AWS WAF, Shield, and GuardDuty: Security at Scale
As businesses migrate to the cloud, ensuring robust security against cyber threats becomes a top priority. AWS provides a multi-layered defence strategy through three key security services: AWS Web Application Firewall (WAF) – Protects web applications from malicious traffic. AWS Shield – Provides DDoS protection at different levels. Amazon GuardDuty – Continuously monitors AWS environments for potential security threats. Together, these services help organizations detect, prevent, and mitigate security risks at scale, ensuring high availability and data integrity for applications running on AWS. AWS WAF: Web Application Firewall AWS WAF (Web Application Firewall) is a security layer designed to protect web applications from common attack patterns such as SQL injection (SQLi), Cross-Site Scripting (XSS), and bot-driven abuse. How AWS WAF Works AWS WAF filters incoming HTTP/HTTPS traffic based on custom rules that block, allow, or count requests. It is deployed alongside: Amazon CloudFront – To protect CDN-distributed applications. Application Load Balancer (ALB) – To secure applications running on EC2 instances. API Gateway – To prevent abuse of serverless APIs. Key Features of AWS WAF Rule-Based Filtering – Users can define rules to block specific IPs, patterns, or behaviours. AWS Managed Rules – Pre-configured security rules for OWASP Top 10 threats. Rate-Based Throttling – Protects applications from brute-force and bot attacks. Logging & Monitoring – Integrates with Amazon CloudWatch Logs for real-time analysis. Example: Blocking SQL Injection Attacks AWS WAF detects malicious queries trying to exploit vulnerabilities in web applications. { "Name": "SQLInjectionRule", "Priority": 1, "Statement": { "SqliMatchStatement": { "FieldToMatch": { "UriPath": {} }, "TextTransformations": [{ "Priority": 0, "Type": "URL_DECODE" }] } }, "Action": { "Block": {} } } This rule blocks SQL injection attempts by inspecting the request URI path. AWS Shield: DDoS Protection Distributed Denial of Service (DDoS) attacks are among the most disruptive cyber threats, capable of overwhelming cloud applications with excessive traffic. AWS Shield is a DDoS protection service that defends AWS-hosted applications by detecting and mitigating attacks automatically. Two Tiers of AWS Shield AWS Shield Standard – Free for all AWS customers, providing basic DDoS protection for EC2, CloudFront, ALB, and Route 53. AWS Shield Advanced – Premium service with enhanced DDoS mitigation, real-time attack analytics, and cost protection against attack-related scaling charges. Key Features of AWS Shield Automatic Mitigation – Blocks malicious traffic without intervention. Real-Time Attack Visibility – Provides live insights into attack traffic. AWS Global Threat Intelligence – Uses AWS’s global monitoring network for proactive defence. Route 53 and CloudFront Integration – Ensures DNS and CDN-level protection. Example: DDoS Attack Mitigation Flow AWS Shield automatically mitigates malicious DDoS attempts, ensuring application availability. Amazon GuardDuty: Threat Detection and Monitoring Amazon GuardDuty is a threat detection service that continuously analyzes AWS logs, VPC flow data, and DNS queries to identify suspicious activities. How GuardDuty Works GuardDuty leverages machine learning (ML) and threat intelligence feeds to detect: Compromised IAM credentials Malicious EC2 activity Unusual API calls Data exfiltration attempts Key Features of GuardDuty Automated Threat Detection – Uses AI/ML to identify anomalies. Low Overhead – No need for agents or additional infrastructure. Integration with AWS Security Hub – Provides centralized threat visibility. Actionable Alerts – Sends findings to AWS Lambda for automated response. Example: Detecting Unusual API Activity If an attacker gains access to an AWS account and creates unauthorized IAM users, GuardDuty generates an alert like this: { "Findings": [{ "Title": "Unauthorized IAM User Creation", "Severity": "High", "Resource": { "Type": "IAMUser", "Id": "arn:aws:iam::123456789012:user/suspicious-user" }, "Action": { "Type": "IAMUserCreate", "RemoteIP": "192.168.1.1" } }] } This information can trigger an AWS Lambda function to automatically revoke access. GuardDuty Monitoring Process: AWS WAF vs. Shield vs. GuardDuty: When to Use Each? Service Purpose Best for AWS WAF Filters HTTP traffic Protecting web applications against SQLi, XSS, and bots AWS Shield Protects against DDoS attacks Ensuring application availability against high-volume attacks Amazon GuardDuty Detects security t
As businesses migrate to the cloud, ensuring robust security against cyber threats becomes a top priority. AWS provides a multi-layered defence strategy through three key security services:
- AWS Web Application Firewall (WAF) – Protects web applications from malicious traffic.
- AWS Shield – Provides DDoS protection at different levels.
- Amazon GuardDuty – Continuously monitors AWS environments for potential security threats.
Together, these services help organizations detect, prevent, and mitigate security risks at scale, ensuring high availability and data integrity for applications running on AWS.
