Crocodilus – A New Android Malware Remotely Control Your Android Devices
Researchers has identified a novel mobile banking Trojan, designated “Crocodilus,” marking a significant advancement in the evolution of Android-targeted malware. Unlike predecessors such as Anatsa, Octo, and Hook, which incrementally refined their capabilities, Crocodilus emerges as a fully mature threat, integrating sophisticated features including overlay attacks, accessibility-based data harvesting, remote access trojan (RAT) functionality, and […] The post Crocodilus – A New Android Malware Remotely Control Your Android Devices appeared first on Cyber Security News.

Researchers has identified a novel mobile banking Trojan, designated “Crocodilus,” marking a significant advancement in the evolution of Android-targeted malware.
Unlike predecessors such as Anatsa, Octo, and Hook, which incrementally refined their capabilities, Crocodilus emerges as a fully mature threat, integrating sophisticated features including overlay attacks, accessibility-based data harvesting, remote access trojan (RAT) functionality, and obfuscated remote control mechanisms.
Discovered during routine threat hunting, the malware’s name derives from developer artifacts referencing “Crocodile” within its codebase.
Technical Breakdown of Crocodilus
Crocodilus employs a multi-stage infection chain, initiated via a proprietary dropper designed to circumvent Android 13+ runtime permission restrictions (e.g., sideload detection enhancements).
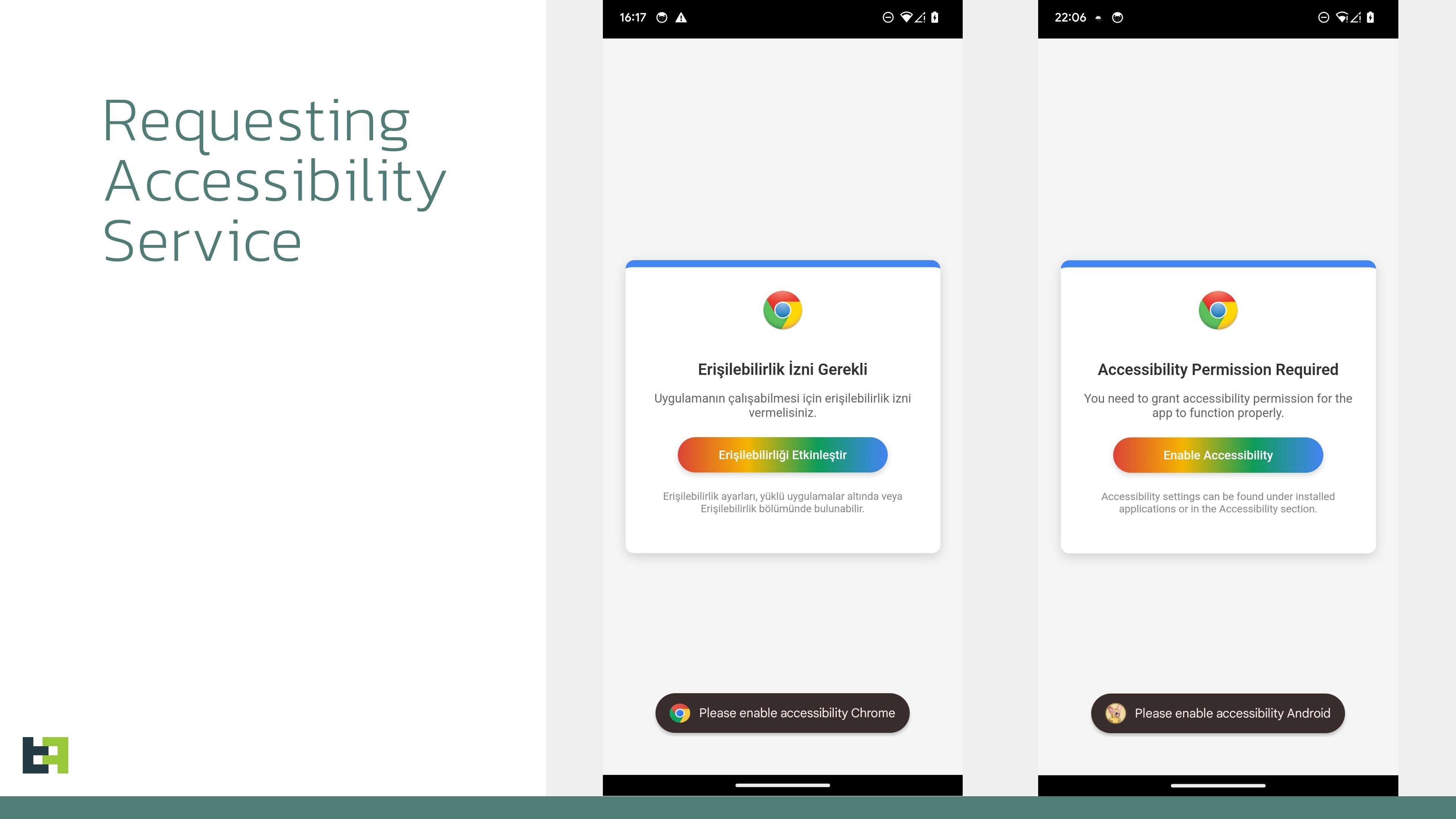
Post-installation, the malware prompts the user to enable Accessibility Services, a critical pivot for its operational capabilities.
Once granted, Crocodilus establishes a persistent connection to a command-and-control (C2) server, retrieving dynamic configurations such as target application package names and overlay templates.
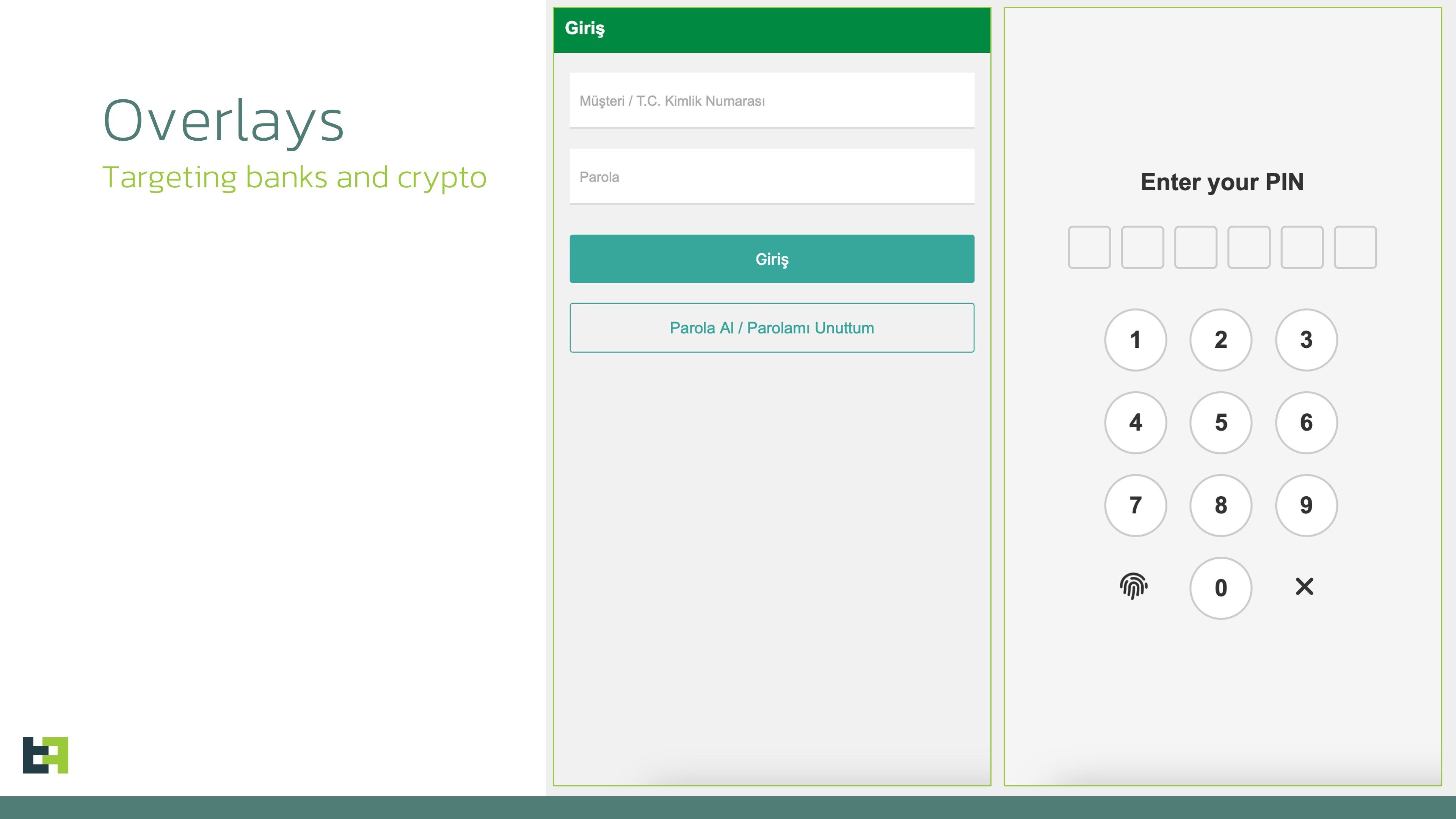
The malware operates as a device-takeover Trojan, leveraging real-time app monitoring to trigger overlay attacks.
These overlays, HTML-based phishing screens, are injected atop legitimate banking or cryptocurrency apps, capturing user credentials.
Initial campaigns indicate targeting of financial institutions in Spain and Turkey, alongside prominent cryptocurrency wallets, with expectations of broader scope as C2 infrastructure scales.
