The Password Graveyard
Introduction "What if a hacker could access your entire digital life… with just one stolen cookie?" Sounds like sci-fi? Unfortunately, it’s not. Welcome to the world of Broken Authentication—a critical vulnerability where faulty login mechanisms, poor session handling, and weak token management give attackers the keys to the kingdom. Whether you're a developer, sysadmin, or cybersecurity enthusiast, understanding this vulnerability is essential in 2025, as breaches like those at Ticketmaster, Uber, and Colonial Pipeline have shown just how real the threat is. In this guide, we’ll break down how authentication failures occur, real-world attacks, how hackers exploit these flaws step-by-step, and what you can do to build secure, resilient authentication systems. Let's dive into the cracks of the digital gatekeeper. Understanding Broken Authentication What Is It, Really? Broken Authentication refers to design or implementation flaws in how a system confirms a user’s identity and manages sessions. Common culprits: Weak password policies Insecure session IDs Poor token management Missing or weak MFA It was formerly ranked #2 in the OWASP Top 10 (now called “Identification and Authentication Failures”) and remains the #2 risk in API security. Why It Matters More Than Ever Consequences of a breach:
Introduction
"What if a hacker could access your entire digital life… with just one stolen cookie?"
Sounds like sci-fi? Unfortunately, it’s not.
Welcome to the world of Broken Authentication—a critical vulnerability where faulty login mechanisms, poor session handling, and weak token management give attackers the keys to the kingdom. Whether you're a developer, sysadmin, or cybersecurity enthusiast, understanding this vulnerability is essential in 2025, as breaches like those at Ticketmaster, Uber, and Colonial Pipeline have shown just how real the threat is.
In this guide, we’ll break down how authentication failures occur, real-world attacks, how hackers exploit these flaws step-by-step, and what you can do to build secure, resilient authentication systems. Let's dive into the cracks of the digital gatekeeper.
Understanding Broken Authentication
What Is It, Really?
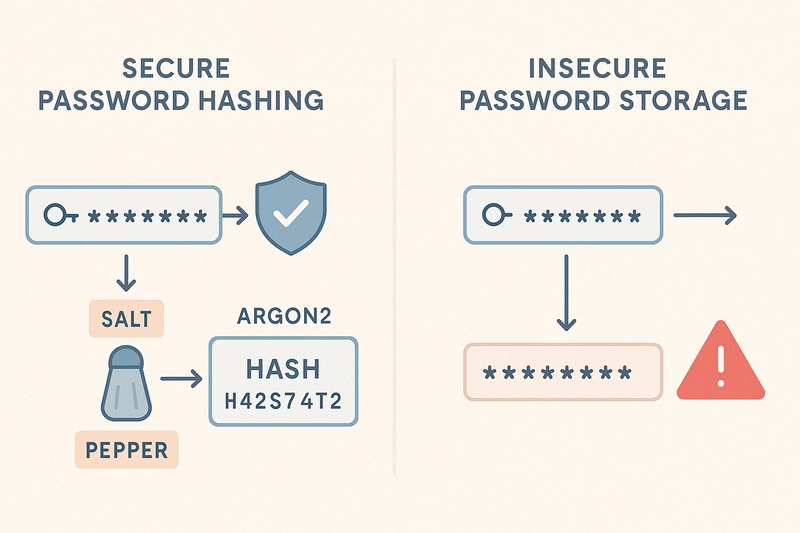
Broken Authentication refers to design or implementation flaws in how a system confirms a user’s identity and manages sessions. Common culprits:
- Weak password policies
- Insecure session IDs
- Poor token management
- Missing or weak MFA
It was formerly ranked #2 in the OWASP Top 10 (now called “Identification and Authentication Failures”) and remains the #2 risk in API security.
Why It Matters More Than Ever
Consequences of a breach: