Preventing Exploitable Cloud Misconfigurations Using IAM Access Analyzer
Introduction What is IAM and its importance in cloud security? Identity and Access Management (IAM) is an AWS web service that helps you securely control access to AWS resources. IAM provides the infrastructure required to control authentication and authorization to various AWS resources. And a few importance of IAM include the following: Least Privilege Enforcement Enabling Fine-Grained Permissions Auditing & Compliance Managing Federated Access. Hence, the AWS resource that guides you toward least privilege by providing capabilities to set, verify, and refine permissions, analyze external access and validate that your policies match your specified corporate security standards is known as IAM Access Analyzer. By the end of this post, you’ll know how to use IAM Access Analyzer to prevent breaches before they happen by reducing your attack surface and enforcing least privilege. How to set it up. Log into your AWS account and select your region. Search for IAM and navigate to the Access Reports -> Access Analyzer. Click on create analyser, you would see two finding types namely: External access finding: This finding detects when resources (like S3 buckets, Snapshots, KMS keys, etc.) can be accessed by external entities which could lead to data exposure or unauthorized actions. Unused access finding: This finding helps you identify permissions, roles, keys that were granted but never used over a certain time period. So, lets start with the External access finding. Select the External access analysis under the finding type, leaving other defaults settings, click on create analyser. Allow the analyser to scan your account. From the snippet above, it shows me that my account has a public facing bucket and EC2 Snapshot. Investigate further into the S3 Bucket. . For the snippet, you can see the bucket name (iajaihnakmrina), the external principal (all principals), shared through (Bucket Policy) and the level of access (Read) usable by the external entities. Navigate to the S3 bucket -> permissions. Notice that the configured bucket policy has its principal as "*" and the block all public access setting was turned off. Turn on Block Public Access setting and rescan the analyser Upon rescanning, the status now shows Resolved. Repeat the process for the second public facing resource. Notice the snapshot name, status and access level. Navigate to the Snapshot. Select the snapshot, click on Action -> Snapshot setting -> Modify Permissions -> select private sharing option. Now, rescan the analyser to confirm resolved. Next, create a analyser for the unused access analysis. Allow it scan your account automatically. Notice the various findings seen below. From the snippet, you could see the various finding types (unused permission, password, role). Investigating each finding type stating with the Unused permission We have that user - dev1 has two (2) permissions for lambda (last used - never) and IAM (last used - yesterday). Also, notice the recommended remediation steps. Navigate to the IAM user - dev1, notice the various permissions attached to the user. Remove the permissions if not needed any more, then rescan. Do same for the next finding type - Unused password. Navigate to the dev1 user -> Security Credentials -> Managed console access. Click on Disable Console Access. For the programmatic keys, simply delete it. Upon rescan, notice that both the unused password and permission finding types have been resolved. Now, lets focus on the last finding type - unused role. If the role is still needed, simply archive the finding. But if needed no more, just delete it. Finally, notice that all findings are now resolved, lowing my attack surface. Conclusion We have learnt what AWS IAM Access Analyser is about, how to set it up and remediate findings. Ensure that you maintain a reduced attack surface and enforcing least privileged using IAM Access Analyzer by tracking your unused permissions, keys, passwords, roles and public facing resources. Check out this AWS documentation for more information on access analyzer.
Introduction
What is IAM and its importance in cloud security?
Identity and Access Management (IAM) is an AWS web service that helps you securely control access to AWS resources. IAM provides the infrastructure required to control authentication and authorization to various AWS resources. And a few importance of IAM include the following:
Least Privilege Enforcement
Enabling Fine-Grained Permissions
Auditing & Compliance
Managing Federated Access.
Hence, the AWS resource that guides you toward least privilege by providing capabilities to set, verify, and refine permissions, analyze external access and validate that your policies match your specified corporate security standards is known as IAM Access Analyzer. By the end of this post, you’ll know how to use IAM Access Analyzer to prevent breaches before they happen by reducing your attack surface and enforcing least privilege.
