Signal controversy: Why the secure messaging app is all over the news
You probably use text message, Facebook Messenger, WhatsApp, or even Instagram to chat with others. And while those messaging apps work fine, some still seek out alternatives that lean hard into a promise of security and privacy—like Signal. Signal is an end-to-end encrypted app (E2EE), which means it encrypts every message before it leaves your device, and that message can only be read after it arrives on a recipient’s device and gets decrypted. As it travels in between, even if it were to be intercepted, it couldn’t be read thanks to the encryption. The thing is, other apps like Messenger and WhatsApp also employ end-to-end encryption. So, what’s so special about Signal? And how did it become part of a small firestorm in US politics this week? Well, the app isn’t the problem. The issue is its use. As an E2EE app, Signal’s bona fides surpass Messenger and WhatsApp. For starters, Signal Messenger LLC—the company that develops Signal—created the encryption protocol used by all three messaging apps. (And to no one’s surprise, it’s called the Signal protocol.) Signal is also open source, which means the community can freely check its source code for any odd behavior or deceptive practices. No one but the sender and recipient(s) should be able to see messages in a secure messaging app. It’s scrambled all the way through, whether on your device (“at rest”) or while zipping through internet pipelines (“in transit”). Through use of both permanent and temporary encryption keys, your privacy should hold until decryption happens, even if those keys are compromised. In contrast, regular SMS (text) messages and email aren’t encrypted at all—those messages can easily be read during any point of their journey between you and other people. The problem is, even with E2EE in place, encryption alone can’t guarantee that information in messages won’t leak. Signal isn’t the only end-to-end encrypted messaging app available, but its protocol serves as the backbone of other popular EE2E messaging alternatives like WhatsApp.Leonidas Santana / Shutterstock.com Your device is only as secure as you are. If you use a weak PIN, or don’t lock your phone at all, then your messages can be read by others. Same if you download unvetted apps or sideload them—they could contain malware that’ll snoop on your decrypted messages. Yet another potential vulnerability are services and integrations, like third-party keyboards, that can be taken over or exploited by hackers. Even if you keep careful guard over your phone, any recipient of a message could take screenshots and later share them. The Atlantic article that kicked off the Signal news frenzy has just such an example of this. (“The Trump Administration Accidentally Texted Me Its War Plans.“) For these reasons, sensitive government conversations aren’t supposed to occur on third-party messaging apps. Top-secret communication is expected to be conducted under heavy restrictions—not just on secured devices, but often also at secured locations. People who have high security clearances might only be able to use approved devices while on site, and might even have to be within specific areas of a facility. Personal devices also may not be allowed to enter certain areas. In this way, risk is reduced that a phone (or a PC) could become compromised. So, that’s the main concern with Signal—it can’t be secured and controlled the same way as government systems. Another sticky spot is that government regulations require a record of communication. Signal—and other secure messaging apps—have the ability to automatically delete messages after a certain time has passed; if that setting is used, any lost conversations related to government proceedings would be in violation of the law. A screenshot from The Atlantic‘s article about being included in a Signal group discussing the US’s plans for action against Yemen. As you can see, it was possible to take screenshots of this encrypted chat.The Atlantic Overall, encrypted messaging apps are the ideal way to chat with others, even for us everyday folk. When you share personal information through text conversations—your bank, your destinations, your medical issues, and more—you want it all to be private… and protected from spying. News broke last December that Chinese hackers infiltrated US telecoms, meaning they could have seen many of the unencrypted text messages that users sent during that time. The gravity of the situation even prompted the FBI to advise a switch to encrypted messaging apps. Signal is just one option among several popular E2EE apps, and of the lot, it actually has the fewest privacy concerns. WhatsApp and Messenger are owned by Meta, while Telegram has been the target of multiple criticisms for weaker security. (Plus, Telegram is a known source for illicit activity, including the sale of stolen data by hackers.) If you’re curious about E2EE apps, you can read more

You probably use text message, Facebook Messenger, WhatsApp, or even Instagram to chat with others. And while those messaging apps work fine, some still seek out alternatives that lean hard into a promise of security and privacy—like Signal.
Signal is an end-to-end encrypted app (E2EE), which means it encrypts every message before it leaves your device, and that message can only be read after it arrives on a recipient’s device and gets decrypted. As it travels in between, even if it were to be intercepted, it couldn’t be read thanks to the encryption.
The thing is, other apps like Messenger and WhatsApp also employ end-to-end encryption. So, what’s so special about Signal? And how did it become part of a small firestorm in US politics this week? Well, the app isn’t the problem. The issue is its use.
As an E2EE app, Signal’s bona fides surpass Messenger and WhatsApp. For starters, Signal Messenger LLC—the company that develops Signal—created the encryption protocol used by all three messaging apps. (And to no one’s surprise, it’s called the Signal protocol.) Signal is also open source, which means the community can freely check its source code for any odd behavior or deceptive practices.
No one but the sender and recipient(s) should be able to see messages in a secure messaging app. It’s scrambled all the way through, whether on your device (“at rest”) or while zipping through internet pipelines (“in transit”). Through use of both permanent and temporary encryption keys, your privacy should hold until decryption happens, even if those keys are compromised. In contrast, regular SMS (text) messages and email aren’t encrypted at all—those messages can easily be read during any point of their journey between you and other people.