AWS WAF: Web Application Firewall
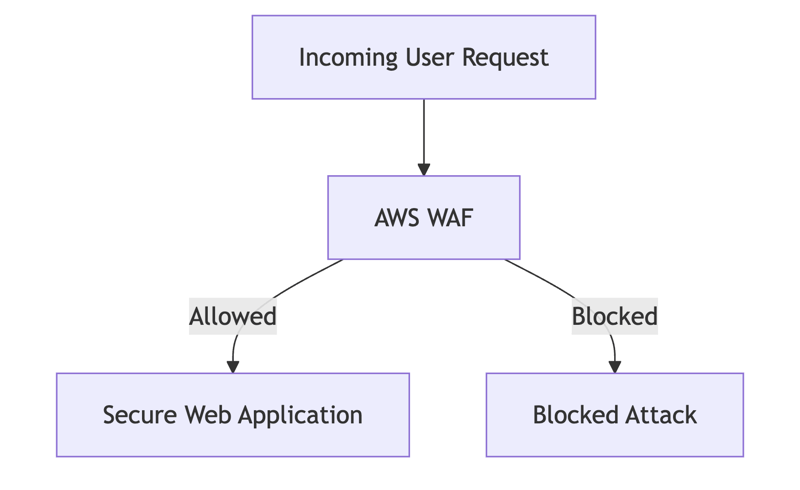
AWS WAF (Web Application Firewall) is a security layer designed to protect web applications from common attack patterns such as SQL injection (SQLi), Cross-Site Scripting (XSS), and bot-driven abuse.
How AWS WAF Works
AWS WAF filters incoming HTTP/HTTPS traffic based on custom rules that block, allow, or count requests. It is deployed alongside:
- Amazon CloudFront – To protect CDN-distributed applications.
- Application Load Balancer (ALB) – To secure applications running on EC2 instances.
- API Gateway – To prevent abuse of serverless APIs.
Key Features of AWS WAF
- Rule-Based Filtering – Users can define rules to block specific IPs, patterns, or behaviours.
- AWS Managed Rules – Pre-configured security rules for OWASP Top 10 threats.
- Rate-Based Throttling – Protects applications from brute-force and bot attacks.
- Logging & Monitoring – Integrates with Amazon CloudWatch Logs for real-time analysis.
Example: Blocking SQL Injection Attacks
AWS WAF detects malicious queries trying to exploit vulnerabilities in web applications.
{
"Name": "SQLInjectionRule",
"Priority": 1,
"Statement": {
"SqliMatchStatement": {
"FieldToMatch": { "UriPath": {} },
"TextTransformations": [{ "Priority": 0, "Type": "URL_DECODE" }]
}
},
"Action": { "Block": {} }
}
This rule blocks SQL injection attempts by inspecting the request URI path.
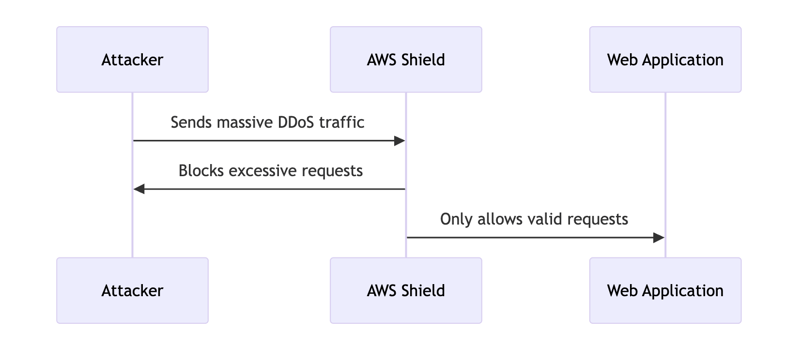
AWS Shield: DDoS Protection
Distributed Denial of Service (DDoS) attacks are among the most disruptive cyber threats, capable of overwhelming cloud applications with excessive traffic.
AWS Shield is a DDoS protection service that defends AWS-hosted applications by detecting and mitigating attacks automatically.
Two Tiers of AWS Shield
- AWS Shield Standard – Free for all AWS customers, providing basic DDoS protection for EC2, CloudFront, ALB, and Route 53.
- AWS Shield Advanced – Premium service with enhanced DDoS mitigation, real-time attack analytics, and cost protection against attack-related scaling charges.
Key Features of AWS Shield
- Automatic Mitigation – Blocks malicious traffic without intervention.
- Real-Time Attack Visibility – Provides live insights into attack traffic.
- AWS Global Threat Intelligence – Uses AWS’s global monitoring network for proactive defence.
- Route 53 and CloudFront Integration – Ensures DNS and CDN-level protection.
Example: DDoS Attack Mitigation Flow
AWS Shield automatically mitigates malicious DDoS attempts, ensuring application availability.