How to set it up.
Log into your AWS account and select your region.
Search for IAM and navigate to the Access Reports -> Access Analyzer.
Click on create analyser, you would see two finding types namely:
External access finding: This finding detects when resources (like S3 buckets, Snapshots, KMS keys, etc.) can be accessed by external entities which could lead to data exposure or unauthorized actions.
Unused access finding: This finding helps you identify permissions, roles, keys that were granted but never used over a certain time period.
So, lets start with the External access finding.
Select the External access analysis under the finding type, leaving other defaults settings, click on create analyser.
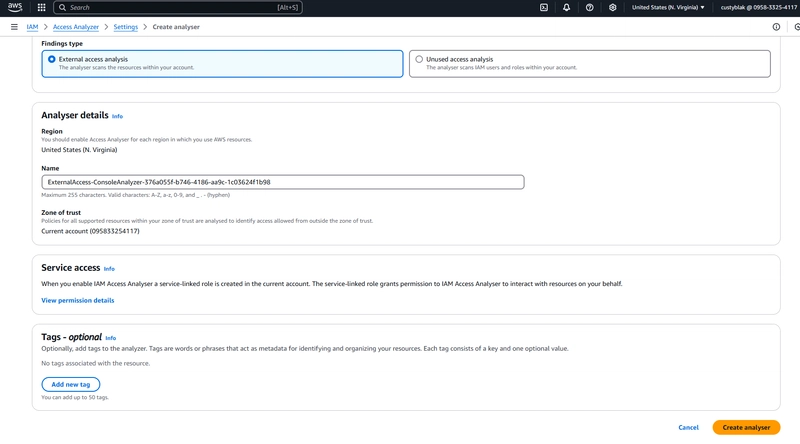
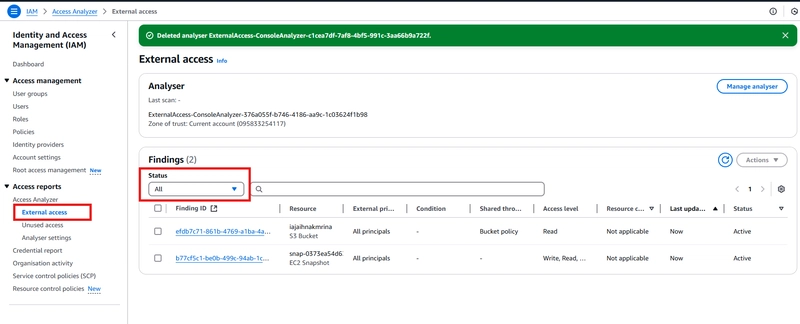
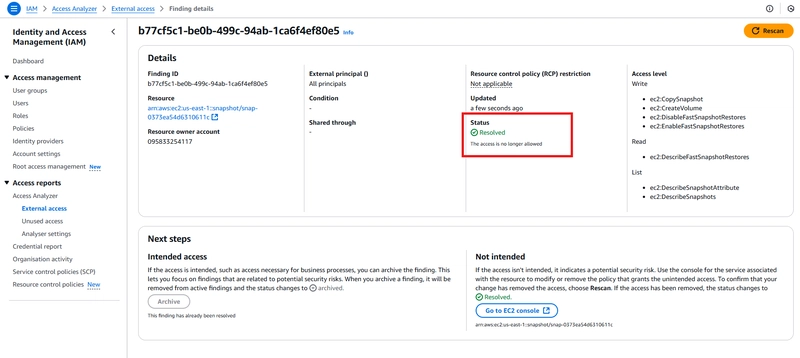
From the snippet above, it shows me that my account has a public facing bucket and EC2 Snapshot.
Investigate further into the S3 Bucket.
