File Upload Vulnerabilities 2025
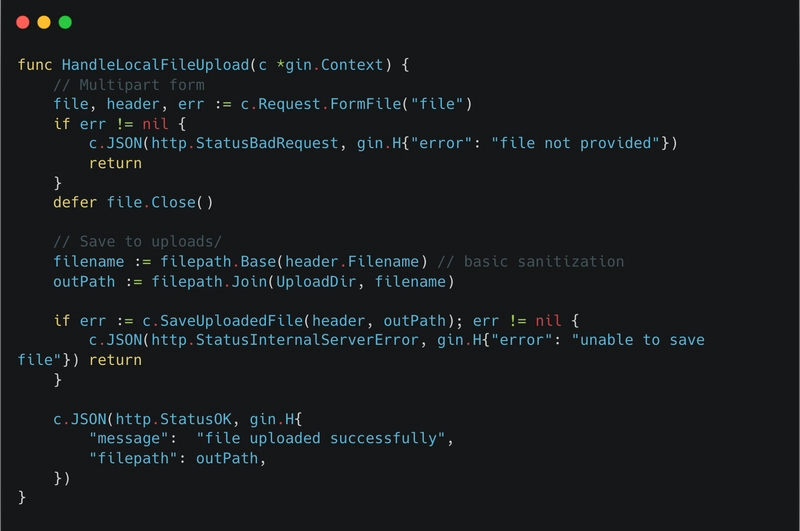
## What is File Upload Vulnerability? When a webserver allows users to upload files to its file system without sufficiently validating things like their name, type, content, size. ** Common Attacks: ** Multiple Extension : A multiple extension attack in file upload vulnerabilities involves uploading a file with a double extension (e.g., file.php.jpg) to bypass security checks, tricking the server into executing malicious code disguised as a safe file type. Bypassing Blacklisted Extension : Blacklists struggle to block malicious files (e.g., script.php.jpg bypassing as an image) without restricting legitimate files (e.g., valid .jpg uploads), as attackers use tricks like double extensions or rare file types (ps2, sct, cpl). Fuzzing & Black Box Techniques : Fuzzing & black box testing involves sending random or malformed inputs (e.g., unexpected file extensions like .php%00.jpg) to a system to uncover vulnerabilities, without knowledge of its internal code, mimicking real-world attacks. Path Traversal Risks : File uploads allow attackers to access or overwrite sensitive files (e.g., ../../etc/passwd) by manipulating file paths, bypassing directory restrictions and potentially compromising the server. Bypassing Mime Checks : Bypassing MIME type checks involves uploading a malicious file (e.g., a script disguised as image/jpeg by altering headers) to trick the server into accepting it, exploiting weak validation that trusts client-provided MIME types. Upload Using Put Method : File upload using the PUT method allows attackers to directly upload malicious files (e.g., malware.php) to a server if improperly configured, bypassing typical upload forms by exploiting HTTP PUT permissions. SVG file upload : SVG file uploads can be exploited to execute malicious JavaScript (e.g., alert('XSS') embedded in the SVG), bypassing image validation due to SVG's XML-based structure, leading to XSS or other attacks. "If server-side file sanitization is in place, only SVG file upload attacks may work, as sanitization often misses embedded JavaScript in SVG files." ** Attacks in 2025: ** *Magic Number Shifting *: A magic number is a unique sequence of bytes (or pattern) located at the beginning of a file that identifies its type. For example: JPEG files start with FF D8 FF PNG files start with 89 50 4E 47 WebP files start with 52 49 46 46 00 00 00 57 45 42 50 File-upload security mechanisms often check these magic numbers to verify the file type before allowing uploads. Attack Scenario : In a shifting magic number attack, an attacker may alter or move the magic number in such a way that it’s no longer in its original place but still part of the file, effectively bypassing checks. The attacker uploads a file that appears to be a harmless image (e.g., a JPEG or PNG). The magic number of the image is shifted — for example, moving the FF D8 FF (JPEG signature) to somewhere in the middle of the file. The file is still technically a JPEG image, but the header is malformed or doesn’t match what the server expects. The server may allow the file upload based on the initial checks (e.g., validating file extensions or basic magic number). The attacker executes their payload (such as arbitrary code execution or XSS) hidden inside the rest of the file, bypassing the magic number check. Vulnerable ICO Files: ICO files are commonly used for icons in Windows, so many websites allow them to be uploaded. But on a Windows server, these files can be risky. If the server processes or resizes the uploaded ICO file using tools like GDI+, Windows Shell, or ImageMagick, it could crash or even allow hackers to run malicious code — especially on older servers that aren’t updated. WebP Files : WebP is a modern image format developed by Google. But in 2023, a critical vulnerability (nicknamed “WebPocalypse”) was found that affected almost every browser and app using libwebp. A malformed WebP image could lead to heap buffer overflows, enabling attackers to run malicious code on the target machine. CVE-2023-4863 impacted Chrome, Firefox, Electron apps, and more. For example, CVE-2017-0235 was a vulnerability in Windows GDI+ where a specially crafted ICO file could lead to remote code execution. CVE related to File Upload Vulnerabilities in 2025 : CVE-2025-31324 – SAP NetWeaver Visual Composer CVE-2025-22654 – Kodeshpa Simplified CVE-2025-1165 – Lumsoft ERP 8 Mitigations : Strict File Type Validation: Only allow specific, trusted file formats (e.g., images) and check the file's content to ensure it matches the expected type. Sanitize Metadata: Remove any embedded metadata from uploaded files (like EXIF, IPTC, or XMP) to prevent leakage of sensitive information. Limit Execution Permissions: Ensure uploaded files cannot be executed by restricting file permissions and avoiding the execution of files in directories accessible via the web. Use Content Security Policies: Implement strict content secur

## What is File Upload Vulnerability?
When a webserver allows users to upload files to its file system without sufficiently validating things like their name, type, content, size.
