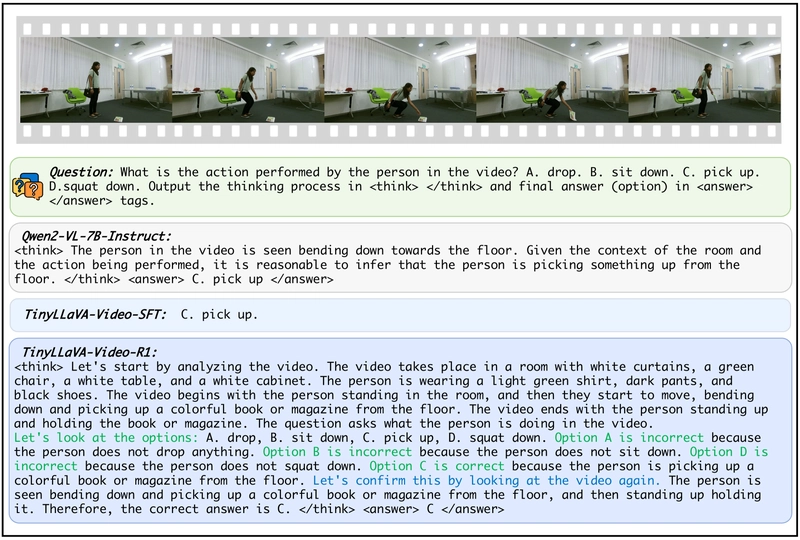
The Psychology of Social Engineering – What Security Leaders Should Know
Social engineering remains one of the most persistent threats to organizational security because it targets human psychology rather than technological vulnerabilities. Unlike conventional cyber threats that exploit technical weaknesses, social engineering manipulates the fundamental psychological traits that make us human. Understanding these psychological dimensions is critical for security leaders to implement better technical controls and […] The post The Psychology of Social Engineering – What Security Leaders Should Know appeared first on Cyber Security News.
.webp?#)
Social engineering remains one of the most persistent threats to organizational security because it targets human psychology rather than technological vulnerabilities.
Unlike conventional cyber threats that exploit technical weaknesses, social engineering manipulates the fundamental psychological traits that make us human.
Understanding these psychological dimensions is critical for security leaders to implement better technical controls and develop human-centered defense strategies.
The psychology behind why employees click suspicious links, share credentials, or allow unauthorized access forms the foundation of effective security leadership.
This understanding enables leaders to move beyond simply blaming user behavior to fostering genuine psychological resilience against increasingly sophisticated manipulation tactics.
Psychology of Social Engineering
Social engineers are masters of human psychology, expertly manipulating core psychological principles that have evolved throughout history.
These attackers exploit authority by impersonating executives or IT personnel, knowing that humans are conditioned to respond to authoritative requests with compliance.
They leverage scarcity and urgency by creating time-limited threats or opportunities, short-circuiting our rational decision-making processes in favor of quick, emotional responses.
Social proof, our tendency to look to others for behavioral guidance, becomes a weapon when attackers reference trusted colleagues or widespread organizational practices.
Familiarity bias is triggered when attacks mimic known brands or communication patterns, exploiting our tendency to lower defenses around seemingly familiar scenarios.
Fear is perhaps the most potent trigger, activating our fight-or-flight response and bypassing critical thinking. Meanwhile, reciprocity, our ingrained need to return favors, creates an obligation that attackers exploit.
For security leaders, recognizing these psychological vulnerabilities means acknowledging that even the most technically sophisticated security systems are only as strong as their human elements.
Common Attack Vectors and Their Psychological Components
Social engineering manifests through various attack vectors, each targeting specific psychological vulnerabilities while sharing common manipulation tactics. Understanding these connections helps leaders develop more effective defenses.
- Phishing attacks exploit authority and fear by masquerading as trusted entities (banks, executives, IT departments) and creating urgent scenarios requiring immediate action. When an employee receives an email from the CEO demanding an immediate transfer of funds, authority compliance and fear of consequences override cautious verification processes.
- Pretexting leverages our natural tendency to trust and help others by creating elaborate scenarios that establish credibility. These attacks succeed because humans naturally fill in missing information with assumptions, especially when the attacker appears knowledgeable about organizational details.
- Baiting operations exploit curiosity, greed, and reward-seeking behavior by offering something enticing: a free USB drive, exclusive content, or valuable downloads that contain malware or harvest credentials. This technique works because our desire for rewards often overrides security awareness.
- Quid pro quo attacks utilize reciprocity, offering assistance or benefits in exchange for information or access. When someone provides free IT support in exchange for login credentials, they exploit our psychological need to return perceived favors.
- Tailgating exploits social harmony and our reluctance to appear rude or confrontational. When someone follows an employee through a secure door, psychology makes challenging them uncomfortable, even when security protocols require it.
These attack vectors succeed not because employees lack intelligence but because they rely on deeply ingrained psychological responses that operate below conscious awareness.
Building Psychological Resilience
Creating psychological resilience against social engineering demands that security leaders adopt a fundamentally different approach to human security aspects.
Traditional security awareness training often fails because it focuses on rules and knowledge rather than addressing the underlying psychological vulnerabilities that social engineers exploit.
Effective security leaders understand that building true organizational resilience requires transforming automatic psychological responses through consistent practice, meaningful feedback, and environmental design.
This means developing training scenarios that deliberately trigger and redirect the psychological impulses exploited by attackers practicing the uncomfortable feeling of verifying a CEO’s unusual request, experiencing the social awkwardness of questioning a tailgater, or overriding the urgency of a fear-based message.
Leaders must create organizational cultures where security vigilance is valued over expedience, questioning unusual requests is rewarded rather than penalized, and security processes align with rather than fight against human psychology.
- Create psychological safety for security behaviors by publicly recognizing and rewarding employees who properly question suspicious communications or enforce access policies, even when doing so causes temporary inconvenience or delays.
- When the senior executive who gets appropriately challenged at the secure entrance congratulates rather than criticizes the employee, psychological safety for security behaviors increases throughout the organization.
- Implement continuous micro-training that targets specific psychological vulnerabilities through realistic simulations, moving beyond theoretical knowledge to practical response conditioning.
- These brief, frequent experiences should gradually increase in sophistication, preparing employees for the advanced psychological manipulation techniques used by professional social engineers.
Security leaders who understand and address the psychological foundations of social engineering transform their security culture from one of compliance to one of resilience.
By recognizing that human psychology remains simultaneously their greatest vulnerability and their most vigorous potential defense, leaders can develop strategies that work with rather than against fundamental human nature.
This psychological approach to security leadership doesn’t just prevent breaches. It builds organizational adaptability to continuously evolving threats.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
The post The Psychology of Social Engineering – What Security Leaders Should Know appeared first on Cyber Security News.