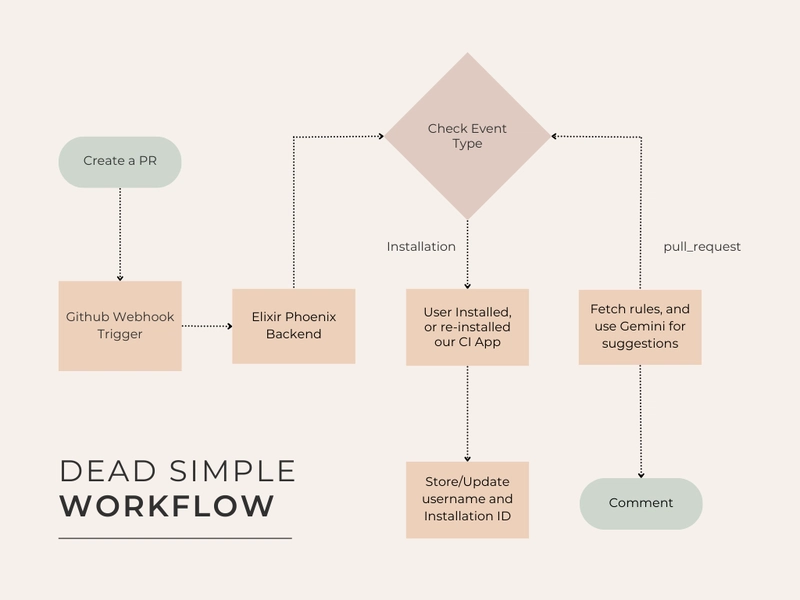
What is Security as Code (SaC)?
As organizations adopt rapid DevOps cycles and cloud-native applications, traditional, manual security methods are no longer sufficient. Security as Code (SaC) addresses this challenge by embedding security directly into the development lifecycle through code, making protection proactive, repeatable, and automated. Defining Security as Code Security as Code (SaC) is the practice of defining and managing security policies, controls, and configurations using code. Instead of waiting until deployment to run security checks, SaC brings those checks earlier—into development pipelines. By treating security like any other part of application development, teams can automate enforcement, test against defined rules, and ensure consistency across cloud, infrastructure, and CI/CD processes. SaC transforms compliance, vulnerability scanning, and policy enforcement into programmable assets versioned alongside application code. Building Blocks of SaC Infrastructure as Code (IaC): With tools like Terraform and CloudFormation, infrastructure is scripted and secured at the provisioning level. Policy as Code: Security policies are written as code using policy engines like OPA, enabling enforcement at scale across environments. Automated Security Testing: Static analysis, container scans, and code audits are embedded into CI/CD pipelines to detect flaws pre-deployment. Secrets Management: Credentials and keys are centrally managed and securely injected into builds using services like Vault or AWS Secrets Manager. Compliance Automation: Security configurations are mapped to compliance requirements, offering a traceable path for audits and regulatory adherence. Why SaC Matters Proactive Risk Mitigation: Catch misconfigurations and vulnerabilities before they reach production. Consistency Across Environments: Eliminate gaps between development, staging, and production. Faster, Safer Deployments: Automate security gates without slowing down delivery. Scalable and Repeatable Security: Apply the same controls across hundreds of microservices or environments with ease. Audit-Ready Architecture: Maintain logs, artifacts, and test evidence to simplify compliance checks. Getting Started Organizations can begin by integrating SaC into high-priority pipelines, choosing appropriate tools, and gradually codifying their security standards. Promoting a security-aware culture and training developers are equally critical for adoption. Conclusion Security as Code enables teams to deliver secure applications at scale. By codifying and automating security, businesses can streamline DevSecOps, reduce risks, and confidently meet compliance demands—without compromising agility.


As organizations adopt rapid DevOps cycles and cloud-native applications, traditional, manual security methods are no longer sufficient. Security as Code (SaC) addresses this challenge by embedding security directly into the development lifecycle through code, making protection proactive, repeatable, and automated.
Defining Security as Code
Security as Code (SaC) is the practice of defining and managing security policies, controls, and configurations using code. Instead of waiting until deployment to run security checks, SaC brings those checks earlier—into development pipelines.
By treating security like any other part of application development, teams can automate enforcement, test against defined rules, and ensure consistency across cloud, infrastructure, and CI/CD processes. SaC transforms compliance, vulnerability scanning, and policy enforcement into programmable assets versioned alongside application code.
Building Blocks of SaC
- Infrastructure as Code (IaC): With tools like Terraform and CloudFormation, infrastructure is scripted and secured at the provisioning level.
- Policy as Code: Security policies are written as code using policy engines like OPA, enabling enforcement at scale across environments.
- Automated Security Testing: Static analysis, container scans, and code audits are embedded into CI/CD pipelines to detect flaws pre-deployment.
- Secrets Management: Credentials and keys are centrally managed and securely injected into builds using services like Vault or AWS Secrets Manager.
- Compliance Automation: Security configurations are mapped to compliance requirements, offering a traceable path for audits and regulatory adherence.
Why SaC Matters
- Proactive Risk Mitigation: Catch misconfigurations and vulnerabilities before they reach production.
- Consistency Across Environments: Eliminate gaps between development, staging, and production.
- Faster, Safer Deployments: Automate security gates without slowing down delivery.
- Scalable and Repeatable Security: Apply the same controls across hundreds of microservices or environments with ease.
- Audit-Ready Architecture: Maintain logs, artifacts, and test evidence to simplify compliance checks.
Getting Started
Organizations can begin by integrating SaC into high-priority pipelines, choosing appropriate tools, and gradually codifying their security standards. Promoting a security-aware culture and training developers are equally critical for adoption.
Conclusion
Security as Code enables teams to deliver secure applications at scale. By codifying and automating security, businesses can streamline DevSecOps, reduce risks, and confidently meet compliance demands—without compromising agility.