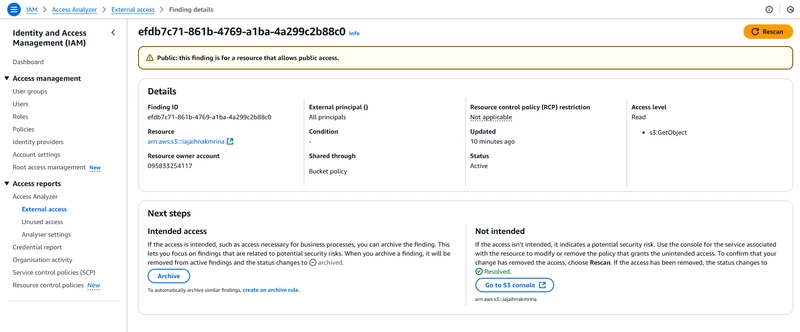 .
.
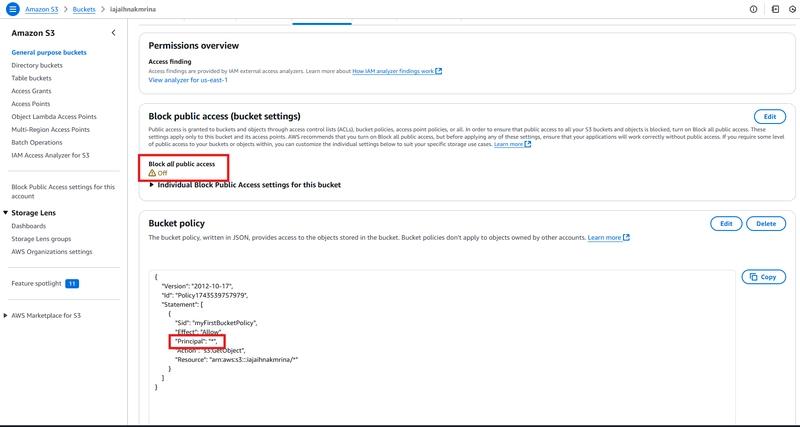
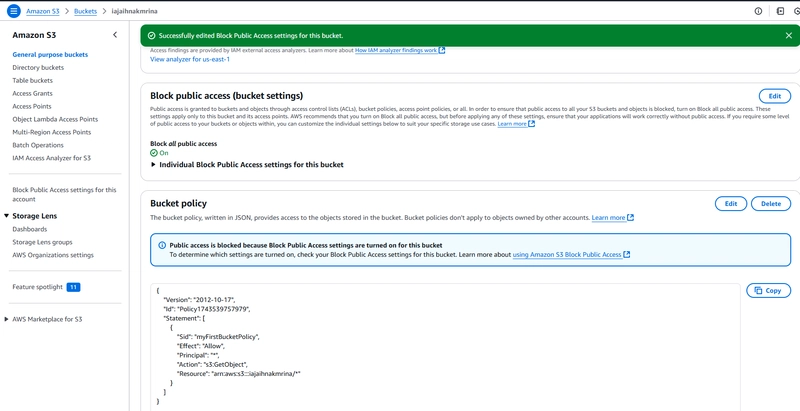
For the snippet, you can see the bucket name (iajaihnakmrina), the external principal (all principals), shared through (Bucket Policy) and the level of access (Read) usable by the external entities.Navigate to the S3 bucket -> permissions.
Notice that the configured bucket policy has its principal as "*" and the block all public access setting was turned off.
