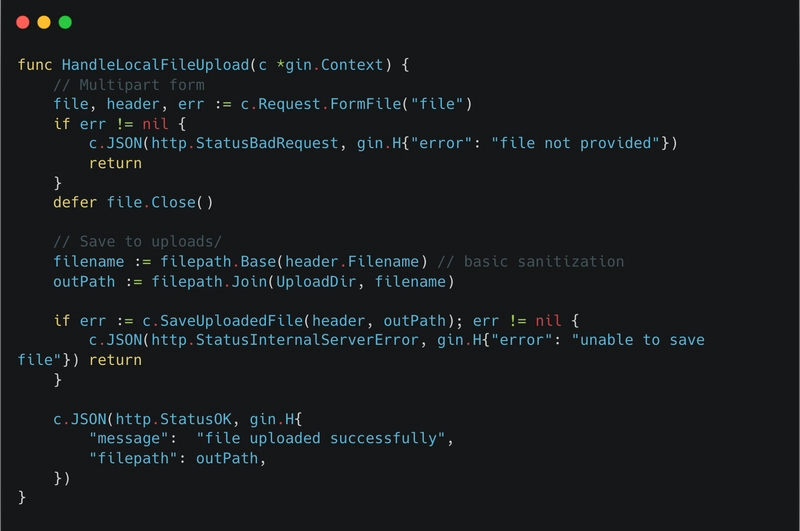
AutoSecure API Gateway: Permissions Redefined
This is a submission for the Permit.io Authorization Challenge: Permissions Redefined Created by @kevin_heidt_d73c1752454fb What I Built I built AutoSecure API Gateway, an innovative authorization solution for the automotive industry that tackles the complex web of permissions unique to dealership networks, service centers, and connected vehicle ecosystems. The automotive industry presents distinctive authorization challenges: Dealership staff may work across multiple locations with varying permission levels Service technicians need temporary access to vehicle systems based on work orders Fleet managers require different access levels based on vehicle ownership arrangements Vehicle owners expect granular control over who can access their vehicle data High employee turnover requires immediate permission revocation AutoSecure addresses these challenges by implementing API-first authorization through Permit.io and NGINX, allowing centralized policy management while maintaining high-performance gateway-level enforcement. Demo Try the live demo: AutoSecure API Gateway Test Credentials: Admin: admin / 2025DEVChallenge Regular User: newuser / 2025DEVChallenge The interactive Swagger UI demonstrates: Vehicle ownership validation (users can only access vehicles they own) Role-based access differentiation (fleet managers vs. service technicians) Dealership-specific permissions (access to service records only at authorized locations) Temporal authorization (time-limited access for service appointments) Project Repo kaheidt / nginx-permitio Demonstrate API First Development with utilization of permit.io AutoSecure API Gateway: API-First Authorization for Automotive Industry An innovative API gateway solution leveraging NGINX and Permit.io to implement fine-grained authorization for automotive industry applications. LIVE DEMO Try it out LIVE HERE Project Overview AutoSecure API Gateway demonstrates how API-First authorization principles can be applied to modern automotive industry services. It showcases how authorization can be externalized from application code and enforced at the gateway layer using Permit.io's integration with NGINX. Use Case: Connected Vehicle Services Platform This project implements a Connected Vehicle Services Platform API with the following components: Vehicle Telemetry API - Access to real-time vehicle data Maintenance Services API - Schedule and manage service appointments Fleet Management API - Monitor and manage vehicle fleets Driver Behavior Analytics API - Access to driving behavior data Each API has different access control requirements based on user roles: Vehicle Owner - Access to their own vehicle data and services Service… View on GitHub The repository includes comprehensive documentation on how the project models and enforces the complex authorization relationships in the automotive industry: Architecture design with gateway-level enforcement Authorization model for automotive industry relationships API documentation showing permission requirements for endpoints My Journey Understanding Automotive Access Control Challenges My first challenge was modeling the complex relationships in automotive dealership networks: Relationship Complexity: A service technician might work at multiple dealerships but have different certification levels and access rights at each location. For example, a technician certified for Brand A at Dealership X might only have basic access at Dealership Y. Employee Turnover: The automotive industry experiences high turnover rates (15-20% annually for service technicians). Traditional role-based authorization creates security risks when deprovisioning is delayed. Multi-tenant Hierarchies: Dealership groups operate multiple locations, with regional managers needing cross-location access while location managers need limited access. Connected Vehicle Data: Modern vehicles generate telematics data that may need to be shared selectively with service centers only during authorized repair visits. Implementation Breakthroughs The key breakthrough came when I