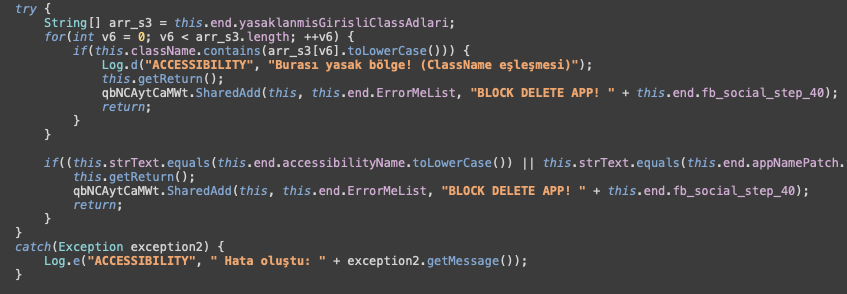
A standout feature is its “Accessibility Logger,” which transcends traditional keylogging.
By hooking into Android’s Accessibility API, Crocodilus enumerates and logs all UI elements and events: text inputs, button labels, and dynamic content such as OTP codes from apps like Google Authenticator.
For instance, the RAT command “TG32XAZADG” triggers a targeted screen scrape of Google Authenticator, extracting OTP names and values for immediate exfiltration to the C2 server.
Remote access is facilitated through a robust RAT module, enabling full device control.
Notably, Crocodilus implements a “hidden” mode, deploying a full-screen black overlay to mask operator actions while muting device audio to suppress audible cues of manipulation.
This allows seamless execution of fraudulent transactions without victim awareness.
Analysis of early Crocodilus samples reveals a tag, “sybupdate,” potentially linking it to the “sybra” threat actor, previously associated with the Ermac fork “MetaDroid” and campaigns involving Hook and Octo.
