Secure by Design: Node.js API Security Patterns for 2025
Security can't be an afterthought. In today's landscape, every Node.js API needs to be resilient from day one. Attackers aren't waiting, and neither should your defenses. In this guide, we'll explore practical, real-world patterns for securing APIs in 2025 — strategies that go beyond checklists and help you build confidence into every line of code. 1. Validate Inputs Relentlessly APIs are only as strong as the assumptions they don't make. Schema Validation: Use libraries like Zod or Yup to validate every incoming request, including query params, body payloads, and headers. Fail Fast: Reject malformed inputs immediately. Don't pass partially trusted data deeper into your app. Centralize Validation: Middleware-level validation prevents duplicated checks and ensures consistency. "If you don't validate inputs, the attacker will validate your assumptions for you." 2. Authenticate & Authorize Intelligently Authentication (who you are) and authorization (what you can do) must both be airtight. Short-Lived Tokens: Prefer access tokens with minimal lifespan. Use refresh tokens separately and securely. Role-Based Access Control (RBAC): Clearly separate permissions for users, admins, and systems. Claims-Based Auth: Don't rely solely on user IDs. Embed roles, permissions, or scopes inside JWT claims — and always validate them server-side. "Authorization failures are the silent killers of secure apps." 3. Rate Limit Aggressively No authentication layer is complete without abuse prevention. IP Throttling: Tools like express-rate-limit can stop basic spam. Global Rate Limits: Even authenticated users should have global limits to prevent abuse. Account Lockouts: Protect sensitive endpoints (login, password reset) with exponential backoff strategies. 4. Manage Secrets Like a Vault Secrets (API keys, DB passwords) must not leak — not in logs, not in Git, not anywhere. Use Secret Managers: Tools like AWS Secrets Manager, HashiCorp Vault, or Doppler. Environment Isolation: Never share dev secrets with prod. Auto-Rotate Keys: Set up secret rotation jobs to reduce exposure time. "Every leaked secret is a breach waiting to happen." 5. Monitor, Detect, and React Fast Prevention is ideal. Detection is mandatory. Centralized Logging: Aggregate and monitor all API logs — especially failed login attempts, 403s, and validation errors. Alerting Systems: Tools like PagerDuty or Opsgenie to notify instantly on suspicious behavior. Audit Trails: Keep immutable records of critical actions like auth changes, permission grants, etc. Real-World Reflection Picture a Node.js API fortified with strict validation, bulletproof authentication, tight rate limiting, no leaked secrets, and real-time monitoring. Suddenly, zero-day vulnerabilities become less scary, because your everyday practices already close 90% of easy attack vectors. This isn't theoretical. It's already happening in resilient Node.js production systems today. Conclusion In 2025, "Secure by Design" isn’t just a best practice—it’s survival. Building strong foundations from the beginning is cheaper, faster, and far less painful than trying to patch holes later. Ask yourself: "If an attacker tried to breach my API today, how many layers would they have to fight through?" The goal isn't perfection — it’s friction. Make every attack path harder, slower, and more detectable. Ready to rethink how you secure your APIs? Start now. Related Series If you enjoyed this post, check out our related series exploring deeper architectural strategies and real-time implementation techniques:

Security can't be an afterthought. In today's landscape, every Node.js API needs to be resilient from day one. Attackers aren't waiting, and neither should your defenses.
In this guide, we'll explore practical, real-world patterns for securing APIs in 2025 — strategies that go beyond checklists and help you build confidence into every line of code.

