Exercise 03: Create and configure Azure Firewall
Scenario Your organization requires centralized network security for the application virtual network. As the application usage increases, more granular application-level filtering and advanced threat protection will be needed. Also, it is expected the application will need continuous updates from Azure DevOps pipelines. You identify these requirements. Azure Firewall is required for additional security in the app-vnet. A firewall policy should be configured to help manage access to the application. A firewall policy application rule is required. This rule will allow the application access to Azure DevOps so the application code can be updated. A firewall policy network rule is required. This rule will allow DNS resolution. Skilling tasks Create an Azure Firewall. Create and configure a firewall policy Create an application rule collection. Create a network rule collection. Create Azure Firewall subnet in our existing virtual network In the search box at the top of the portal, enter Virtual networks. Select Virtual networks in the search results. Select app-vnet. Select Subnets. Select + Subnet. Enter the following information and select Save. Name= AzureFirewallSubnet Address range= 10.1.63.0/26 Create an Azure Firewall In the search box at the top of the portal, enter Firewall. Select Firewall in the search results. Select + Create. Create a firewall by using the values in the following table. For any property that is not specified, use the default value. Note: Azure Firewall can take a few minutes to deploy. Update the Firewall Policy In the portal, search for and select Firewall Policies. Select fw-policy. Add an application rule In the Settings blade, select Application rules and then Add a rule collection. Configure the application rule collection and then select Add. Name= app-vnet-fw-rule-collection Rule collection type= Application Priority= 200 Rule collection action= Allow Rule collection group= DefaultApplicationRuleCollectionGroup Name= AllowAzurePipelines Source type= IP address Source= 10.1.0.0/23 Protocol= https Destination type= FQDN Destination= dev.azure.com, azure.microsoft.com Note: The AllowAzurePipelines rule allows the web application to access Azure Pipelines. The rule allows the web application to access the Azure DevOps service and the Azure website. Add a network rule In the Settings blade, select Network rules and then Add a network collection. Configure the network rule and then select Add. Name= app-vnet-fw-nrc-dns Rule collection type= Network Priority= 200 Rule collection action= Allow Rule collection group= DefaultNetworkRuleCollectionGroup Rule= AllowDns Source= 10.1.0.0/23 Protocol= UDP Destination ports= 53 Destination addresses= 1.1.1.1, 1.0.0.1 Verify the firewall and firewall policy status In the portal search for and select Firewall. View the app-vnet-firewall and ensure the Provisioning state is Succeeded. This may take a few minutes. In the portal serach for and select Firewall policies. View the fw-policy and ensure the Provisioning state is Succeeded. This may take a few minutes.
Scenario
Your organization requires centralized network security for the application virtual network. As the application usage increases, more granular application-level filtering and advanced threat protection will be needed. Also, it is expected the application will need continuous updates from Azure DevOps pipelines. You identify these requirements.
Azure Firewall is required for additional security in the app-vnet.
A firewall policy should be configured to help manage access to the application.
A firewall policy application rule is required. This rule will allow the application access to Azure DevOps so the application code can be updated.
A firewall policy network rule is required. This rule will allow DNS resolution.
Skilling tasks
Create an Azure Firewall.
Create and configure a firewall policy
Create an application rule collection.
Create a network rule collection.
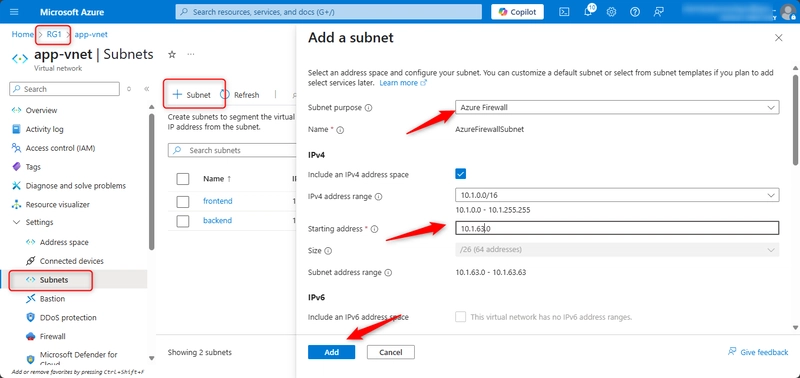
Create Azure Firewall subnet in our existing virtual network
In the search box at the top of the portal, enter Virtual networks. Select Virtual networks in the search results.
Select app-vnet.
Select Subnets.
Select + Subnet.
Enter the following information and select Save.
Name= AzureFirewallSubnet
Address range= 10.1.63.0/26

Create an Azure Firewall
In the search box at the top of the portal, enter Firewall. Select Firewall in the search results.
Select + Create.
Create a firewall by using the values in the following table. For any property that is not specified, use the default value.
