Day 9/ 30 Days of Linux Mastery: Special Permissions (SUID, SGID, Sticky Bit)
Table of Contents Introduction What Are Special Permissions? Core Special Permission Commands Real-World Scenario: Special Permissions in a Cloud Project Conclusion Let's Connect Introduction Welcome back to Day 9 of our Linux journey! Over here, we are learning by doing every single day. Today’s focus? Special permissions: They are powerful tools that give extra control over files and directories in multi-user systems. Understanding how these permissions work can help you manage user behavior securely and professionally. What Are Special Permissions? In Linux, we know basic file permissions (rwx). But special permissions go a level deeper. They include: SUID (Set User ID) SGID (Set Group ID) Sticky Bit 1. SUID: Run as the File Owner Use case: You want a regular user to run a script with the permissions of the file owner (usually root). Common with: /usr/bin/passwd command (lets users change their own password). chmod u+s # To verify ls -ld You will see an s replacing the owner's x, like: -rwsr-xr-x 2. SGID: Run as the Group or Share a Group Folder Use case: You are working with a dev team in a shared directory, and all files created should belong to the group. Common with: Shared folders like /var/www/ for web teams. chmod g+s # To verify ls -ld Output drwxr-sr-x 3. Sticky Bit: Lock Files in Shared Directories Use case: In a shared folder (like /tmp), you want users to only delete their own files. Common with: /tmp directory. chmod +t shared_folder # To verify ls -ld Output drwxrwxrwt - you will notice the 't' Core Special Permission Commands Special Permission Commands Purpose chmod u+s 'file' File runs as owner chmod g+s 'directory name' Files in dir inherit group chmod +t 'directory' Users can’t delete others’ files chmod u-s 'directory Remove user special permission SUID chmod g-s 'directory' Remove group special permission SGID chmod -t 'directory' Removes sticky bit Real-World Scenario: Special Permissions in a Cloud Project You have just joined the Infrastructure Team. You are asked to set up a shared workspace /opt/devteam for developers where: All new files must be owned by the group. No one should delete someone else's file. A setup script needs to run with elevated privileges. Solution: Create shared directory /tmp/devteam Create group 'devteam' Change group to devteam Apply special group permission (SGID) Add sticky bit to avoid file deletion (Sticky bit) Note: The capital T indicates that execution permission is inactive. But if it is active it will display a small case t. 3. Create a setup script and set SUID Note the numerical values: For SUID : use 4000 (+/- default permission eg:4755) For SGID : use 2000 (+/- default permission eg:2755) For Sticky bit : use 1000 (+/- default permission eg:1755) Conclusion These special permissions might look small, but they carry huge security and collaboration impact. Mastering these makes you stand out as someone who understands real infrastructure security. If this is helpful to you, feel free to bookmark, comment, like and follow me for Day 10! Let's Connect! If you want to connect or share your journey, feel free to reach out on LinkedIn. I am always happy to learn and build with others in the tech space. #30DaysLinuxChallenge #Redhat#RHCSA #RHCE #CloudWhistler #Linux #Rhel #Ansible #Vim #CloudComputing #DevOps #LinuxAutomation #IaC #SysAdmin#CloudEngineer
Table of Contents
- Introduction
- What Are Special Permissions?
- Core Special Permission Commands
- Real-World Scenario: Special Permissions in a Cloud Project
- Conclusion
- Let's Connect
Introduction
Welcome back to Day 9 of our Linux journey! Over here, we are learning by doing every single day.
Today’s focus? Special permissions: They are powerful tools that give extra control over files and directories in multi-user systems.
Understanding how these permissions work can help you manage user behavior securely and professionally.
What Are Special Permissions?
In Linux, we know basic file permissions (rwx). But special permissions go a level deeper. They include:
SUID (Set User ID)
SGID (Set Group ID)
Sticky Bit
1. SUID: Run as the File Owner
Use case: You want a regular user to run a script with the permissions of the file owner (usually root).
Common with: /usr/bin/passwd command (lets users change their own password).
chmod u+s
# To verify
ls -ld
You will see an s replacing the owner's x, like:
-rwsr-xr-x
2. SGID: Run as the Group or Share a Group Folder
Use case: You are working with a dev team in a shared directory, and all files created should belong to the group.
Common with: Shared folders like /var/www/ for web teams.
chmod g+s
# To verify
ls -ld
Output
drwxr-sr-x
3. Sticky Bit: Lock Files in Shared Directories
Use case: In a shared folder (like /tmp), you want users to only delete their own files.
Common with: /tmp directory.
chmod +t shared_folder
# To verify
ls -ld
Output
drwxrwxrwt - you will notice the 't'
Core Special Permission Commands
| Special Permission Commands | Purpose |
|---|---|
chmod u+s 'file'
|
File runs as owner |
chmod g+s 'directory name'
|
Files in dir inherit group |
chmod +t 'directory'
|
Users can’t delete others’ files |
chmod u-s 'directory
|
Remove user special permission SUID |
chmod g-s 'directory'
|
Remove group special permission SGID |
chmod -t 'directory'
|
Removes sticky bit |
Real-World Scenario: Special Permissions in a Cloud Project
You have just joined the Infrastructure Team. You are asked to set up a shared workspace /opt/devteam for developers where:
All new files must be owned by the group.