realized traditional role-based authorization fails to address these complexities. Instead, I needed to: Model Relationships, Not Just Roles: Using Permit.io's flexible policy model, I created relationship-based rules like: //Service tech can only access vehicles at their current assigned dealership user.role == "service_technician" && resource.current_dealership_id == user.assigned_dealership_id Implement Time-bound Access: For service appointments, access is granted only during scheduled service windows: //Service tech can access vehicle diagnostic data only during scheduled appointment now() >= resource.appointment_start_time && now()

This is a submission for the Permit.io Authorization Challenge: Permissions Redefined
Created by @kevin_heidt_d73c1752454fb
What I Built
I built AutoSecure API Gateway, an innovative authorization solution for the automotive industry that tackles the complex web of permissions unique to dealership networks, service centers, and connected vehicle ecosystems.
The automotive industry presents distinctive authorization challenges:
- Dealership staff may work across multiple locations with varying permission levels
- Service technicians need temporary access to vehicle systems based on work orders
- Fleet managers require different access levels based on vehicle ownership arrangements
- Vehicle owners expect granular control over who can access their vehicle data
- High employee turnover requires immediate permission revocation
AutoSecure addresses these challenges by implementing API-first authorization through Permit.io and NGINX, allowing centralized policy management while maintaining high-performance gateway-level enforcement.
Demo
Try the live demo: AutoSecure API Gateway
Test Credentials:
- Admin:
admin/2025DEVChallenge - Regular User:
newuser/2025DEVChallenge
The interactive Swagger UI demonstrates:
- Vehicle ownership validation (users can only access vehicles they own)
- Role-based access differentiation (fleet managers vs. service technicians)
- Dealership-specific permissions (access to service records only at authorized locations)
- Temporal authorization (time-limited access for service appointments)
Project Repo
 kaheidt
/
nginx-permitio
kaheidt
/
nginx-permitio
Demonstrate API First Development with utilization of permit.io
AutoSecure API Gateway: API-First Authorization for Automotive Industry
An innovative API gateway solution leveraging NGINX and Permit.io to implement fine-grained authorization for automotive industry applications.
LIVE DEMO
Try it out LIVE HERE
Project Overview
AutoSecure API Gateway demonstrates how API-First authorization principles can be applied to modern automotive industry services. It showcases how authorization can be externalized from application code and enforced at the gateway layer using Permit.io's integration with NGINX.
Use Case: Connected Vehicle Services Platform
This project implements a Connected Vehicle Services Platform API with the following components:
- Vehicle Telemetry API - Access to real-time vehicle data
- Maintenance Services API - Schedule and manage service appointments
- Fleet Management API - Monitor and manage vehicle fleets
- Driver Behavior Analytics API - Access to driving behavior data
Each API has different access control requirements based on user roles:
- Vehicle Owner - Access to their own vehicle data and services
- Service…
The repository includes comprehensive documentation on how the project models and enforces the complex authorization relationships in the automotive industry:
- Architecture design with gateway-level enforcement
- Authorization model for automotive industry relationships
- API documentation showing permission requirements for endpoints
My Journey
Understanding Automotive Access Control Challenges
My first challenge was modeling the complex relationships in automotive dealership networks:
Relationship Complexity: A service technician might work at multiple dealerships but have different certification levels and access rights at each location. For example, a technician certified for Brand A at Dealership X might only have basic access at Dealership Y.