**
Common Attacks:
**
Multiple Extension : A multiple extension attack in file upload vulnerabilities involves uploading a file with a double extension (e.g., file.php.jpg) to bypass security checks, tricking the server into executing malicious code disguised as a safe file type.
Bypassing Blacklisted Extension : Blacklists struggle to block malicious files (e.g., script.php.jpg bypassing as an image) without restricting legitimate files (e.g., valid .jpg uploads), as attackers use tricks like double extensions or rare file types (ps2, sct, cpl).
Fuzzing & Black Box Techniques : Fuzzing & black box testing involves sending random or malformed inputs (e.g., unexpected file extensions like .php%00.jpg) to a system to uncover vulnerabilities, without knowledge of its internal code, mimicking real-world attacks.
Path Traversal Risks : File uploads allow attackers to access or overwrite sensitive files (e.g., ../../etc/passwd) by manipulating file paths, bypassing directory restrictions and potentially compromising the server.
Bypassing Mime Checks : Bypassing MIME type checks involves uploading a malicious file (e.g., a script disguised as image/jpeg by altering headers) to trick the server into accepting it, exploiting weak validation that trusts client-provided MIME types.
Upload Using Put Method : File upload using the PUT method allows attackers to directly upload malicious files (e.g., malware.php) to a server if improperly configured, bypassing typical upload forms by exploiting HTTP PUT permissions.
SVG file upload : SVG file uploads can be exploited to execute malicious JavaScript (e.g., alert('XSS') embedded in the SVG), bypassing image validation due to SVG's XML-based structure, leading to XSS or other attacks.
"If server-side file sanitization is in place, only SVG file upload attacks may work, as sanitization often misses embedded JavaScript in SVG files."
**
Attacks in 2025:
**
*Magic Number Shifting *: A magic number is a unique sequence of bytes (or pattern) located at the beginning of a file that identifies its type. For example:
JPEG files start with FF D8 FF
PNG files start with 89 50 4E 47
WebP files start with 52 49 46 46 00 00 00 57 45 42 50
File-upload security mechanisms often check these magic numbers to verify the file type before allowing uploads.
Attack Scenario :
In a shifting magic number attack, an attacker may alter or move the magic number in such a way that it’s no longer in its original place but still part of the file, effectively bypassing checks.
The attacker uploads a file that appears to be a harmless image (e.g., a JPEG or PNG).
The magic number of the image is shifted — for example, moving the FF D8 FF (JPEG signature) to somewhere in the middle of the file.
The file is still technically a JPEG image, but the header is malformed or doesn’t match what the server expects.
The server may allow the file upload based on the initial checks (e.g., validating file extensions or basic magic number).
The attacker executes their payload (such as arbitrary code execution or XSS) hidden inside the rest of the file, bypassing the magic number check.
Vulnerable ICO Files: ICO files are commonly used for icons in Windows, so many websites allow them to be uploaded. But on a Windows server, these files can be risky. If the server processes or resizes the uploaded ICO file using tools like GDI+, Windows Shell, or ImageMagick, it could crash or even allow hackers to run malicious code — especially on older servers that aren’t updated.
WebP Files : WebP is a modern image format developed by Google. But in 2023, a critical vulnerability (nicknamed “WebPocalypse”) was found that affected almost every browser and app using libwebp. A malformed WebP image could lead to heap buffer overflows, enabling attackers to run malicious code on the target machine.
CVE-2023-4863 impacted Chrome, Firefox, Electron apps, and more.
For example, CVE-2017-0235 was a vulnerability in Windows GDI+ where a specially crafted ICO file could lead to remote code execution.
CVE related to File Upload Vulnerabilities in 2025 :
- CVE-2025-31324 – SAP NetWeaver Visual Composer
- CVE-2025-22654 – Kodeshpa Simplified
- CVE-2025-1165 – Lumsoft ERP 8
Mitigations :
Strict File Type Validation: Only allow specific, trusted file formats (e.g., images) and check the file's content to ensure it matches the expected type.
Sanitize Metadata: Remove any embedded metadata from uploaded files (like EXIF, IPTC, or XMP) to prevent leakage of sensitive information.
Limit Execution Permissions: Ensure uploaded files cannot be executed by restricting file permissions and avoiding the execution of files in directories accessible via the web.
Use Content Security Policies: Implement strict content security policies (CSP) to prevent scripts from running within uploaded files, such as SVG or image files with embedded JavaScript.
Regularly Update Security Tools: Keep your image processing and file upload libraries up to date to mitigate any vulnerabilities, especially those related to buffer overflow or remote code execution.