Solving TryHackMe's "Brains" Room: A complete Walktrough
Introduction TryHackMe's Brains room is a cybersecurity challenge that focuses on exploiting an authentication bypass vulnerability in TeamCity (CVE-2024-27198). This walkthrough will guide you through the attacker's perspective, where we gain access to the system, and the defender's perspective, where we analyze logs to track the attack. Step 1: Initial Reconnaissance Before diving into exploitation, we need to gather information about the target system. Running an Nmap Scan Start by scanning the target machine to identify open ports and services, i used the following code: nmap -A -sV -sS 10.10.155.253(YOUR_MACHINEIP) -T4 but you can have the same results as shown with this: nmap -A -T4 -p- 10.10.155.253(YOUR_MACHINEIP) Scan Results: | Port | Service | Version | | 22 | SSH | OpenSSH 8.4 | | 80 | HTTP | Apache 2.4 | | 50000 | TeamCity | Version 2023.11.4 |

Introduction
TryHackMe's Brains room is a cybersecurity challenge that focuses on exploiting an authentication bypass vulnerability in TeamCity (CVE-2024-27198). This walkthrough will guide you through the attacker's perspective, where we gain access to the system, and the defender's perspective, where we analyze logs to track the attack.
Step 1: Initial Reconnaissance
Before diving into exploitation, we need to gather information about the target system.
Running an Nmap Scan
Start by scanning the target machine to identify open ports and services, i used the following code:
nmap -A -sV -sS 10.10.155.253(YOUR_MACHINEIP) -T4
but you can have the same results as shown with this:
nmap -A -T4 -p- 10.10.155.253(YOUR_MACHINEIP)
Scan Results:
| Port | Service | Version |
| 22 | SSH | OpenSSH 8.4 |
| 80 | HTTP | Apache 2.4 |
| 50000 | TeamCity | Version 2023.11.4 | <-------
Let's dig further, so open the Firefox browser and in the url bar, let's try input:
http://10.10.155.253(YOUR_MACHINEIP):22(port)
SPOILER ALERT: This won't work, you'll ended up with an unauthorized message!
http://10.10.155.253(YOUR_MACHINEIP):80(port)
That should work but you'll ended up in a landing page, no interesting things even in the source code.
http://10.10.155.253(YOUR_MACHINEIP):50000(port)
BINGO!
The presence of TeamCity on port 50000 is interesting, as we know that version 2023.11.4 is vulnerable to CVE-2024-27198.
Step 2: Exploiting the Vulnerability
_The CVE-2024-27198 vulnerability allows an attacker to bypass authentication and create a new user with administrative privileges.
We need to find a login form and i've found one just typing in the url the following:
http://10.10.155.253(YOUR_MACHINEIP):50000(port)/login.html
See the version of this application, it matches the CV we've discovered!
Let's fire up Metasploit!
msfconsole
Be Patient, it will take some times before everything is correctly loaded
Now let's look if we can find something that matches TeamCity as an exploit
search teamcity
Go ahead and use the fourth exploit and let's check the options to see what we need to give as parameter to metasploit.
use 4
options
Ok, now we need to set at least RHOSTS, RPORT and LHOST to get the exploit to run, no need to set up a netcat listener. I'll list the configuration that for me worked straigh forward:
RHOSTS: 10.10.155.253(
YOUR_VICTIM_MACHINEIP);RPORT: 50000(
YOUR_VICTIM_MACHINEPORT);LHOST: 10.10.233.201(
ATTACKBOX_MACHINEIP, you can find on the top of the terminal or otherwise, open a new terminal and performip a)
I used also the check command just to see if we get response on metasploit about the target vulnerability
Now all we need to do is to run the exploit and wait until metasploit gives us a shell.
It will take some minutes to run and get the shell, if at the first try the exploit won't run, try it again.
Managed to get the shell and performed some basic investigations likels -lorcd ..to check where we were
Just look at directory names to see if we find something interesting. First i started looking up in the home directory but didn't find anything worth looking other than the ubuntu directory
As i was sifting thru i've managed to score the flag!
cat flag.txt
and you'll get what you see here, just copy and paste in the answer box on tryhackme:
So Red Teaming Task SORTED, let's go ahead with the Blue Teaming Task
Step 3: Defensive Analysis with Splunk
Switching to the blue team role, analyze logs to trace the attack.
Splunk runs on port 8000, so we need to come back on Firefox for this task to get it done.
http://10.10.155.253(YOUR_MACHINEIP):8000(port)
When i tried to input this in the URL bar it automatically logged me in Splunk so, just in case, TryHackMe provided you with credentials to log you in.
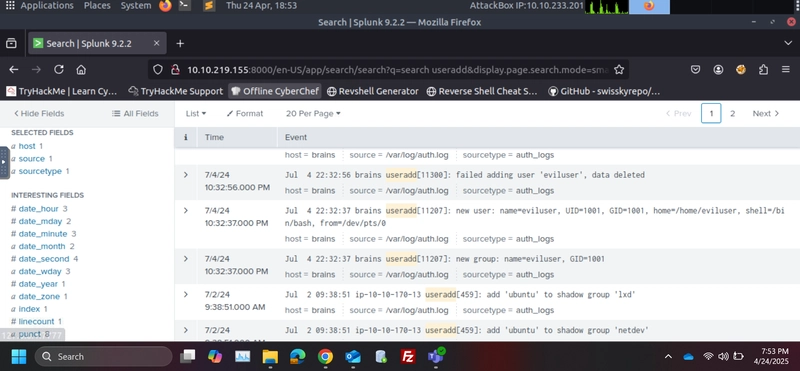
Identifying the Created User
Well, there are multiple completed and hardest ways here, but i worked out the easiest to manage what we were looking for.
I've put in the advanced search bar a simple word like useradd or you can try some of the suggested parameters to look up
If it loads a lot of results you can easily add a date range to get less results and investigate better.
AH! BINGO
See that new user: name=eviluser, someone just added a new user called eviluser and that's one of our answers we were looking for.
Finding the Malicious Package
Use Splunk to check installed packages.
HOW?
Remember the log timing in the previous answer? Keep the month of July and the exact date of the 4th with you.
Now, in the advanced search bar let's input sourcetype so we can specify that we want only package log results. With the date added as parameter of the search the can have a search string that looks like this:
Other answer HERE!!! We get a configure datacollector: amd64 1.0 1.0log result. We know now for sure that datacollector is the name of the package and we see also what version is running too!
Locating the Exploited Plugin
Searching for plugin installation logs can be easy now with all those previous details.
Modify the previous search string by deleting the sourcetype and replacing it with plugins keyword like that:
Keep the exact month and date log time with you, otherwise Splunk will print a butload of results!!!
There you have it! You can see the package name print in clear text: AyzzbuXY.zip and also you have the path were this was actually installed.
My Conclusion
This challenge provides hands-on experience in ethical hacking and incident response. Whether you're an aspiring penetration tester or SOC analyst, mastering both attack and defense techniques is crucial. But really fun! It is intended to have 60 minutes to complete both tasks, you'll managed to do it in probably 5/10 minutes.