Building a Scalable, Secure Multi-Tier Architecture on AWS — My Recent Infrastructure Project
Over the past few weeks, I’ve been working on a cloud infrastructure project that I’m very proud to share. This project centers around designing and deploying a highly available, secure, and scalable multi-tier architecture on Amazon Web Services (AWS). It's a great example of how we can apply core cloud and security best practices in a real-world scenario. Let me walk you through the architecture and the thought process behind it. Objective To build a 3-tier web application infrastructure on AWS that emphasizes: High Availability Scalability Security Observability This design is tailored for production-level applications with strict requirements for uptime, monitoring, and protection from external threats. Architecture Diagram High-Level Overview The architecture is built within a VPC (10.0.0.0/16), split across two Availability Zones (AZ-A and AZ-B) for redundancy. It follows the standard 3-tier model: Web Tier Application Tier Integration Tier (Background Services / Async Processing) Each tier is isolated within its own subnet and protected using security groups and routing policies. Key AWS Services Used EC2 – For compute resources ALB (Application Load Balancer) – To distribute traffic between internal services ELB (External Load Balancer) – To handle incoming requests Auto Scaling – To ensure each tier can scale based on demand S3 – For static content and logs RDS – For managed relational database service EFS – For shared storage across AZs IAM – To manage fine-grained access controls CloudWatch – For monitoring and logging Route 53 – For DNS resolution VPC Flow Logs – For traffic visibility and security analysis CloudFront – For CDN distribution (static assets and caching) Detailed Architecture Breakdown 1. Web Tier (Frontend) Deployed across two public subnets. EC2 instances serve the frontend (Apache/NGINX or Node.js apps). Protected by an External ALB that routes traffic using HTTPS (SSL termination). Auto Scaling Groups handle traffic spikes and maintain instance health. Integrated with CloudFront to serve cached content quickly. 2. Application Tier Deployed in private subnets for better security. Hosts core business logic on EC2, registered under an Internal ALB. Communicates with both the web and integration tiers. IAM roles restrict access to specific AWS services (e.g., S3, RDS). 3. Integration Tier Handles background tasks and async processes (e.g., job queues, processing pipelines). Also deployed in private subnets. This layer is decoupled and communicates directly with the Application Tier and services like RDS or S3. All logs and outputs are pushed to S3 and CloudWatch. Security Best Practices Layered Security: Subnets and security groups segment each layer. Least Privilege: IAM roles and policies are tightly scoped. No Public Access to App/Integration Tiers: Only the Web Tier is exposed via the External Load Balancer. VPC Flow Logs track traffic patterns and are fed into SIEM tools for analysis. Data Encryption: At rest (S3, RDS, EFS) and in transit (HTTPS). Resilience & Observability Health checks and auto-scaling across AZs provide fault tolerance. CloudWatch metrics, alarms, and dashboards offer real-time observability. Application logs and metrics are centralized in CloudWatch and S3 for auditing and debugging. What’s Next? Integrating AWS WAF and Shield for advanced threat protection. Enabling DynamoDB and Lambda-based background workers in the integration tier. Automating the entire infrastructure using Terraform and CI/CD pipelines for streamlined deployment. Final Thoughts This project pushed me deeper into cloud security, automation, and architecture design. It solidified my understanding of multi-tier deployments and sharpened my focus on resilience and compliance in production systems. If you're building a cloud-native app or looking to secure a modern SaaS workload on AWS, this kind of architecture offers a robust foundation. Feel free to connect if you'd like to collaborate or brainstorm ideas — I'm always open to meaningful conversations around Cloud Security, DevSecOps, and AI-driven Infrastructure.
Over the past few weeks, I’ve been working on a cloud infrastructure project that I’m very proud to share. This project centers around designing and deploying a highly available, secure, and scalable multi-tier architecture on Amazon Web Services (AWS). It's a great example of how we can apply core cloud and security best practices in a real-world scenario.
Let me walk you through the architecture and the thought process behind it.
Objective
To build a 3-tier web application infrastructure on AWS that emphasizes:
- High Availability
- Scalability
- Security
- Observability
This design is tailored for production-level applications with strict requirements for uptime, monitoring, and protection from external threats.
