Why can deleted files be recovered?
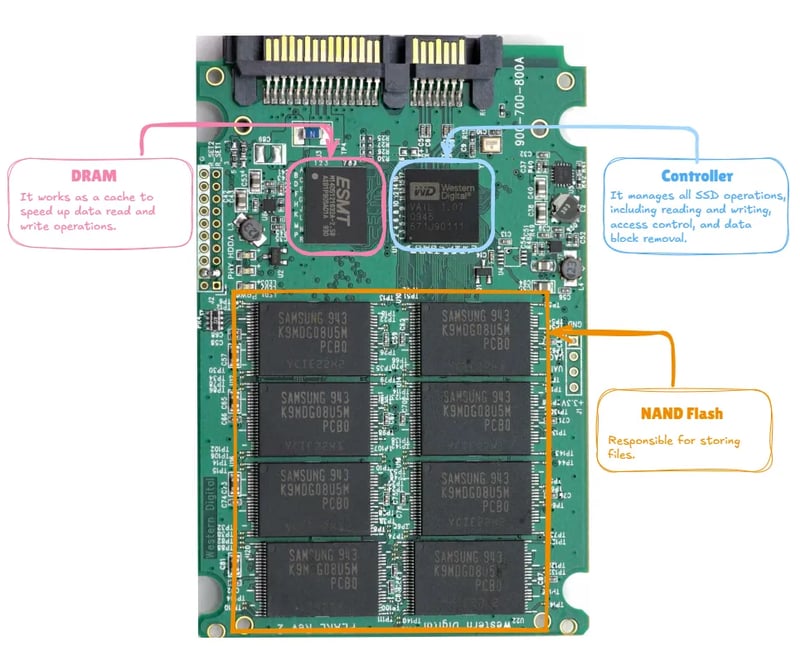
Understand how deleted data on SSDs can be recovered and the role of the TRIM command, encryption, and forensic techniques used in digital investigations. Components of an SSD Solid State Drives (SSDs) are made up of module(s): ➡️ DRAM (Cache): speeds up read/write operations; ➡️ Nand Memory: allows data storage; ➡️ Controller: Manages all SSD operations What is DRAM? DRAM is a type of volatile memory that temporarily stores data. It is made up of cells that store bits. This DRAM module is used as a cache to temporarily store data being read or written, improving the device’s access speed and efficiency. The Controller’s Role The SSD controller is a chip that manages data reading and writing to NAND flash memory cells. This component is vital for the device’s performance and durability, and it contains the Flash Translation Layer (FTL). The main functions of FTL are: Translate commands received from the operating system to flash memory; Maintain a mapping between the logical address and the physical address of the data; Perform garbage collection on memory blocks; and Distribute SSD operations among memory blocks to reduce wear. This function is known as Wear Leveling. How NAND Memory Works NAND Memory is a non-volatile memory technology that stores data in memory cells organized in a matrix structure. NAND memory is made up of numerous memory cells that are organized into pages and blocks. Memory Cells Storage cells are organized in layers, similar to a ream of A4 paper. Within each cell, there are several blocks responsible for effectively storing file data. These components have a limited lifespan. Each time information is created (or modified, or deleted), this lifespan decreases. To address this issue, the FTL (Flash Translation Layer) distributes operations evenly, preventing certain blocks from wearing out faster than others. The operating system does not have direct access to this part of the SSD; for this, the use of the Flash Translation Layer (FTL) is required, which facilitates integration between them. Why Can Data Be Recovered? When a file is deleted, the operating system signals to the FTL (Flash Translation Layer) that the space used by the file can be reused for another. The FTL marks the spaces as free, but the bits of information remain in the cell until they are overwritten later. This strategy, in addition to preventing wear — as already explained — also improves performance. Erasing entire blocks is more efficient than erasing individual cells. Therefore, after you delete a file from your SSD, forensic experts can attempt to directly access the memory cells using specific devices to recover the deleted data. An SSD with many gigabytes or terabytes that is lightly used can retain deleted information for years. How to Ensure Permanent Deletion? When working with personal data (such as contracts, SSH keys, and database backups), you must take specific precautions with files — particularly if your company needs to comply with the General Data Protection Law. ❓ I used the Eraser, BitRaser, Shred apps, etc. Congratulations!! Some of these apps work on 90s-era HDDs. On SSDs, they still don’t permanently delete the file. Back in the early 1990s, computer scientist Peter Gutmann created an algorithm to overwrite empty spaces on HDDs. The goal was to rewrite the same file 35 times to prevent the original content from being recovered. However, this technique does not work on modern storage devices. ❓ How can I securely delete files containing my data, then? The National Security Agency (NSA) recommends that storage devices be shredded into pieces no larger than 2mm. This is an extreme measure, but there are other alternatives. The TRIM Command The TRIM command is an instruction sent by the operating system to the SSD, indicating which data blocks are no longer in use and can be erased. Once TRIM is executed, recovering deleted files becomes much more difficult — though not impossible. Attention! Not every SSD and not every operating system supports this instruction. Software Encryption Full disk encryption aims to make data access more difficult, ensuring that the information stored on the device is accessible only to authorized users, such as those who have the password, a key file, or a hardware authentication device (like a Yubikey, for example). Windows, for instance, uses BitLocker to implement full disk encryption. However, this does not guarantee that the data is completely inviolable. The study “Is My Password Strong Enough?: A Study on User Perception in The Developing World” revealed that many users choose predictable and weak passwords, such as personal information and common patterns. Password reuse is also a significant issue, with 69% of participants admitting to this practice. Hardware Encryption This is a technique
Understand how deleted data on SSDs can be recovered and the role of the TRIM command, encryption, and forensic techniques used in digital investigations.