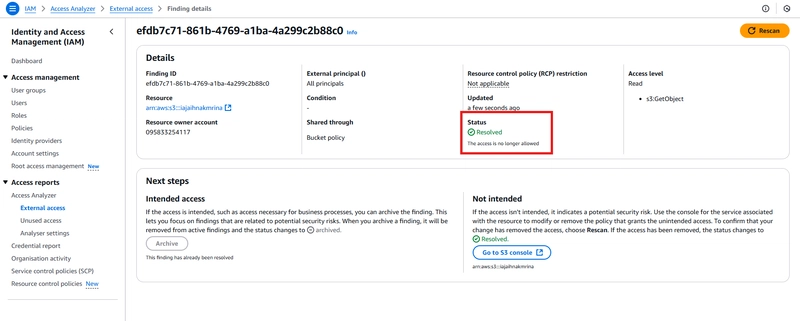
- Turn on Block Public Access setting and rescan the analyser
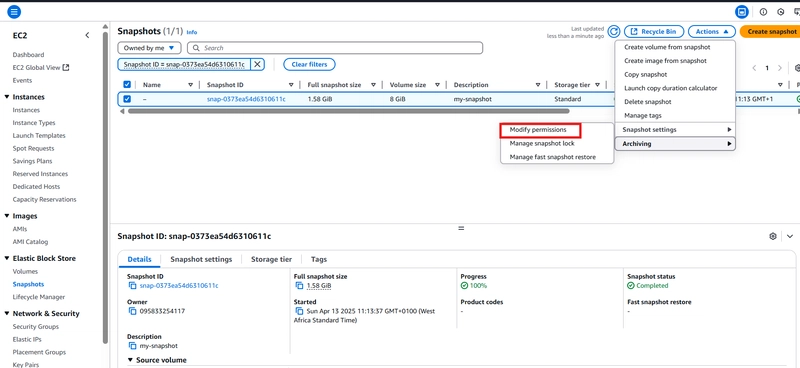
Repeat the process for the second public facing resource. Notice the snapshot name, status and access level.
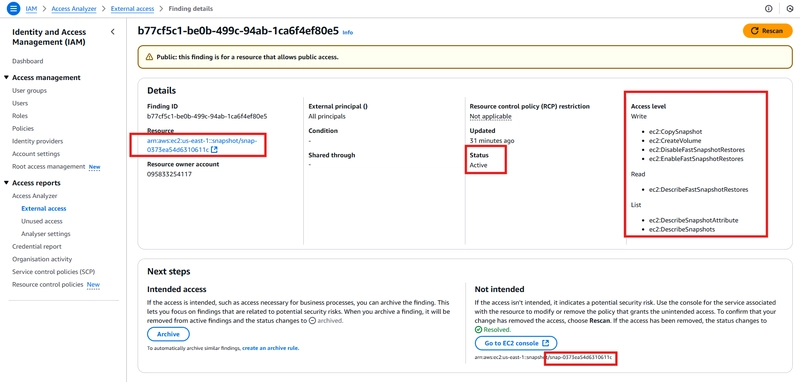
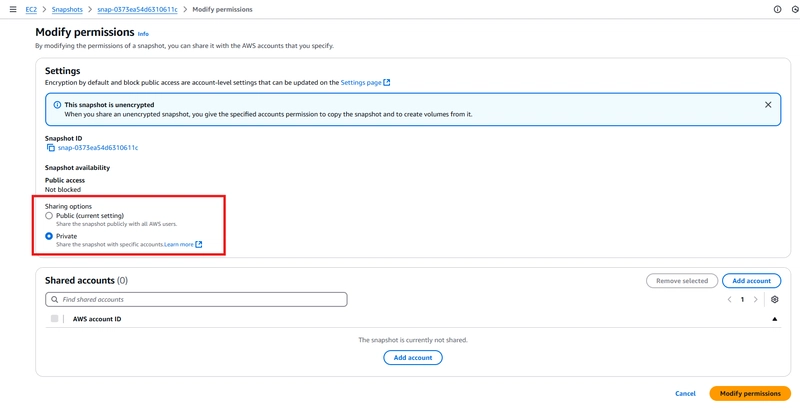
Select the snapshot, click on Action -> Snapshot setting -> Modify Permissions -> select private sharing option.