High-Level Overview
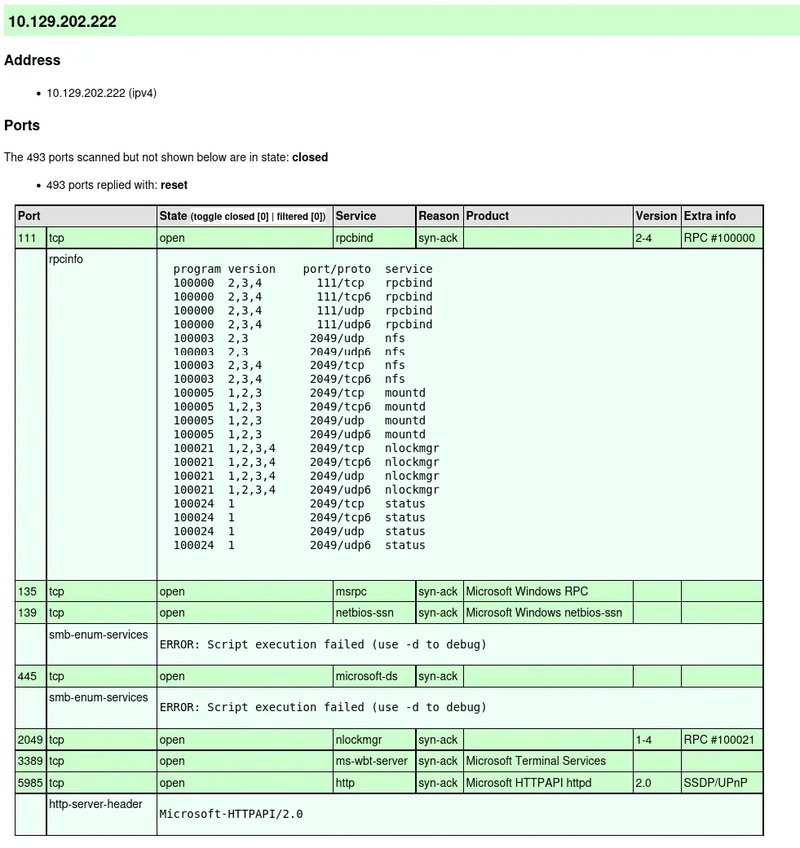
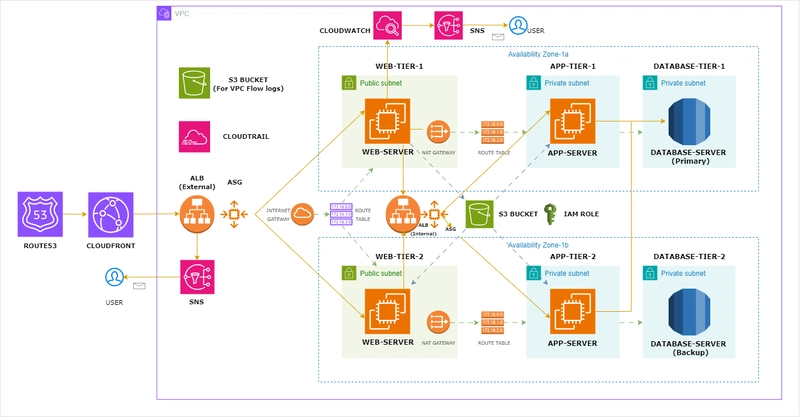
The architecture is built within a VPC (10.0.0.0/16), split across two Availability Zones (AZ-A and AZ-B) for redundancy. It follows the standard 3-tier model:
- Web Tier
- Application Tier
- Integration Tier (Background Services / Async Processing)
Each tier is isolated within its own subnet and protected using security groups and routing policies.
Key AWS Services Used
- EC2 – For compute resources
- ALB (Application Load Balancer) – To distribute traffic between internal services
- ELB (External Load Balancer) – To handle incoming requests
- Auto Scaling – To ensure each tier can scale based on demand
- S3 – For static content and logs
- RDS – For managed relational database service
- EFS – For shared storage across AZs
- IAM – To manage fine-grained access controls
- CloudWatch – For monitoring and logging
- Route 53 – For DNS resolution
- VPC Flow Logs – For traffic visibility and security analysis
- CloudFront – For CDN distribution (static assets and caching)
Detailed Architecture Breakdown
1. Web Tier (Frontend)
- Deployed across two public subnets.
- EC2 instances serve the frontend (Apache/NGINX or Node.js apps).
- Protected by an External ALB that routes traffic using HTTPS (SSL termination).
- Auto Scaling Groups handle traffic spikes and maintain instance health.
- Integrated with CloudFront to serve cached content quickly.
2. Application Tier
- Deployed in private subnets for better security.
- Hosts core business logic on EC2, registered under an Internal ALB.
- Communicates with both the web and integration tiers.
- IAM roles restrict access to specific AWS services (e.g., S3, RDS).
3. Integration Tier
- Handles background tasks and async processes (e.g., job queues, processing pipelines).
- Also deployed in private subnets.
- This layer is decoupled and communicates directly with the Application Tier and services like RDS or S3.
- All logs and outputs are pushed to S3 and CloudWatch.
Security Best Practices
- Layered Security: Subnets and security groups segment each layer.
- Least Privilege: IAM roles and policies are tightly scoped.
- No Public Access to App/Integration Tiers: Only the Web Tier is exposed via the External Load Balancer.
- VPC Flow Logs track traffic patterns and are fed into SIEM tools for analysis.
- Data Encryption: At rest (S3, RDS, EFS) and in transit (HTTPS).
Resilience & Observability
- Health checks and auto-scaling across AZs provide fault tolerance.
- CloudWatch metrics, alarms, and dashboards offer real-time observability.
- Application logs and metrics are centralized in CloudWatch and S3 for auditing and debugging.
What’s Next?
- Integrating AWS WAF and Shield for advanced threat protection.
- Enabling DynamoDB and Lambda-based background workers in the integration tier.
- Automating the entire infrastructure using Terraform and CI/CD pipelines for streamlined deployment.
Final Thoughts
This project pushed me deeper into cloud security, automation, and architecture design. It solidified my understanding of multi-tier deployments and sharpened my focus on resilience and compliance in production systems.
If you're building a cloud-native app or looking to secure a modern SaaS workload on AWS, this kind of architecture offers a robust foundation.
Feel free to connect if you'd like to collaborate or brainstorm ideas — I'm always open to meaningful conversations around Cloud Security, DevSecOps, and AI-driven Infrastructure.