EXPOSED! Why Hackers Are Silently Targeting Your Security Misconfigurations
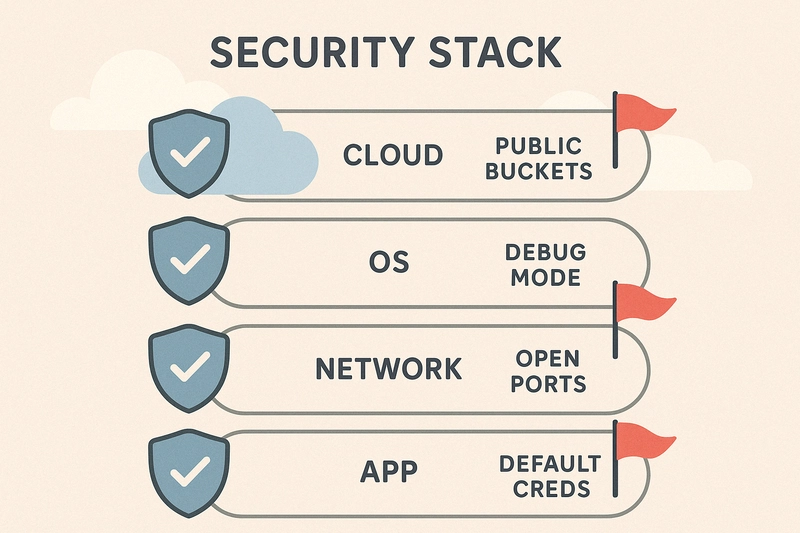
Introduction When I was testing my first AWS S3 bucket during a beginner lab exercise, I was shocked to find it publicly accessible by default—no warnings, no barriers. That moment made something very clear: misconfigurations are everywhere, and they’re silently waiting to be exploited. In this blog, you’ll discover what security misconfigurations are, how they’re exploited in the real world, and how to bulletproof your systems against them. Whether you’re a beginner, a developer, or a security enthusiast, this is your no-fluff guide to understanding the silent killers of modern infrastructure.
Introduction
When I was testing my first AWS S3 bucket during a beginner lab exercise, I was shocked to find it publicly accessible by default—no warnings, no barriers. That moment made something very clear: misconfigurations are everywhere, and they’re silently waiting to be exploited.
In this blog, you’ll discover what security misconfigurations are, how they’re exploited in the real world, and how to bulletproof your systems against them. Whether you’re a beginner, a developer, or a security enthusiast, this is your no-fluff guide to understanding the silent killers of modern infrastructure.