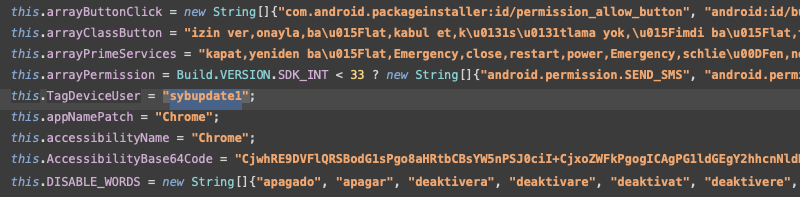
However, attribution remains inconclusive; “sybra” may be a developer, distributor, or early adopter. Further insight comes from debug strings in the malware’s source, written in Turkish, suggesting Turkish-speaking developers.
Social Engineering and Data Harvesting
A notable tactic targets cryptocurrency wallet users.
Post-credential capture via overlays, Crocodilus displays a deceptive prompt: “Back up your wallet key in the settings within 12 hours. Otherwise, the app will be reset, and you may lose access to your wallet.”
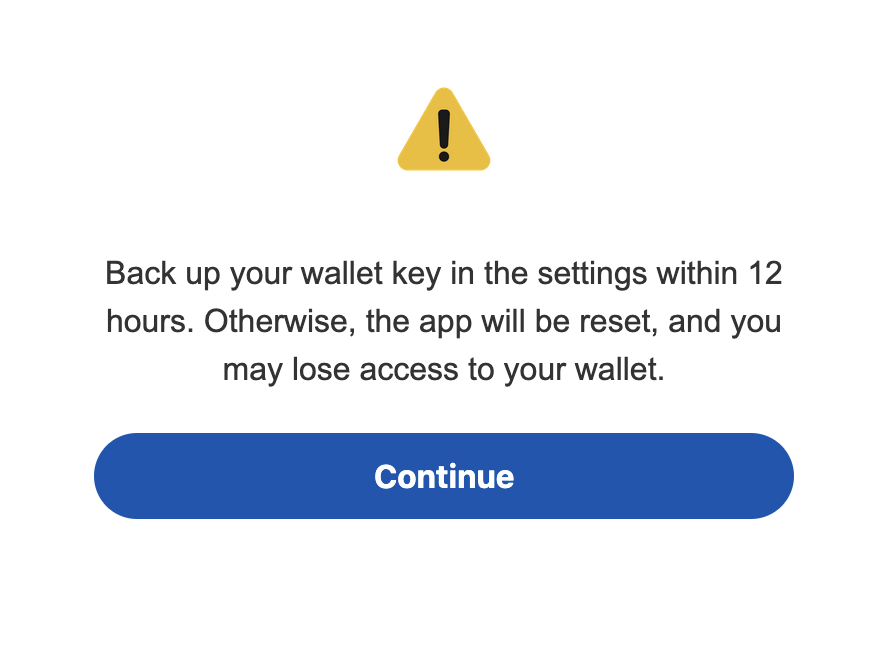
This manipulates victims into navigating to their seed phrase, which the Accessibility Logger harvests, granting attackers unrestricted wallet access.
Crocodilus exemplifies a paradigm shift in mobile malware sophistication.
Its integration of device-takeover capabilities, black-screen obfuscation, and advanced logging from inception distinguishes it from nascent threats.
Targeting high-value assets, banking credentials and cryptocurrency keys, it exploits the Android ecosystem’s Accessibility Services in ways that challenge conventional defenses.
Signature-based detection proves inadequate against such polymorphic threats, particularly during initial propagation phases.
Mitigation requires a multi-layered approach: behavioral analysis of app interactions, runtime device integrity checks, and anomaly detection in network traffic to C2 endpoints.
Financial institutions and cryptocurrency platforms must prioritize these strategies to counter Crocodilus’s evolving footprint.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates
The post Crocodilus – A New Android Malware Remotely Control Your Android Devices appeared first on Cyber Security News.