The Trump Administration Signal Scandal, Somehow, Gets Worse
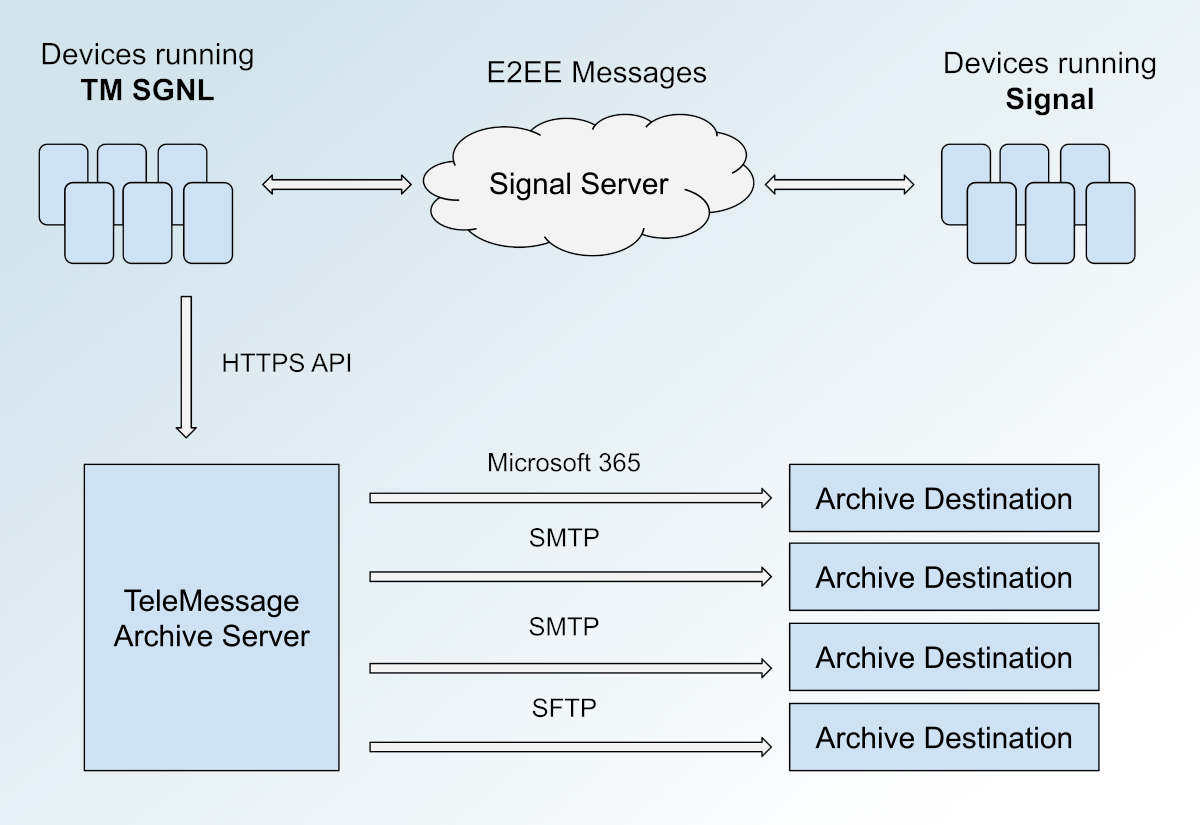
Micah Lee, in a spectacularly detailed post: On Thursday, 404 Media reported that in the Reuters photo showing former National Security Advisor and war criminal Mike Waltz checking his Signal messages under the table, he was actually using an obscure modified Signal app called TM SGNL, and not the real and actually secure Signal app. On Friday, I wrote an analysis of everything I could find out about TM SGNL using OSINT, including the fact that it’s nearly impossible to install without a device enrolled in an MDM service that’s tied to an Apple Business Manager or a Google Enterprise account. On Saturday, after discovering that TeleMessage published the source code for the TM SGNL apps for Android and iPhone themselves, I re-published them on GitHub with the goal of making them easier to research. (It looks like the iOS source code is actually just unmodified Signal, so maybe they actually only published their Android code.) On Saturday night, an anonymous source told me they hacked TeleMessage. On Sunday, I, along with Joseph Cox, published an article about the hack to 404 Media (and to my blog). On Monday, NBC News reported that TeleMessage suspended its service after a second hacker breached TeleMessage and “downloaded a large cache of files.” Today, Senator Ron Wyden published a letter, which cites the 404 Media article and my analysis of TM SGNL, to Attorney General Pam Bondi, requesting that the Justice Department investigate the “serious threat to U.S. national security posed by TeleMessage, a federal contractor that sold dangerously insecure communications software to the White House and other federal agencies.” National security leaders using this app — which effectively just removes all of Signal’s actual security features by backing up all messages as plain text — is stupid it’s surprising, even from these idiots Trump has surrounded himself with. I mean think about how stupid it is that Mike Waltz was using this app while in front of press photographers at a Cabinet meeting. Lee goes deep, including an analysis of TM SGNL’s open source Android source code, to show that it’s designed to transmit backups of messages in plain text to publicly-facing servers. And it turns out those servers had easily-hackable flaws. See also: Wired: “The Company Behind the Signal Clone Mike Waltz Used Has Direct Access to User Chats”. ★
Micah Lee, in a spectacularly detailed post:
On Thursday, 404 Media reported that in the Reuters photo showing former National Security Advisor and war criminal Mike Waltz checking his Signal messages under the table, he was actually using an obscure modified Signal app called TM SGNL, and not the real and actually secure Signal app.
On Friday, I wrote an analysis of everything I could find out about TM SGNL using OSINT, including the fact that it’s nearly impossible to install without a device enrolled in an MDM service that’s tied to an Apple Business Manager or a Google Enterprise account.
On Saturday, after discovering that TeleMessage published the source code for the TM SGNL apps for Android and iPhone themselves, I re-published them on GitHub with the goal of making them easier to research. (It looks like the iOS source code is actually just unmodified Signal, so maybe they actually only published their Android code.)
On Saturday night, an anonymous source told me they hacked TeleMessage.
On Sunday, I, along with Joseph Cox, published an article about the hack to 404 Media (and to my blog).
On Monday, NBC News reported that TeleMessage suspended its service after a second hacker breached TeleMessage and “downloaded a large cache of files.”
Today, Senator Ron Wyden published a letter, which cites the 404 Media article and my analysis of TM SGNL, to Attorney General Pam Bondi, requesting that the Justice Department investigate the “serious threat to U.S. national security posed by TeleMessage, a federal contractor that sold dangerously insecure communications software to the White House and other federal agencies.”
National security leaders using this app — which effectively just removes all of Signal’s actual security features by backing up all messages as plain text — is stupid it’s surprising, even from these idiots Trump has surrounded himself with. I mean think about how stupid it is that Mike Waltz was using this app while in front of press photographers at a Cabinet meeting.
Lee goes deep, including an analysis of TM SGNL’s open source Android source code, to show that it’s designed to transmit backups of messages in plain text to publicly-facing servers. And it turns out those servers had easily-hackable flaws.
See also: Wired: “The Company Behind the Signal Clone Mike Waltz Used Has Direct Access to User Chats”.