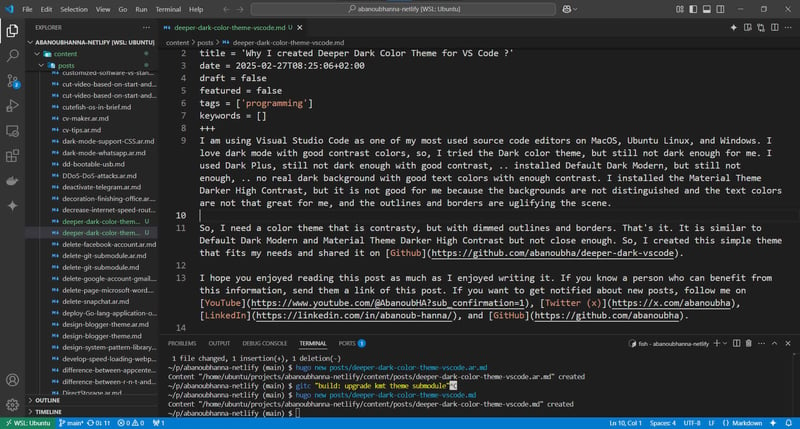
Cool "iptables" commands - Linux
The iptables command is a formidable tool that allows you to do many cool things. Here are some of my favorite uses: Allow all loopback ( lo0 ) traffic, and reject traffic to localhost that does not originate from lo0. iptables -A INPUT -i lo -j ACCEPT iptables -A INPUT ! -i lo -s 127.0.0.0/8 -j REJECT Allow ping. iptables -A INPUT -p icmp -m state --state NEW --icmp-type 8 -j ACCEPT Allow SSH connections. iptables -A INPUT -p tcp --dport 22 -m state --state NEW -j ACCEPT Allow HTTP and HTTPS connections from anywhere ( standard web server ports ). iptables -A INPUT -p tcp --dport 80 -m state --state NEW -j ACCEPT iptables -A INPUT -p tcp --dport 443 -m state --state NEW -j ACCEPT Allow inbound traffic from established connections. This includes ICMP error returns. iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT Log incoming, but denied traffic. iptables -A INPUT -m limit --limit 5/min -j LOG --log-prefix "iptables_INPUT_denied: " --log-level 7 Reject all inbound traffic that hasn't been explicitly allowed by previous rules. iptables -A INPUT -j REJECT Log any traffic that was sent to you for forwarding ( applies to packets being routed through your machine, not destined for it ). iptables -A FORWARD -m limit --limit 5/min -j LOG --log-prefix "iptables_FORWARD_denied: " --log-level 7 Reject all traffic forwarding. iptables -A FORWARD -j REJECT Bonus: nullrouting an IP with the "ip" command ( useful against volumetric DOS attacks ). ip route add blackhole 192.168.1.100 And to remove the nullroute: ip route del blackhole 192.168.1.100
The iptables command is a formidable tool that allows you to do many cool things.
Here are some of my favorite uses:
Allow all loopback ( lo0 ) traffic, and reject traffic to localhost that does not originate from lo0.
iptables -A INPUT -i lo -j ACCEPT
iptables -A INPUT ! -i lo -s 127.0.0.0/8 -j REJECT
Allow ping.
iptables -A INPUT -p icmp -m state --state NEW --icmp-type 8 -j ACCEPT
Allow SSH connections.
iptables -A INPUT -p tcp --dport 22 -m state --state NEW -j ACCEPT
Allow HTTP and HTTPS connections from anywhere ( standard web server ports ).
iptables -A INPUT -p tcp --dport 80 -m state --state NEW -j ACCEPT
iptables -A INPUT -p tcp --dport 443 -m state --state NEW -j ACCEPT
Allow inbound traffic from established connections. This includes ICMP error returns.
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
Log incoming, but denied traffic.
iptables -A INPUT -m limit --limit 5/min -j LOG --log-prefix "iptables_INPUT_denied: " --log-level 7
Reject all inbound traffic that hasn't been explicitly allowed by previous rules.
iptables -A INPUT -j REJECT
Log any traffic that was sent to you for forwarding ( applies to packets being routed through your machine, not destined for it ).
iptables -A FORWARD -m limit --limit 5/min -j LOG --log-prefix "iptables_FORWARD_denied: " --log-level 7
Reject all traffic forwarding.
iptables -A FORWARD -j REJECT
Bonus: nullrouting an IP with the "ip" command ( useful against volumetric DOS attacks ).
ip route add blackhole 192.168.1.100
And to remove the nullroute:
ip route del blackhole 192.168.1.100



















_JIRAROJ_PRADITCHAROENKUL_Alamy.jpg?#)

_Tanapong_Sungkaew_Alamy.jpg?#)


































![‘Yellowjackets’ Stars on Filming [SPOILER]’s ‘Heartbreaking’ Death in Episode 6 and Why It Needed to Happen That Way](https://variety.com/wp-content/uploads/2025/03/Yellowjackts_306_CB_0809_1106_RT.jpg?#)