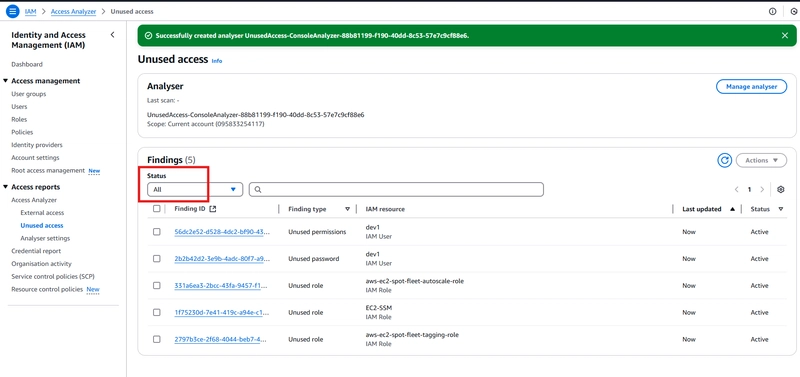
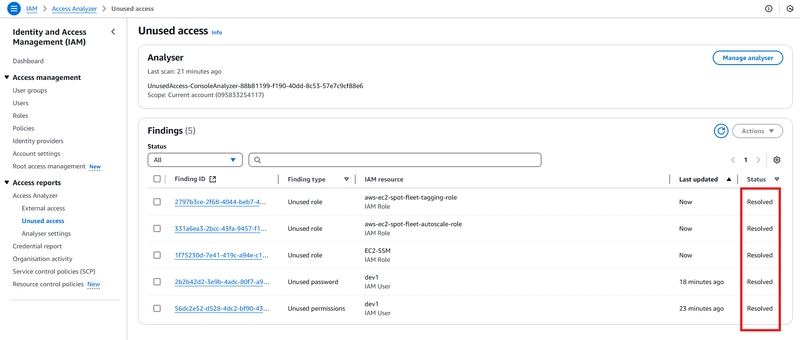
From the snippet, you could see the various finding types (unused permission, password, role).
- Investigating each finding type stating with the Unused permission
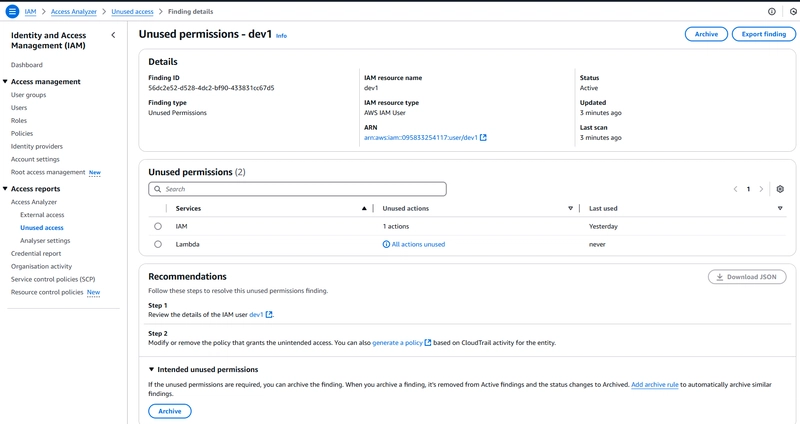
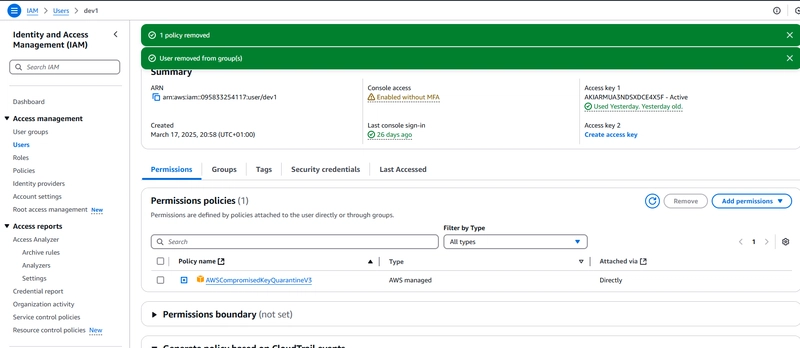
We have that user - dev1 has two (2) permissions for lambda (last used - never) and IAM (last used - yesterday). Also, notice the recommended remediation steps.
