Split-Horizon DNS on AdGuard: One Domain, Two Networks, Two IP Addresses
Split-Horizon DNS with AdGuard Home Let’s say you self-host an app on your home network. Your server’s local IP is 192.168.1.200, so you set app.example.com to point to that. Everything works fine—until you want to access it from outside your home. You set up a VPN (like Tailscale, WireGuard, or OpenVPN) so your clients and server can talk securely. The server now also has a VPN IP, like 100.64.50.50. You configure your devices to use your home AdGuard DNS over VPN. But here’s the problem: when you try to reach app.example.com over VPN, it still resolves to 192.168.1.200—a local IP that doesn’t work outside the LAN. So, you switch the DNS to return 100.64.50.50 instead. Great—VPN clients can now connect. But now what about your devices at home? Do they also need to connect through VPN all the time? Do you really want encrypted VPN traffic on your local LAN? Should you run two separate DNS servers and sync them? There’s a simpler way using split-horizon DNS with AdGuard Home. What’s Split-Horizon DNS? It’s when your DNS server returns different IP addresses depending on where the request comes from. For example: If you're on VPN → return VPN IP (100.64.50.50) If you're on home LAN → return local IP (192.168.1.200) ### How to Set It Up in AdGuard Home Log in to your AdGuard Home dashboard. Go to Filters → Custom Filtering Rules. Add these two rules: ||split.example.com^$dnsrewrite=NOERROR;A;100.64.50.50,client=100.0.0.0/8 ||split.example.com^$dnsrewrite=NOERROR;A;192.168.1.200,client=192.168.1.0/24 - The first rule responds with the VPN IP if the query comes from the Tailscale subnet (`100.0.0.0/8`). - The second rule responds with the local IP for devices on your home network (`192.168.1.0/24`).
Split-Horizon DNS with AdGuard Home
Let’s say you self-host an app on your home network. Your server’s local IP is 192.168.1.200, so you set app.example.com to point to that. Everything works fine—until you want to access it from outside your home.
You set up a VPN (like Tailscale, WireGuard, or OpenVPN) so your clients and server can talk securely. The server now also has a VPN IP, like 100.64.50.50. You configure your devices to use your home AdGuard DNS over VPN.
But here’s the problem: when you try to reach app.example.com over VPN, it still resolves to 192.168.1.200—a local IP that doesn’t work outside the LAN. So, you switch the DNS to return 100.64.50.50 instead.
Great—VPN clients can now connect. But now what about your devices at home? Do they also need to connect through VPN all the time? Do you really want encrypted VPN traffic on your local LAN? Should you run two separate DNS servers and sync them?
There’s a simpler way using split-horizon DNS with AdGuard Home.
What’s Split-Horizon DNS?
It’s when your DNS server returns different IP addresses depending on where the request comes from. For example:
- If you're on VPN → return VPN IP (
100.64.50.50) - If you're on home LAN → return local IP (
192.168.1.200) ### How to Set It Up in AdGuard Home
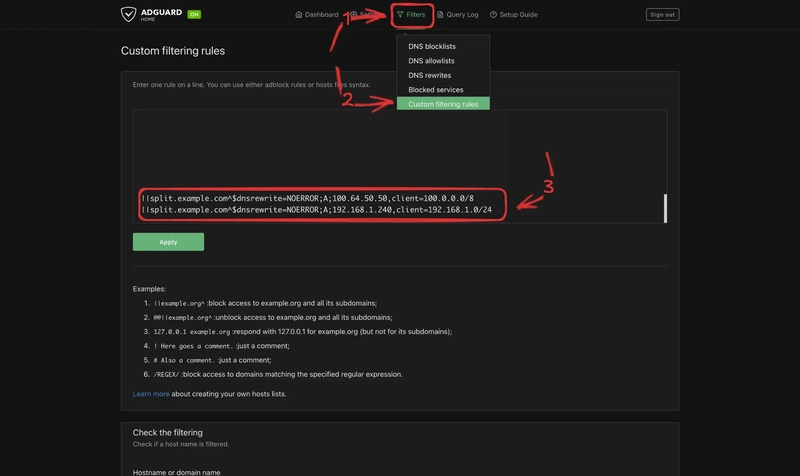
- Log in to your AdGuard Home dashboard.
- Go to Filters → Custom Filtering Rules.

-
Add these two rules:
||split.example.com^$dnsrewrite=NOERROR;A;100.64.50.50,client=100.0.0.0/8 ||split.example.com^$dnsrewrite=NOERROR;A;192.168.1.200,client=192.168.1.0/24
- The first rule responds with the VPN IP if the query comes from the Tailscale subnet (`100.0.0.0/8`).
- The second rule responds with the local IP for devices on your home network (`192.168.1.0/24`).