Employee Turnover: The automotive industry experiences high turnover rates (15-20% annually for service technicians). Traditional role-based authorization creates security risks when deprovisioning is delayed.
Multi-tenant Hierarchies: Dealership groups operate multiple locations, with regional managers needing cross-location access while location managers need limited access.
Connected Vehicle Data: Modern vehicles generate telematics data that may need to be shared selectively with service centers only during authorized repair visits.
Implementation Breakthroughs
The key breakthrough came when I realized traditional role-based authorization fails to address these complexities. Instead, I needed to:
- Model Relationships, Not Just Roles: Using Permit.io's flexible policy model, I created relationship-based rules like:
//Service tech can only access vehicles at their current assigned dealership
user.role == "service_technician" && resource.current_dealership_id == user.assigned_dealership_id
- Implement Time-bound Access: For service appointments, access is granted only during scheduled service windows:
//Service tech can access vehicle diagnostic data only during scheduled
appointment now() >= resource.appointment_start_time && now() <= resource.appointment_end_time
- Use NGINX As The Enforcement Layer: By moving authorization to the API gateway with Permit.io's NGINX integration, I eliminated inconsistent enforcement across microservices.
Technical Challenges Overcome
- Performance Concerns: Authorization checks for every API call could create latency. I solved this with:
- Local PDP sidecar for low-latency decisions
- Intelligent caching of authorization decisions
Optimized JWT processing in NGINX
Complex Authorization Logic: Automotive relationship modeling required intricate policies. I addressed this by:
Creating a hierarchy of policies from simple to complex
Building reusable policy components with Permit.io
Separating base role permissions from contextual rules
Using Permit.io for Authorization
Permit.io transformed how I approached automotive industry authorization in several key ways:
1. Context-Aware Authorization
The automotive industry requires authorization decisions based on multiple contexts that traditional RBAC can't handle:
// A dealership can only access vehicles that were purchased there OR
// are currently being serviced there OR have a valid service agreement
permit.check(
user, "view", vehicle,
{
dealership_id: user.dealership_id,
context: {
purchase_location: vehicle.purchase_dealership_id,
service_location: vehicle.current_service_location,
service_agreements: vehicle.active_service_agreements
}
}
);
2. Relationship-Based Authorization
Using Permit.io's flexible policy model, I created relationship-based rules that reflect the real automotive industry:
// Regional manager can access data across multiple dealerships
user.role == "regional_manager" &&
user.region_id == resource.dealership.region_id
// Service technician access depends on certification level
user.role == "service_technician" &&
user.certification_level >= resource.required_certification_level
// Parts department can view vehicle history only for parts ordering
user.department == "parts" && action == "view_history"
3. Dynamic Permission Adjustments
Employee roles in automotive often change temporarily (covering shifts, special assignments). Permit.io enabled dynamic permission adjustments without code changes:
// Tech temporarily assigned to another dealership
(user.role == "service_technician" &&
(user.assigned_dealership_id == resource.dealership_id ||
user.temporary_assignments.includes(resource.dealership_id)))
4. Multi-Brand Dealership Groups
Many dealership groups represent multiple brands, each with different access requirements:
// Brand-specific certification is required for diagnostics
user.role == "service_technician" &&
user.certifications.includes(resource.vehicle.brand) &&
action == "run_diagnostics"
By leveraging Permit.io's flexible policy engine at the NGINX gateway level, AutoSecure provides a comprehensive solution to the automotive industry's unique authorization challenges—finally bringing structured, consistent access control to an industry that has long struggled with it.
Thank you for considering my submission! I hope AutoSecure API Gateway demonstrates how Permit.io can transform authorization in complex multi-relationship environments like the automotive industry.