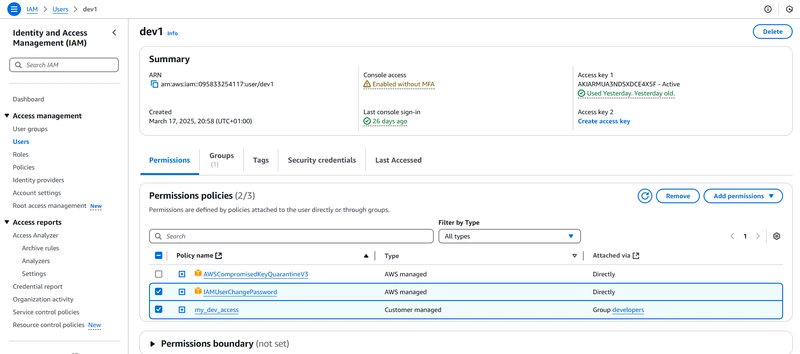
- Navigate to the IAM user - dev1, notice the various permissions attached to the user.
- Remove the permissions if not needed any more, then rescan.
- Do same for the next finding type - Unused password.
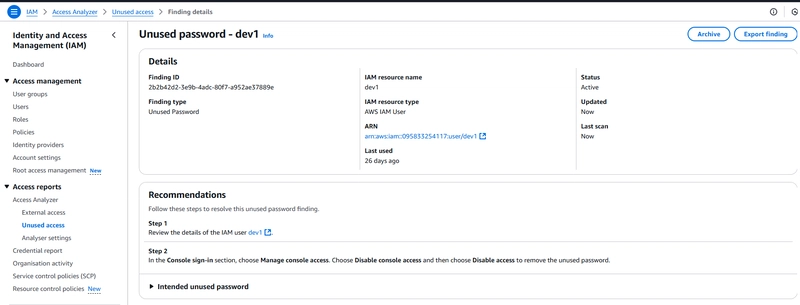
Navigate to the dev1 user -> Security Credentials -> Managed console access.
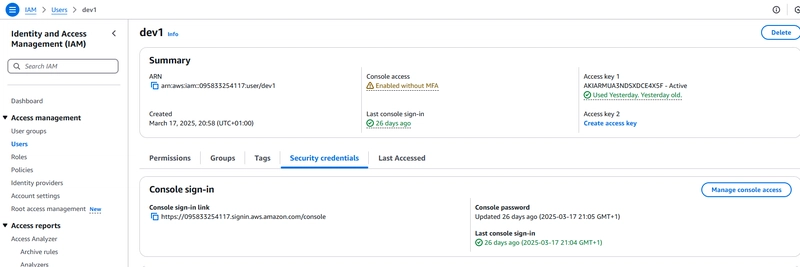
Click on Disable Console Access.
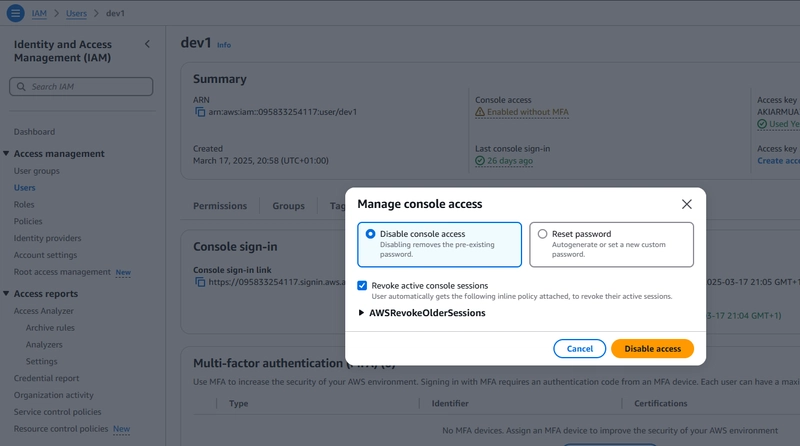
For the programmatic keys, simply delete it.