Components of an SSD
Solid State Drives (SSDs) are made up of module(s):
➡️ DRAM (Cache): speeds up read/write operations;
➡️ Nand Memory: allows data storage;
➡️ Controller: Manages all SSD operations
What is DRAM?
DRAM is a type of volatile memory that temporarily stores data. It is made up of cells that store bits.
This DRAM module is used as a cache to temporarily store data being read or written, improving the device’s access speed and efficiency.
The Controller’s Role
The SSD controller is a chip that manages data reading and writing to NAND flash memory cells. This component is vital for the device’s performance and durability, and it contains the Flash Translation Layer (FTL).
The main functions of FTL are:
- Translate commands received from the operating system to flash memory;
- Maintain a mapping between the logical address and the physical address of the data;
- Perform garbage collection on memory blocks; and
- Distribute SSD operations among memory blocks to reduce wear. This function is known as Wear Leveling.
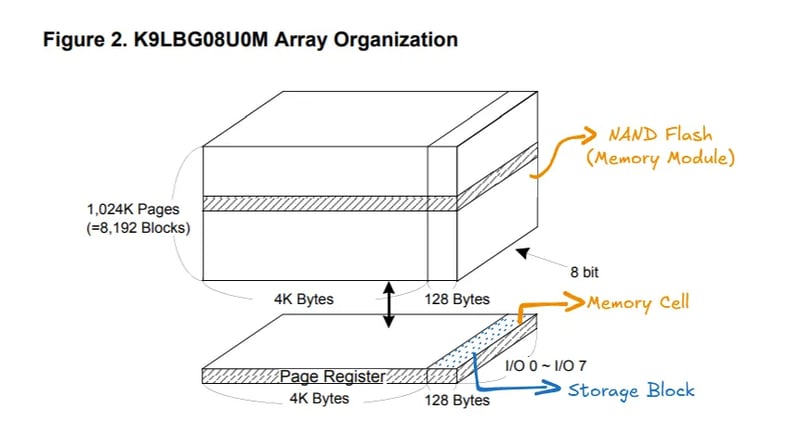
How NAND Memory Works
NAND Memory is a non-volatile memory technology that stores data in memory cells organized in a matrix structure. NAND memory is made up of numerous memory cells that are organized into pages and blocks.
Memory Cells
Storage cells are organized in layers, similar to a ream of A4 paper. Within each cell, there are several blocks responsible for effectively storing file data.
These components have a limited lifespan. Each time information is created (or modified, or deleted), this lifespan decreases.
To address this issue, the FTL (Flash Translation Layer) distributes operations evenly, preventing certain blocks from wearing out faster than others.
The operating system does not have direct access to this part of the SSD; for this, the use of the Flash Translation Layer (FTL) is required, which facilitates integration between them.
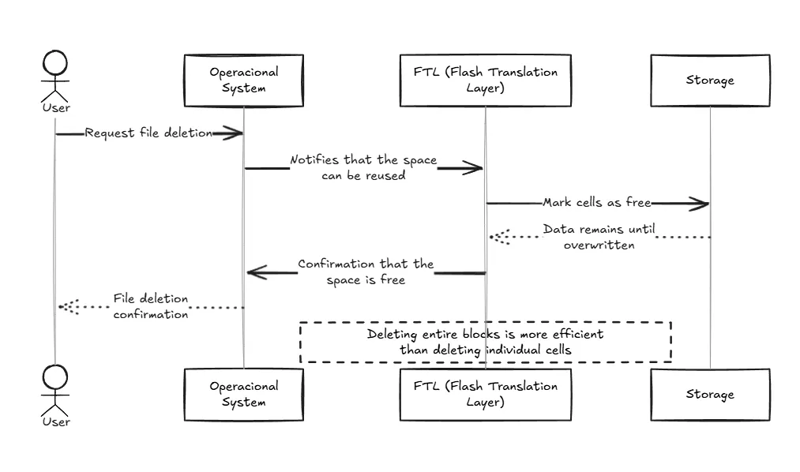
Why Can Data Be Recovered?