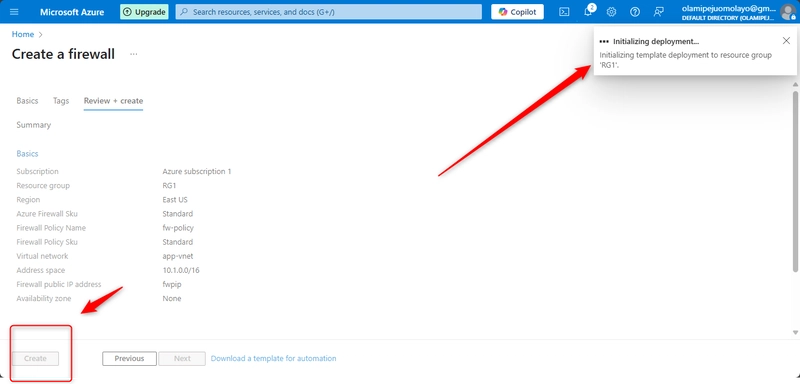
Note: Azure Firewall can take a few minutes to deploy.
Update the Firewall Policy
In the portal, search for and select Firewall Policies.
Select fw-policy.
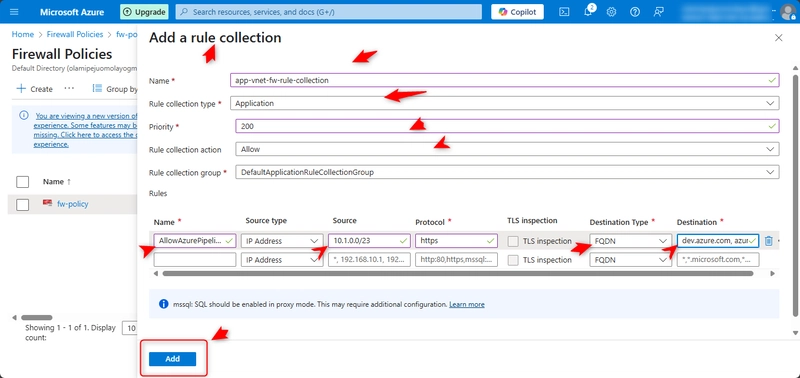
Add an application rule
In the Settings blade, select Application rules and then Add a rule collection.
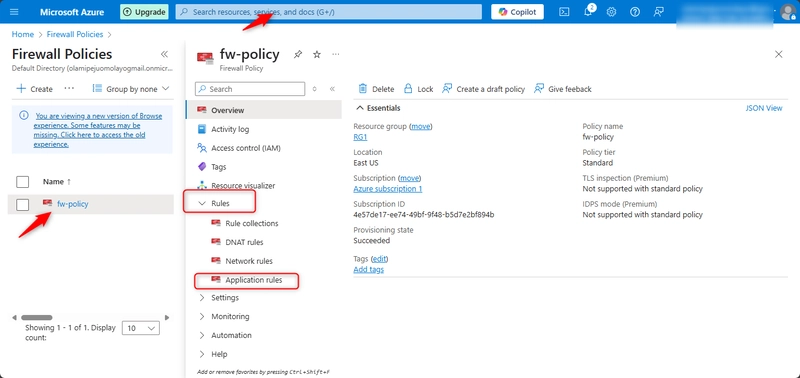
Configure the application rule collection and then select Add.
Name= app-vnet-fw-rule-collection
Rule collection type= Application
Priority= 200
Rule collection action= Allow
Rule collection group= DefaultApplicationRuleCollectionGroup
Name= AllowAzurePipelines
Source type= IP address
Source= 10.1.0.0/23
Protocol= https
Destination type= FQDN
Destination= dev.azure.com, azure.microsoft.com
Note: The AllowAzurePipelines rule allows the web application to access Azure Pipelines. The rule allows the web application to access the Azure DevOps service and the Azure website.
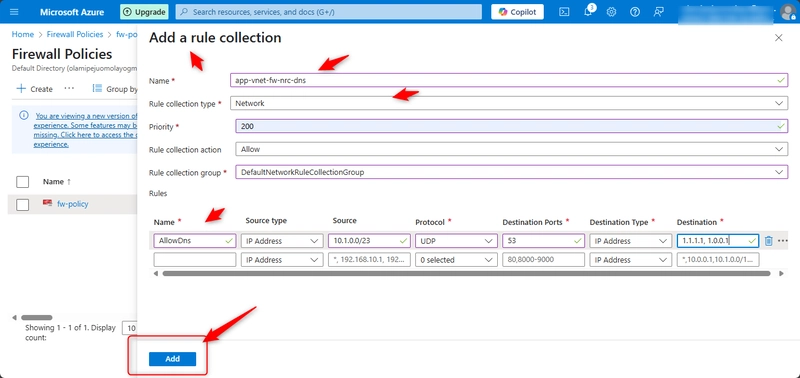
Add a network rule
In the Settings blade, select Network rules and then Add a network collection.
Configure the network rule and then select Add.
Name= app-vnet-fw-nrc-dns
Rule collection type= Network
Priority= 200
Rule collection action= Allow
Rule collection group= DefaultNetworkRuleCollectionGroup
Rule= AllowDns
Source= 10.1.0.0/23
Protocol= UDP
Destination ports= 53
Destination addresses= 1.1.1.1, 1.0.0.1
Verify the firewall and firewall policy status
In the portal search for and select Firewall.
View the app-vnet-firewall and ensure the Provisioning state is Succeeded. This may take a few minutes.
In the portal serach for and select Firewall policies.
View the fw-policy and ensure the Provisioning state is Succeeded. This may take a few minutes.















![New iPhone Factory Goes Live in India, Another Just Days Away [Report]](https://www.iclarified.com/images/news/97165/97165/97165-640.jpg)