Insights into Kerberos
A crucial protocol in the context of AD is Kerberos 1. Originally developed at MIT as part of Project Athena in 1988 2, Kerberos has become a cornerstone for secure authentication in distributed systems and plays a central role in securing interactions within Active Directory domains. The general goal of Kerberos is to authenticate a user to a service over an insecure network. This is achieved by providing a way of mutual authentication, a process in which both the user and the service verify each other’s identity while ensuring the authentication messages are timely and uncompromised. To accomplish this, each party generates an independent challenge to confirm the interaction’s freshness. The challenge must be returned as part of the authenticator, encrypted using the private key of the party issuing the challenge. A key requirement of the challenge is that it must not have been used previously for authenticating the two parties. This uniqueness can be ensured by one of three methods: maintaining a record of all previously used challenges, employing a monotonically increasing sequence such as timestamps, or generating sufficiently large random numbers to achieve uniqueness probabilistically 3. To fully grasp the functioning of Kerberos, it is essential to become acquainted with the following key terminology 4: Realm: A domain or group of systems over which Kerberos has authority to authenticate users and services. Multiple realms can exist and can be interconnected to facilitate authentication across domains. Principal: A unique identity within a realm, which can represent either a user or a service. Client: A process acting on behalf of a user to access a specific service. User: An individual entity within a realm. A realm may host multiple users and their associated clients. Service: A resource or application that a client can access, such as a file server, application, or other networked resource. Multiple services can exist within a single realm. Key Distribution Center (KDC): A centralized authority responsible for issuing tickets and generating temporary session keys to facilitate secure authentication between users and services. The KDC maintains all symmetric keys used within the realm. It is composed of two main components: Authentication Server: Validates the identity of users making access requests and issues a Ticket Granting Ticket (TGT) for further authentication. Ticket Granting Server (TGS): Verifies access requests from users for specific services and issues Service Tickets to enable secure communication with the requested service. Authenticators: Records containing information, such as timestamps, generated using the session key shared between the client and the server. Tickets: Encrypted data structures containing information such as service keys, timestamps, and client identifiers. Tickets are encrypted with the secret key of the destination server to ensure secure transmission. The following points provide a high-level overview of the authentication process when a user attempts to access a Kerberos-protected service, while the Figure below illustrates the detailed message exchanges 4: The user initiates communication with the Authentication Server by sending an unencrypted message. The Authentication Server verifies the user’s identity and responds with two components: a TGT and a second message encrypted with the user’s secret key, which is securely stored within the KDC. The user decrypts the response using their secret key and forwards a new request to the TGS, including the TGT obtained from the Authentication Server. The TGS decrypts and validates the TGT. Upon successful validation, the TGS generates a service ticket specific to the requested service. The service ticket, along with additional information, is sent back to the user in an encrypted format. The user decrypts the received message, constructs an authenticator message, and forwards both the authenticator and the service ticket to the requested service. The service decrypts and validates the received messages. Upon successful validation, it generates its own authenticator message to confirm the user’s identity and the integrity of the communication. The service sends the final authenticator message back to the user, completing the mutual authentication process. The Kerberos flow. You can download a full-res version here.Based on this. B. Neuman and T. Ts’o, "Kerberos: an authentication service for computer networks," IEEE Communications Magazine, vol. 32, no. 9, pp. 33–38, Sep. 1994, conference Name: IEEE Communications Magazine. Online ↩ J. G. Steiner, C. Neuman, and J. I. Schiller, "Kerberos: An Authentication Service for Open Network Systems," 1988. ↩ D. Otway and O. Rees, "Efficient and timely mutual authentication," ACM SIGOPS Operating Systems Review, vol. 21, no. 1, pp. 8–10, Jan. 1987. Online ↩ Destination Certification, "Kerberos Authentication Explained | A de
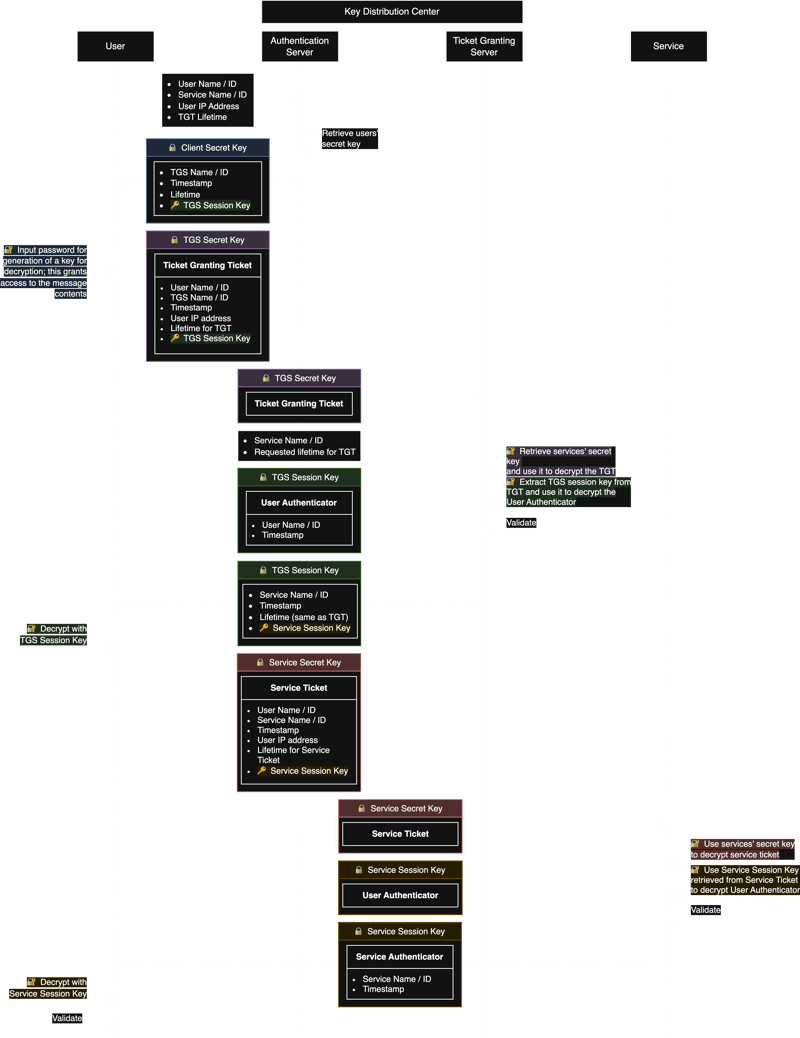