When a file is deleted, the operating system signals to the FTL (Flash Translation Layer) that the space used by the file can be reused for another. The FTL marks the spaces as free, but the bits of information remain in the cell until they are overwritten later.
This strategy, in addition to preventing wear — as already explained — also improves performance. Erasing entire blocks is more efficient than erasing individual cells.
Therefore, after you delete a file from your SSD, forensic experts can attempt to directly access the memory cells using specific devices to recover the deleted data. An SSD with many gigabytes or terabytes that is lightly used can retain deleted information for years.
How to Ensure Permanent Deletion?
When working with personal data (such as contracts, SSH keys, and database backups), you must take specific precautions with files — particularly if your company needs to comply with the General Data Protection Law.
❓ I used the Eraser, BitRaser, Shred apps, etc.
Congratulations!! Some of these apps work on 90s-era HDDs. On SSDs, they still don’t permanently delete the file.
Back in the early 1990s, computer scientist Peter Gutmann created an algorithm to overwrite empty spaces on HDDs. The goal was to rewrite the same file 35 times to prevent the original content from being recovered. However, this technique does not work on modern storage devices.
❓ How can I securely delete files containing my data, then?
The National Security Agency (NSA) recommends that storage devices be shredded into pieces no larger than 2mm. This is an extreme measure, but there are other alternatives.
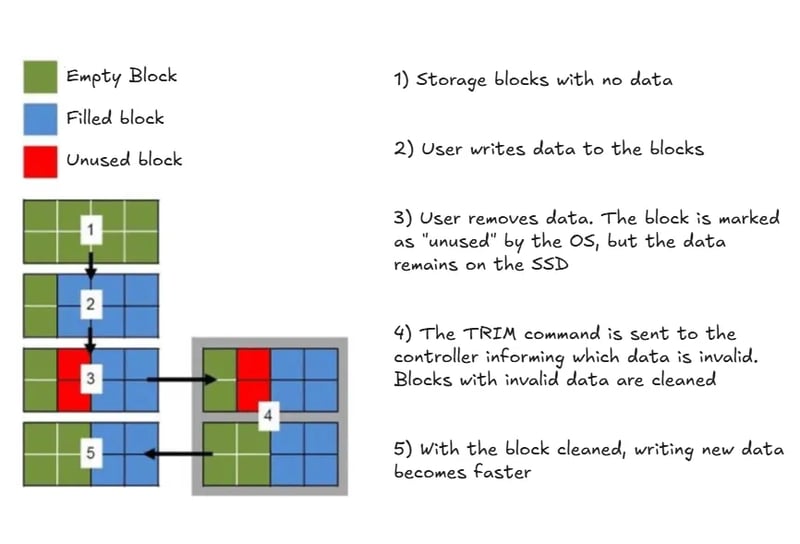
The TRIM Command
The TRIM command is an instruction sent by the operating system to the SSD, indicating which data blocks are no longer in use and can be erased. Once TRIM is executed, recovering deleted files becomes much more difficult — though not impossible.
Attention! Not every SSD and not every operating system supports this instruction.
Software Encryption
Full disk encryption aims to make data access more difficult, ensuring that the information stored on the device is accessible only to authorized users, such as those who have the password, a key file, or a hardware authentication device (like a Yubikey, for example).
Windows, for instance, uses BitLocker to implement full disk encryption. However, this does not guarantee that the data is completely inviolable.
The study “Is My Password Strong Enough?: A Study on User Perception in The Developing World” revealed that many users choose predictable and weak passwords, such as personal information and common patterns. Password reuse is also a significant issue, with 69% of participants admitting to this practice.
Hardware Encryption
This is a technique that uses dedicated components, such as encryption controllers and chips, to protect data stored on SSD devices. This approach offers advantages over software encryption, particularly when it comes to the difficulty of recovering data after deletion or destruction of the device. However, the cost of such devices may not be attractive to most people.
On the market, there are some devices like the IronKey Vault Privacy 80 8TB External SSD, which can cost up to $900; and the ORICO 2TB mSATA SSD for internal use, which can cost $130.
It’s not a paid post, but it could be