No one should delete someone else's file.
A setup script needs to run with elevated privileges.
Solution:
- Create shared directory /tmp/devteam
- Create group 'devteam'
- Change group to devteam
- Apply special group permission (SGID)
- Add sticky bit to avoid file deletion (Sticky bit)
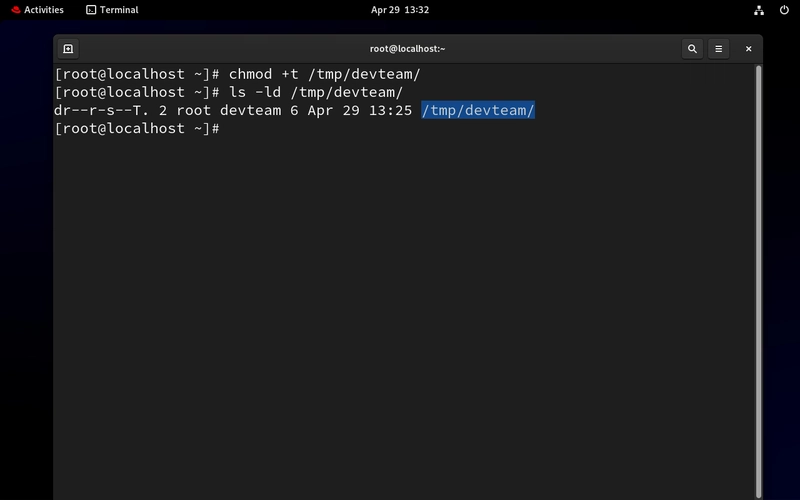
Note: The capital T indicates that execution permission is inactive.
But if it is active it will display a small case t.
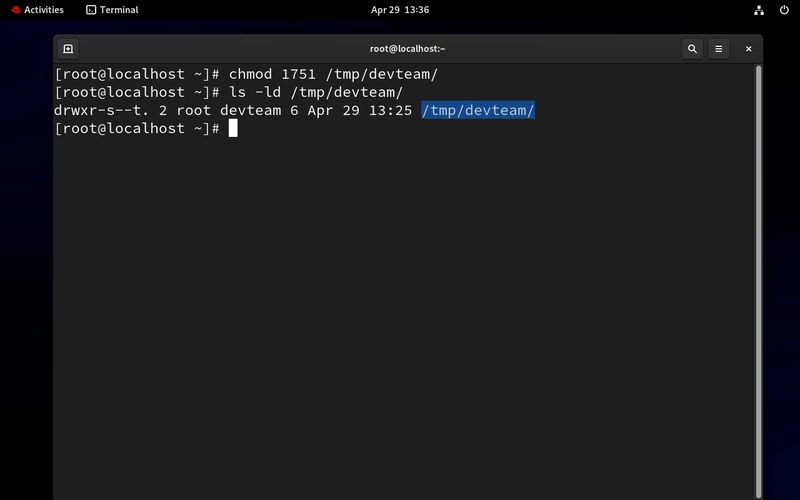
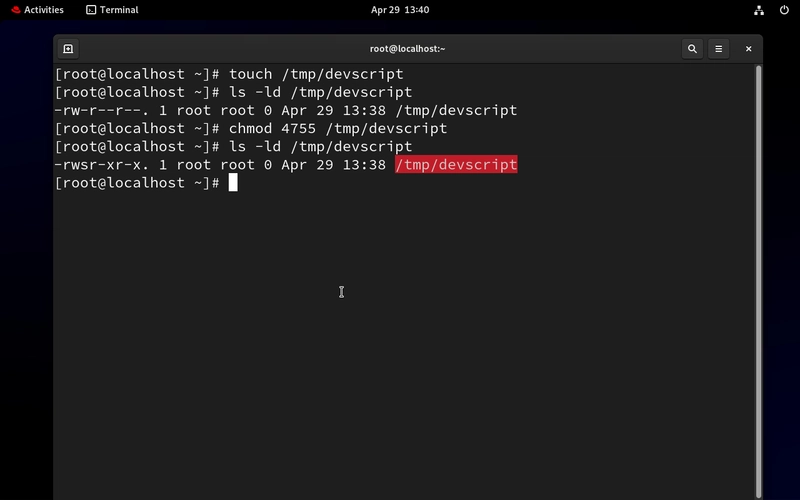
- 3. Create a setup script and set SUID
Note the numerical values:
- For SUID : use 4000 (+/- default permission eg:4755)
- For SGID : use 2000 (+/- default permission eg:2755)
- For Sticky bit : use 1000 (+/- default permission eg:1755)
Conclusion
These special permissions might look small, but they carry huge security and collaboration impact. Mastering these makes you stand out as someone who understands real infrastructure security.
If this is helpful to you, feel free to bookmark, comment, like and follow me for Day 10!
Let's Connect!
If you want to connect or share your journey, feel free to reach out on LinkedIn.
I am always happy to learn and build with others in the tech space.
#30DaysLinuxChallenge #Redhat#RHCSA #RHCE #CloudWhistler #Linux #Rhel #Ansible #Vim #CloudComputing #DevOps #LinuxAutomation #IaC #SysAdmin#CloudEngineer