user's identity information. After the verification is passed, it will generate the corresponding AccessToken according to the user's permission level and return it to the client. How to Configure In the configuration file of ohpm-repo, the relevant parameters of the AccessToken need to be configured. For example, the expiration time of the Token can be set to avoid the security risks caused by a long-term valid Token. In the config.yaml file, the following configuration can be added: token: expiration_time: 3600 # Token expiration time, in seconds At the same time, information such as the encryption algorithm and key of the Token can also be configured to ensure the security of the Token. How to Manage Tokens of Different Levels Users of different levels will be assigned Tokens of different levels. The Token of a system administrator has the highest permissions and can access and operate all functions of the system. The Token of an organization administrator can only be used for operations within the organization to which they belong. The Token of an ordinary user can only be used for downloading packages. On the server side, the user's request will be verified and authorized according to the permission information contained in the Token. If the user's Token does not have sufficient permissions, the server will reject the request. Access Control Optimization: How to Prevent Malicious Requests? Limiting User Access Frequency To prevent malicious users from attacking the repository through frequent requests, the access frequency of users can be limited. In the server-side code of ohpm-repo, an access frequency limiting module can be implemented. For example, each user can be set to be allowed to initiate a ma
During the development of HarmonyOS Next, the ohpm-repo private repository stores a large amount of important code and dependency packages, and its security is of vital importance. Reasonable access control and permission management strategies can effectively prevent malicious attacks and ensure the security of the private repository's data. Below, I will introduce in detail the access control strategies of ohpm-repo, combining practical usage experience.
How to Manage User Permissions?
System Administrators
System administrators have the highest level of permissions and are responsible for the management and maintenance of the entire ohpm-repo system. They can perform system-level configurations, such as modifying database connection information and setting the storage method. In terms of user management, system administrators can create and delete user accounts and adjust the permissions of any user. For example, in an internal development environment of a company, system administrators can create accounts for newly joined developers according to project requirements and assign appropriate permissions. At the same time, system administrators can also adjust the global settings of the repository, such as setting the size limit for packages that can be uploaded and enabling or disabling certain functional modules.
Ordinary Users
Ordinary users are usually members of the development team, and their permissions are relatively restricted. The main operations of ordinary users are to download and use the packages in the repository. They can use the ohpm command in their own development environment to download the required dependency packages from the repository according to project needs. However, ordinary users do not have the permissions to upload and delete packages, nor can they perform system configuration and user management operations. This is to ensure the stability and security of the repository data and prevent accidental operations or malicious uploads.
Organization Administrators
Organization administrators are responsible for managing the packages and users under a specific organization. They can upload, delete, and manage packages within their own organization. For example, the organization administrator of a certain business department can upload the internal library developed by the department for use by the developers within the department. At the same time, organization administrators can manage the users within the organization, including adding and deleting users and adjusting the permissions of users within the organization. However, organization administrators cannot operate on the resources of other organizations and do not have system-level configuration permissions.
AccessToken Authentication Mechanism
How to Generate
When a user logs in to the ohpm-repo private repository management address, the system will generate a unique AccessToken for the user. This Token is an encrypted string that contains key data such as the user's identity information and permission level. For example, after a user logs in with a username and password, the server will verify the user's identity information. After the verification is passed, it will generate the corresponding AccessToken according to the user's permission level and return it to the client.
How to Configure
In the configuration file of ohpm-repo, the relevant parameters of the AccessToken need to be configured. For example, the expiration time of the Token can be set to avoid the security risks caused by a long-term valid Token. In the config.yaml file, the following configuration can be added:
token:
expiration_time: 3600 # Token expiration time, in seconds
At the same time, information such as the encryption algorithm and key of the Token can also be configured to ensure the security of the Token.
How to Manage Tokens of Different Levels
Users of different levels will be assigned Tokens of different levels. The Token of a system administrator has the highest permissions and can access and operate all functions of the system. The Token of an organization administrator can only be used for operations within the organization to which they belong. The Token of an ordinary user can only be used for downloading packages. On the server side, the user's request will be verified and authorized according to the permission information contained in the Token. If the user's Token does not have sufficient permissions, the server will reject the request.
Access Control Optimization: How to Prevent Malicious Requests?
Limiting User Access Frequency
To prevent malicious users from attacking the repository through frequent requests, the access frequency of users can be limited. In the server-side code of ohpm-repo, an access frequency limiting module can be implemented. For example, each user can be set to be allowed to initiate a maximum of 10 requests within one minute. When the number of requests from a user exceeds this limit, the server will reject subsequent requests and return the corresponding error message. This can effectively prevent malicious behaviors such as brute force cracking and traffic brushing.
Log Monitoring
Log monitoring is an important means of detecting and handling malicious requests. Ohpm-repo will record all operation information of users, including the time of the request, the interface of the request, and the parameters of the request. By conducting real-time monitoring and analysis of these log information, abnormal request patterns can be discovered in a timely manner. For example, if an IP address initiates a large number of identical requests within a short period of time, it is likely to be a malicious attack behavior. Log analysis tools (such as the ELK Stack) can be used to collect, store, and analyze the logs, and discover and handle potential security threats in a timely manner.
Blacklist Management
For users or IP addresses that are confirmed to have malicious behaviors, they can be added to the blacklist. On the server side, when a request is received, it will first check whether the source of the request is in the blacklist. If it is, the request will be directly rejected. The blacklist can be added to the configuration file of ohpm-repo, or a blacklist table can be maintained in the database. Regularly update and clean up the blacklist to ensure its effectiveness.
Through the above access control and permission management strategies, the security of the ohpm-repo private repository can be effectively improved, malicious attacks can be prevented, and the data security and development efficiency of the development team can be ensured. In practical applications, these strategies need to be flexibly adjusted and optimized according to specific business needs and security requirements.