The problem is, even with E2EE in place, encryption alone can’t guarantee that information in messages won’t leak.

Leonidas Santana / Shutterstock.com
Your device is only as secure as you are. If you use a weak PIN, or don’t lock your phone at all, then your messages can be read by others. Same if you download unvetted apps or sideload them—they could contain malware that’ll snoop on your decrypted messages. Yet another potential vulnerability are services and integrations, like third-party keyboards, that can be taken over or exploited by hackers.
Even if you keep careful guard over your phone, any recipient of a message could take screenshots and later share them. The Atlantic article that kicked off the Signal news frenzy has just such an example of this. (“The Trump Administration Accidentally Texted Me Its War Plans.“)
For these reasons, sensitive government conversations aren’t supposed to occur on third-party messaging apps. Top-secret communication is expected to be conducted under heavy restrictions—not just on secured devices, but often also at secured locations. People who have high security clearances might only be able to use approved devices while on site, and might even have to be within specific areas of a facility. Personal devices also may not be allowed to enter certain areas. In this way, risk is reduced that a phone (or a PC) could become compromised.
So, that’s the main concern with Signal—it can’t be secured and controlled the same way as government systems.
Another sticky spot is that government regulations require a record of communication. Signal—and other secure messaging apps—have the ability to automatically delete messages after a certain time has passed; if that setting is used, any lost conversations related to government proceedings would be in violation of the law.
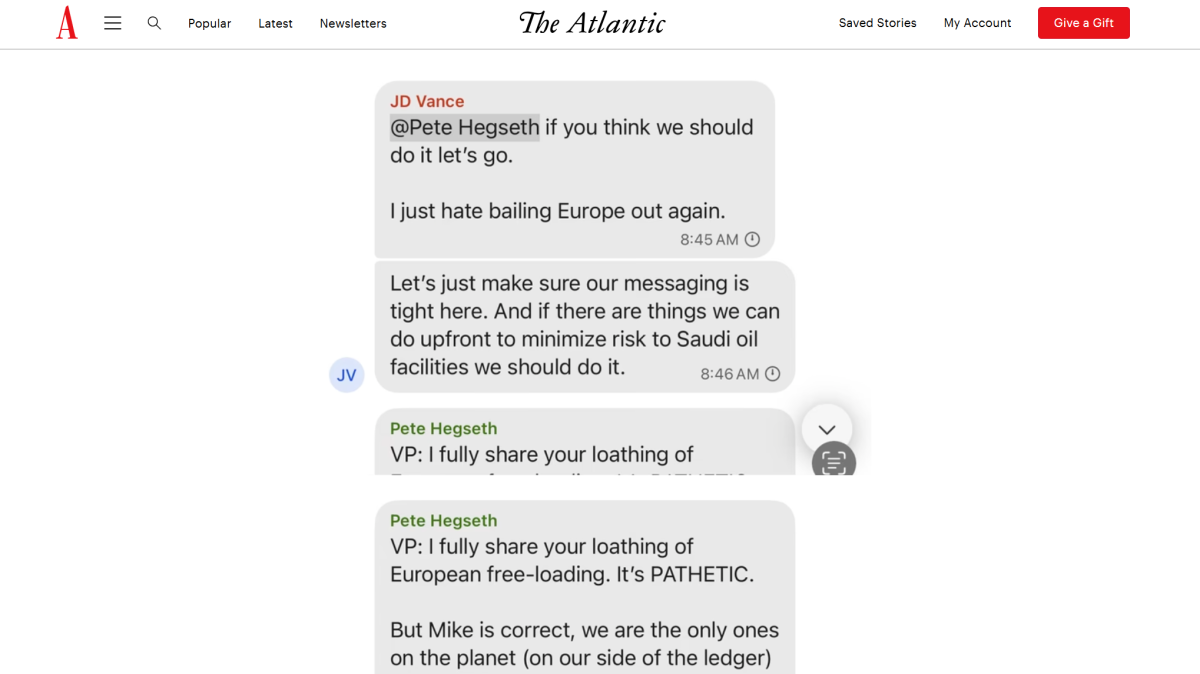
The Atlantic
Overall, encrypted messaging apps are the ideal way to chat with others, even for us everyday folk. When you share personal information through text conversations—your bank, your destinations, your medical issues, and more—you want it all to be private… and protected from spying. News broke last December that Chinese hackers infiltrated US telecoms, meaning they could have seen many of the unencrypted text messages that users sent during that time. The gravity of the situation even prompted the FBI to advise a switch to encrypted messaging apps.
Signal is just one option among several popular E2EE apps, and of the lot, it actually has the fewest privacy concerns. WhatsApp and Messenger are owned by Meta, while Telegram has been the target of multiple criticisms for weaker security. (Plus, Telegram is a known source for illicit activity, including the sale of stolen data by hackers.)
If you’re curious about E2EE apps, you can read more about Signal and how its encryption works, which also touches on alternatives like WhatsApp. Ultimately, if you don’t switch to an encrypted messaging app, you should at least think carefully about what you’re sharing—and how that info could be shared against your will.