- Upon rescan, notice that both the unused password and permission finding types have been resolved.
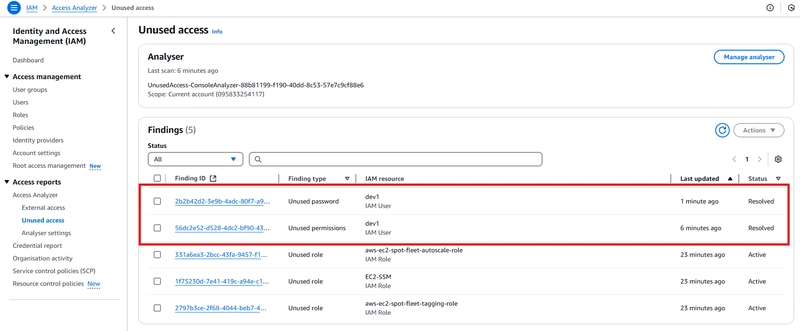
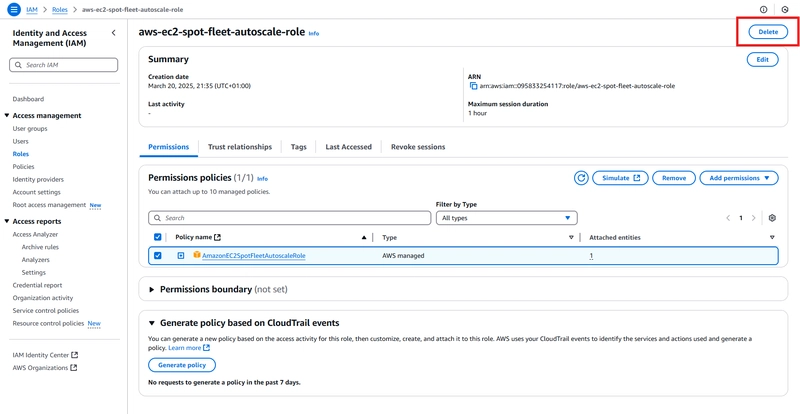
- Now, lets focus on the last finding type - unused role.
If the role is still needed, simply archive the finding. But if needed no more, just delete it.
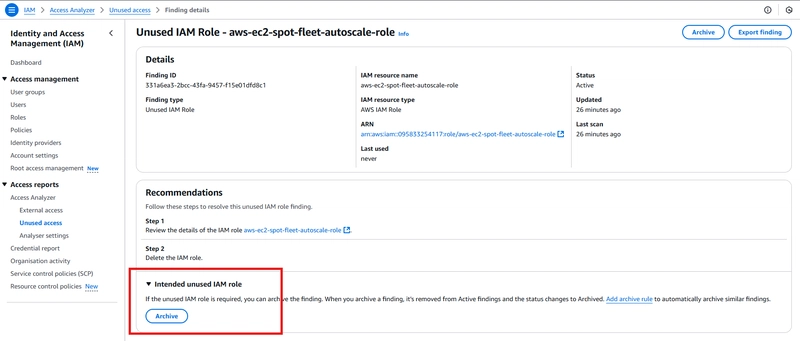
- Finally, notice that all findings are now resolved, lowing my attack surface.
Conclusion
We have learnt what AWS IAM Access Analyser is about, how to set it up and remediate findings. Ensure that you maintain a reduced attack surface and enforcing least privileged using IAM Access Analyzer by tracking your unused permissions, keys, passwords, roles and public facing resources.
Check out this AWS documentation for more information on access analyzer.