A crucial protocol in the context of AD is Kerberos 1. Originally developed at MIT as part of Project Athena in 1988 2, Kerberos has become a cornerstone for secure authentication in distributed systems and plays a central role in securing interactions within Active Directory domains. The general goal of Kerberos is to authenticate a user to a service over an insecure network. This is achieved by providing a way of mutual authentication, a process in which both the user and the service verify each other’s identity while ensuring the authentication messages are timely and uncompromised. To accomplish this, each party generates an independent challenge to confirm the interaction’s freshness. The challenge must be returned as part of the authenticator, encrypted using the private key of the party issuing the challenge. A key requirement of the challenge is that it must not have been used previously for authenticating the two parties. This uniqueness can be ensured by one of three methods: maintaining a record of all previously used challenges, employing a monotonically increasing sequence such as timestamps, or generating sufficiently large random numbers to achieve uniqueness probabilistically 3. To fully grasp the functioning of Kerberos, it is essential to become acquainted with the following key terminology 4:
- Realm: A domain or group of systems over which Kerberos has authority to authenticate users and services. Multiple realms can exist and can be interconnected to facilitate authentication across domains.
- Principal: A unique identity within a realm, which can represent either a user or a service.
- Client: A process acting on behalf of a user to access a specific service.
- User: An individual entity within a realm. A realm may host multiple users and their associated clients.
- Service: A resource or application that a client can access, such as a file server, application, or other networked resource. Multiple services can exist within a single realm.
-
Key Distribution Center (KDC): A centralized authority responsible for issuing tickets and generating temporary session keys to facilitate secure authentication between users and services. The KDC maintains all symmetric keys used within the realm. It is composed of two main components:
- Authentication Server: Validates the identity of users making access requests and issues a Ticket Granting Ticket (TGT) for further authentication.
- Ticket Granting Server (TGS): Verifies access requests from users for specific services and issues Service Tickets to enable secure communication with the requested service.
Authenticators: Records containing information, such as timestamps, generated using the session key shared between the client and the server.
Tickets: Encrypted data structures containing information such as service keys, timestamps, and client identifiers. Tickets are encrypted with the secret key of the destination server to ensure secure transmission.
The following points provide a high-level overview of the authentication process when a user attempts to access a Kerberos-protected service, while the Figure below illustrates the detailed message exchanges 4:
- The user initiates communication with the Authentication Server by sending an unencrypted message.
- The Authentication Server verifies the user’s identity and responds with two components: a TGT and a second message encrypted with the user’s secret key, which is securely stored within the KDC.
- The user decrypts the response using their secret key and forwards a new request to the TGS, including the TGT obtained from the Authentication Server.
- The TGS decrypts and validates the TGT. Upon successful validation, the TGS generates a service ticket specific to the requested service.
- The service ticket, along with additional information, is sent back to the user in an encrypted format.
- The user decrypts the received message, constructs an authenticator message, and forwards both the authenticator and the service ticket to the requested service.
- The service decrypts and validates the received messages. Upon successful validation, it generates its own authenticator message to confirm the user’s identity and the integrity of the communication.
- The service sends the final authenticator message back to the user, completing the mutual authentication process.

The Kerberos flow. You can download a full-res version here.
Based on this.
-
B. Neuman and T. Ts’o, "Kerberos: an authentication service for computer networks," IEEE Communications Magazine, vol. 32, no. 9, pp. 33–38, Sep. 1994, conference Name: IEEE Communications Magazine. Online ↩
-
J. G. Steiner, C. Neuman, and J. I. Schiller, "Kerberos: An Authentication Service for Open Network Systems," 1988. ↩
-
D. Otway and O. Rees, "Efficient and timely mutual authentication," ACM SIGOPS Operating Systems Review, vol. 21, no. 1, pp. 8–10, Jan. 1987. Online ↩
-
Destination Certification, "Kerberos Authentication Explained | A deep dive," Apr. 2020. Online ↩










![From hating coding to programming satellites at age 37 with Francesco Ciulla [Podcast #165]](https://cdn.hashnode.com/res/hashnode/image/upload/v1742585568977/09b25b8e-8c92-4f4b-853f-64b7f7915980.png?#)