1. Validate Inputs Relentlessly
APIs are only as strong as the assumptions they don't make.
- Schema Validation: Use libraries like Zod or Yup to validate every incoming request, including query params, body payloads, and headers.
- Fail Fast: Reject malformed inputs immediately. Don't pass partially trusted data deeper into your app.
- Centralize Validation: Middleware-level validation prevents duplicated checks and ensures consistency.
"If you don't validate inputs, the attacker will validate your assumptions for you."
2. Authenticate & Authorize Intelligently
Authentication (who you are) and authorization (what you can do) must both be airtight.
- Short-Lived Tokens: Prefer access tokens with minimal lifespan. Use refresh tokens separately and securely.
- Role-Based Access Control (RBAC): Clearly separate permissions for users, admins, and systems.
- Claims-Based Auth: Don't rely solely on user IDs. Embed roles, permissions, or scopes inside JWT claims — and always validate them server-side.
"Authorization failures are the silent killers of secure apps."
3. Rate Limit Aggressively
No authentication layer is complete without abuse prevention.
- IP Throttling: Tools like express-rate-limit can stop basic spam.
- Global Rate Limits: Even authenticated users should have global limits to prevent abuse.
- Account Lockouts: Protect sensitive endpoints (login, password reset) with exponential backoff strategies.
4. Manage Secrets Like a Vault
Secrets (API keys, DB passwords) must not leak — not in logs, not in Git, not anywhere.
- Use Secret Managers: Tools like AWS Secrets Manager, HashiCorp Vault, or Doppler.
- Environment Isolation: Never share dev secrets with prod.
- Auto-Rotate Keys: Set up secret rotation jobs to reduce exposure time.
"Every leaked secret is a breach waiting to happen."
5. Monitor, Detect, and React Fast
Prevention is ideal. Detection is mandatory.
- Centralized Logging: Aggregate and monitor all API logs — especially failed login attempts, 403s, and validation errors.
- Alerting Systems: Tools like PagerDuty or Opsgenie to notify instantly on suspicious behavior.
- Audit Trails: Keep immutable records of critical actions like auth changes, permission grants, etc.
Real-World Reflection
Picture a Node.js API fortified with strict validation, bulletproof authentication, tight rate limiting, no leaked secrets, and real-time monitoring. Suddenly, zero-day vulnerabilities become less scary, because your everyday practices already close 90% of easy attack vectors.
This isn't theoretical. It's already happening in resilient Node.js production systems today.
Conclusion
In 2025, "Secure by Design" isn’t just a best practice—it’s survival. Building strong foundations from the beginning is cheaper, faster, and far less painful than trying to patch holes later.
Ask yourself: "If an attacker tried to breach my API today, how many layers would they have to fight through?"
The goal isn't perfection — it’s friction. Make every attack path harder, slower, and more detectable.
Ready to rethink how you secure your APIs? Start now.
Related Series
If you enjoyed this post, check out our related series exploring deeper architectural strategies and real-time implementation techniques:








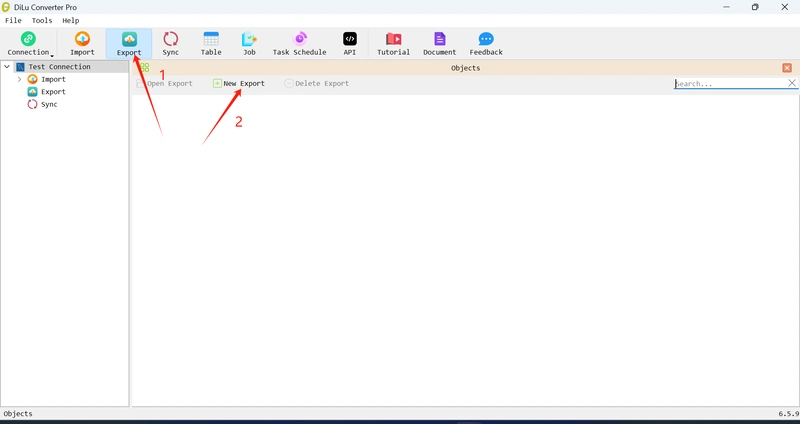







![New iPhone Factory Goes Live in India, Another Just Days Away [Report]](https://www.iclarified.com/images/news/97165/97165/97165-640.jpg)