How I found my "First Bug" in a public bug bounty program
Today I was reviewing my Telegram channels and realized that I hadn't written a summary of my "first bug" (in quotes - only those in the know will understand). It happened that while searching on a public program (I can't say the platform so as not to give spoilers), when it comes to a cryptocurrency investment platform, I found a link on the main website to an academy website (so far I haven't run any tool). Indeed, I wasn't expecting to find any bugs, but I decided to test it since it didn't have much functionality. I tested for all sorts of vulnerabilities related to authentication and business logic (since that's what I really like to test), but so far without success. Analyzing the website, I could see that it used authentication via JWT tokens and it is known that poor implementation of this type of authentication can lead to various types of vulnerabilities. I decided to start with the most obvious bug, that is, trying to crack the signature key and, for my surprise, it worked! The key was ridiculously easy to crack and my friends even joked: "the developer really wanted to help you, because it cannot be possible..." and added the following command to their bug bounty checklists: hashcat -m 16500 -w3 -S So by changing the userId parameter I was able to account takeover any other account without knowing their credentials, and in this way, access and manipulate their personal information, change their password. I also tested it using the email parameter, but without success. Unfortunately the bug was considered out of scope by the company's staff and I didn't receive anything for it, although it was approved by the platform's triagers.
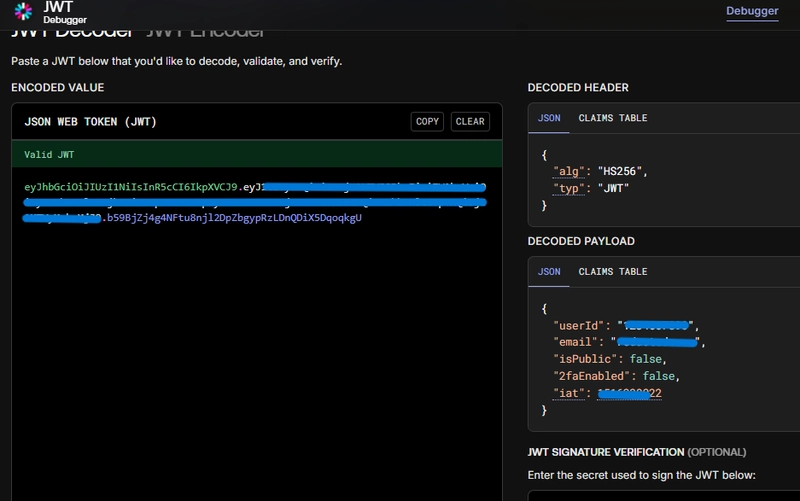
Today I was reviewing my Telegram channels and realized that I hadn't written a summary of my "first bug" (in quotes - only those in the know will understand). It happened that while searching on a public program (I can't say the platform so as not to give spoilers), when it comes to a cryptocurrency investment platform, I found a link on the main website to an academy website (so far I haven't run any tool).
Indeed, I wasn't expecting to find any bugs, but I decided to test it since it didn't have much functionality. I tested for all sorts of vulnerabilities related to authentication and business logic (since that's what I really like to test), but so far without success. Analyzing the website, I could see that it used authentication via JWT tokens and it is known that poor implementation of this type of authentication can lead to various types of vulnerabilities. I decided to start with the most obvious bug, that is, trying to crack the signature key and, for my surprise, it worked!
The key was ridiculously easy to crack and my friends even joked: "the developer really wanted to help you, because it cannot be possible..." and added the following command to their bug bounty checklists:
hashcat -m 16500 -w3 -S
So by changing the userId parameter I was able to account takeover any other account without knowing their credentials, and in this way, access and manipulate their personal information, change their password. I also tested it using the email parameter, but without success.
Unfortunately the bug was considered out of scope by the company's staff and I didn't receive anything for it, although it was approved by the platform's triagers.