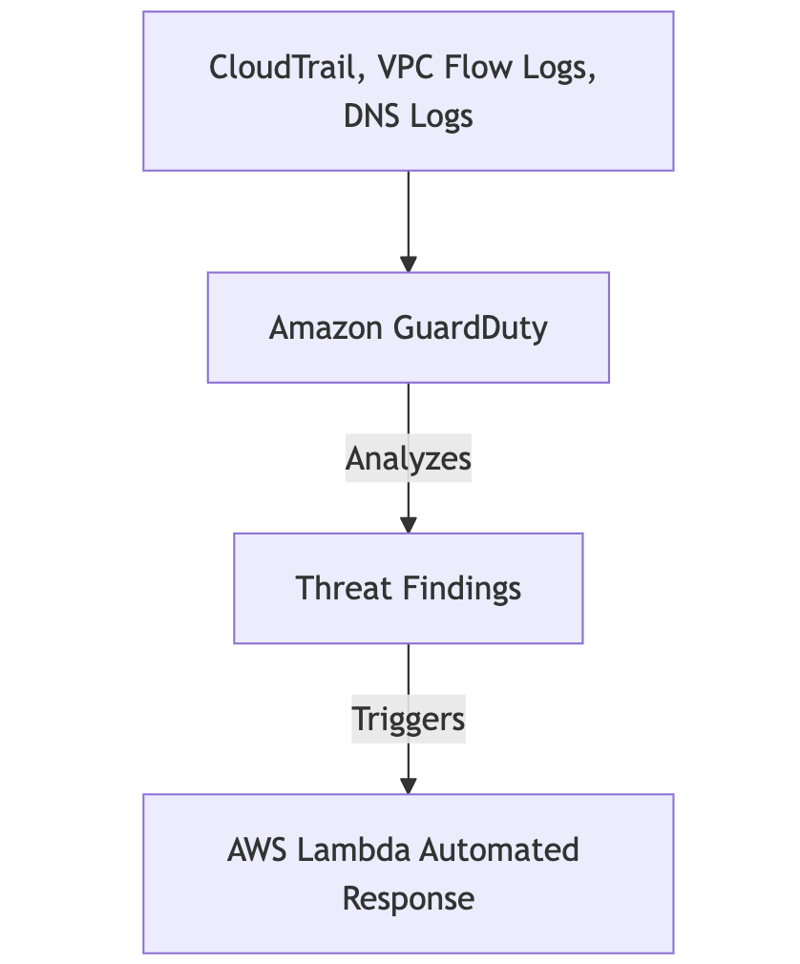
Amazon GuardDuty: Threat Detection and Monitoring
Amazon GuardDuty is a threat detection service that continuously analyzes AWS logs, VPC flow data, and DNS queries to identify suspicious activities.
How GuardDuty Works
GuardDuty leverages machine learning (ML) and threat intelligence feeds to detect:
- Compromised IAM credentials
- Malicious EC2 activity
- Unusual API calls
- Data exfiltration attempts
Key Features of GuardDuty
- Automated Threat Detection – Uses AI/ML to identify anomalies.
- Low Overhead – No need for agents or additional infrastructure.
- Integration with AWS Security Hub – Provides centralized threat visibility.
- Actionable Alerts – Sends findings to AWS Lambda for automated response.
Example: Detecting Unusual API Activity
If an attacker gains access to an AWS account and creates unauthorized IAM users, GuardDuty generates an alert like this:
{
"Findings": [{
"Title": "Unauthorized IAM User Creation",
"Severity": "High",
"Resource": {
"Type": "IAMUser",
"Id": "arn:aws:iam::123456789012:user/suspicious-user"
},
"Action": {
"Type": "IAMUserCreate",
"RemoteIP": "192.168.1.1"
}
}]
}
This information can trigger an AWS Lambda function to automatically revoke access.
GuardDuty Monitoring Process:
AWS WAF vs. Shield vs. GuardDuty: When to Use Each?
| Service | Purpose | Best for |
|---|---|---|
| AWS WAF | Filters HTTP traffic | Protecting web applications against SQLi, XSS, and bots |
| AWS Shield | Protects against DDoS attacks | Ensuring application availability against high-volume attacks |
| Amazon GuardDuty | Detects security threats | Monitoring AWS accounts, EC2, and networking activity |
Using these services together creates a comprehensive AWS security framework.
Best Practices for Security at Scale
- Enable AWS WAF Managed Rules – Protect against common threats without manual configuration.
- Use AWS Shield Advanced for Critical Apps – Mitigate sophisticated DDoS attacks.
- Activate GuardDuty – Continuously monitor AWS activity for anomalies.
- Integrate AWS Security Hub – Centralize security findings across AWS services.
- Automate Incident Response – Use AWS Lambda to react to GuardDuty findings.
Conclusion
AWS provides scalable, automated, and intelligent security solutions through AWS WAF, Shield, and GuardDuty. These services complement each other by protecting against web exploits, DDoS attacks, and security breaches.
By leveraging AWS’s security services, businesses can ensure their cloud applications remain secure, available, and resilient against modern cyber threats.
In our next article, we will explore AWS CloudWatch and CloudTrail, two critical monitoring services that provide real-time visibility, performance tracking, and audit logging for AWS resources. Stay tuned!